Seven young people arrested, including a 16-year-old teenager, for being associated with the hacker group LAPSUS $ that attacked Microsoft and Samsung

The
Seven teenagers arrested in connection with the Lapsus $ hacking group --The Verge
https://www.theverge.com/2022/3/24/22994563/lapsus-hacking-group-london-police-arrest-microsoft-nvidia
Lapsus $ suspects arrested for Microsoft, Nvidia, Okta hacks
https://www.bleepingcomputer.com/news/security/lapsus-suspects-arrested-for-microsoft-nvidia-okta-hacks/
LAPSUS $ has been active mainly in South America since around 2020, but from around 2022, it has shifted its target to international high-tech companies such as Microsoft and Samsung. According to the security-related blog Krebs on Security, LAPSUS $ uses ' social engineering ' to perform unauthorized access in many attacks. LAPSUS $'s social engineering involves tricking employees inside the target, help desks, and other stakeholders, or acquiring and bringing them into the group.
A Closer Look at the LAPSUS $ Data Extortion Group – Krebs on Security
https://krebsonsecurity.com/2022/03/a-closer-look-at-the-lapsus-data-extortion-group/
The image below is a message posted by LAPSUS $ leader 'Oklaqq' to recruit social engineering accomplices. Oklaqq is a scam called 'SIM swapping ' that hijacks the target SIM card instead of paying employees of carriers such as ATT, Verizon, and T-Mobile up to $ 20,000 a week. I'm asking you to help.
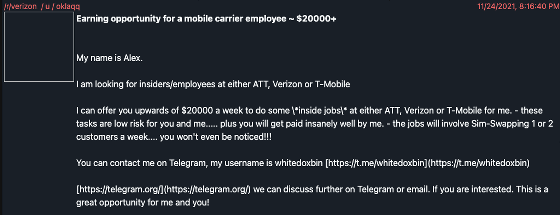
LAPSUS $ is said to have taken over the account by intercepting the target SMS and voice calls through SIM swapping, breaking through the two-step verification for resetting employees and email accounts. Many tech companies are aware of their cybersecurity, but aren't used to hacking with phone-based social engineering.
The leader of such LAPSUS $ is more likely to be a 17-year-old boy living in the United Kingdom who works under the ID 'White Doxbin' or 'Oklaqq'. This boy disclosed his real name, home address, date of birth, educational background, and private photos of himself and his family by a hacker who was hostile to the operation of a website called 'Doxbin' that discloses and shares personal information of others. However, since overseas media are underage, we refrain from reporting their real names.
A teenage suspect emerged as the central figure of the hacker group 'LAPSUS $' that hacked Microsoft etc. --GIGAZINE

The alleged father of 'White Doxbin' told the BBC in foreign media that he didn't know the boy had anything to do with LAPSUS $ and had never talked about hacking. 'My dad is familiar with computers and spends a very long time on computers.' 'I thought he was playing games. We're going to stop him from using computers. 'The father said.
Meanwhile, it was reported that the City of London Police arrested young people related to LAPSUS $. Investigator Michael O'Sullivan of the City of London Police told The Verge, a foreign media, 'The City of London Police is investigating members of the hacking group with partners. Seven people aged 16-21 are involved in the investigation. We were arrested and all were released under investigation. Our investigation is ongoing. ' It is not known if 'White Doxbin' is included in the seven people arrested this time.
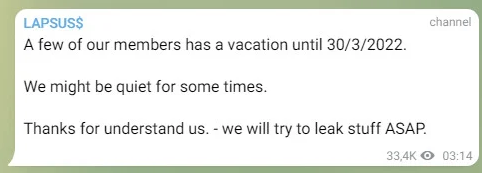
Although it is unclear whether it is related to this arrest, LAPSUS $ reported on March 23 that 'some members will take leave until March 30, 2022.'
Bill Demirkapi, a security engineer at Zoom, reports that members of LAPSUS $ posted a post boasting access to the internal development environment during a Microsoft hack. Bleeping Computer, a tech media outlet, pointed out that LAPSUS $ made some operational security mistakes and said that this lack of stuffing could have led to the identification of members.
The LAPSUS $ ransomware group appear to be incredibly inexperienced with OPSEC. They posted their message boasting about access to Microsoft's internal DevOps environment * while still exfiltrating source code *. We can tell by looking at the timestamp of the files in their leak. ?? ?? ♂️ https://t.co/NaU38cypUw pic.twitter.com/AryXJS12A1
— Bill Demirkapi @ ShmooCon (@BillDemirkapi) March 22, 2022
Related Posts:
in Security, Posted by log1h_ik






