`` Amazon and PayPal pointed out the vulnerability of account authentication but could not be opponent, '' a security researcher reported

Technical vulnerabilities caused by software and hardware, such as
Vulnerability reporting is dysfunctional
https://freedom-to-tinker.com/2020/03/25/vulnerability-reporting-is-dysfunctional/
In January 2020, Lee reported that a SIM card exchange procedure performed by a US mobile carrier was flawed, and that a ' SIM swap attack ' in which an attacker could take over a phone number or SMS was possible. At the same time, it pointed out that if the SIM swap attack succeeds, websites that use only phone numbers or SMS to verify account identities may be taken over by attackers.
Security researchers point out that there is a flaw that could leak personal information in the carrier's SIM card exchange process-GIGAZINE

After reporting the flaws in his
Among the 17 sites that Lee asked for fixes, Adobe, Snapchat, and eBay responded quickly, with a response saying they had completed the fix. However, Microsoft, Paypal, and Yahoo did not understand the threat, despite having demonstrated a SIM swap attack. In the case of PayPal, he said he rejected the point that 'SIM swap attack is a carrier problem, not a PayPal problem.' Lee said to PayPal's response that `` the carrier is responsible for taking over the phone number and SMS by SIM swap attack, but it is a website problem that account authentication can be done only with phone number and SMS ''. You.

Mr. Lee reported that he reported the vulnerability to HackerOne, a platform that can receive bounty for bug reports, but was not recognized as 'not a software bug'. Lee said of HackerOne
Ultimately, nine of the 17 sites did not fix the flaws at the time of article creation. Websites that do not fix the flaws also include payment services such as PayPal and Venmo, where security is important.
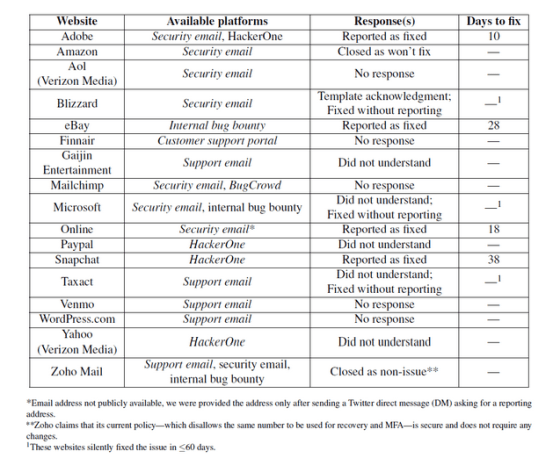
Lee points out that companies should take reporting of vulnerabilities seriously, use a model to detect such vulnerabilities, and have a direct contact for security reports.
Related Posts:
in Security, Posted by darkhorse_log