A series of multi-factor authentication attacks that issue push notifications and wait for users to make inadvertent mistakes
In addition to normal ID + password authentication, '
Current MFA Fatigue Attack Campaign Targeting Microsoft Office 365 Users --GoSecure
https://www.gosecure.net/blog/2022/02/14/current-mfa-fatigue-attack-campaign-targeting-microsoft-office-365-users/
Below is a movie demonstrating 'MFA Fatigue Attack', which sends push notifications and waits for users to make inadvertent mistakes.
MFA Attacks: Push Notification Fatigue Demonstration --YouTube
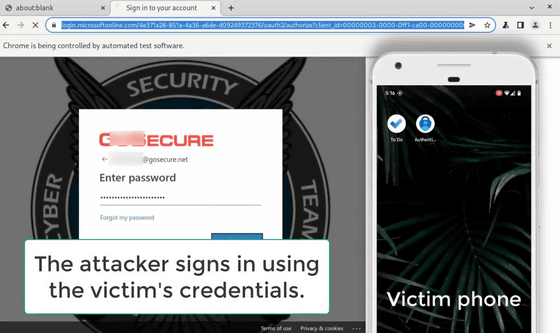
This attack focuses on the 'second stage' of multi-factor authentication, assuming that the first stage ID and password have been stolen. First, the attacker attempts to log in to Microsoft Office 365 using the stolen attack target ID and password.
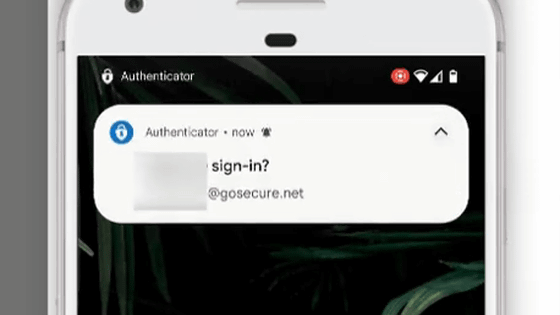
Microsoft's smartphone authentication application '
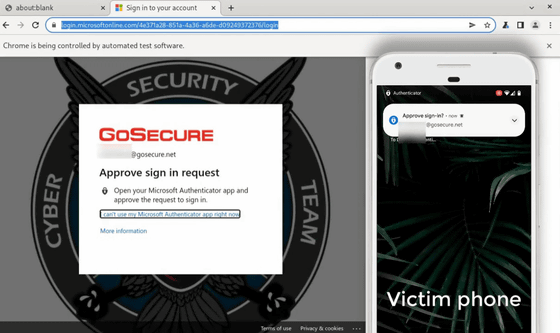
Here, the attacker is trying to log in to the Microsoft Office 365 account without permission, so the smartphone side taps 'DENY' to reject the suspicious login.
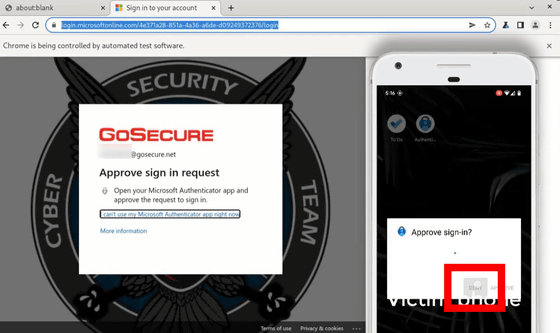
However, since Microsoft Office 365 can ask you to perform the second step authentication over and over again, it is possible to repeatedly send a notification to the smartphone side 'Please allow Microsoft Office 365 sign-in'. To. All you have to do is wait for inadvertent mistakes such as mistakes made by the user. This attack is called 'multi-factor authentication fatigue attack' because it tires the user and induces mistakes.
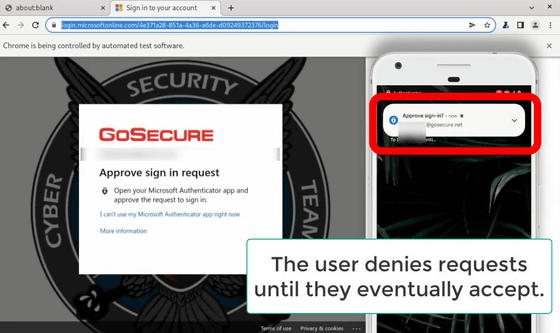
According to Go Secure, an IT security company that reported on this attack method, the number of cases of multi-factor authentication fatigue attacks has increased significantly. This attack is more of a human error attack than a security flaw, but Go Secure says, 'Most users are new to this type of attack, so either approve it without understanding it as an attack, or just get in the way. We may allow authentication in an assembly line because of the notification, 'he said, and evaluated the kind of attack that pierces human error as' particularly effective. '
Go Secure encourages Microsoft Office 365 administrators to take steps such as limiting repeated attempts for multi-factor authentication and limiting push notification authentication itself.
Related Posts: