This is the result of comparing various 'authentication methods' of the website together.

There are many websites that have a login function because they provide different data for each user. However, users shouldn't really care about the 'authentication method' of the login function installed on the website.
Web Authentication Methods Compared | TestDriven.io
https://testdriven.io/blog/web-authentication-methods/
◆ Basic authentication
Basic authentication , which is built into HTTP, is the most basic authentication method. Basic authentication does not have an encryption function, and the user ID and password encoded in Base64 are sent from the client to the server.
The authentication flow looks like this. First, the client sends an unauthenticated request to the server, which returns a 401 error. The client then submits the user ID and password to access the server.
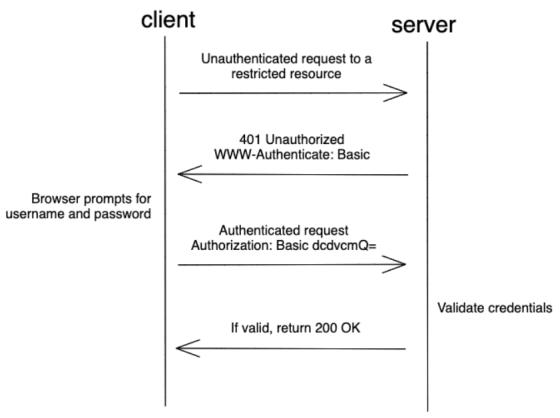
The advantages of basic authentication are that it is easy to implement and that many browsers support it. On the other hand, the disadvantages are that it does not support encryption and that it is necessary to authenticate each time a request is made.
◆ Digest authentication
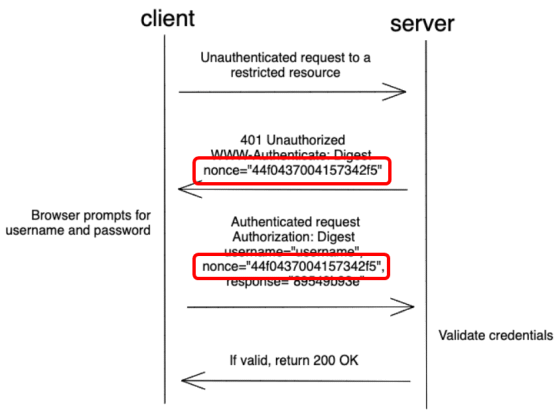
In addition to the advantages of basic authentication, Digest authentication has the advantage of improving security by hashing MD5. However, the point that it is necessary to authenticate for each request is the same as basic authentication, and since the user ID and password on the server side are stored in plain text, the security on the server side is inferior to basic authentication. It is also described as vulnerable to
◆ Session-based authentication
Session-based authentication is an authentication method that uses cookies, and unlike basic authentication and Digest authentication, it is not necessary to send and receive a user ID and password for each request. As an authentication flow, the client first sends the authentication information to the server, and if it is correctly authenticated on the server side, a session is generated on the server side. The server sends a session cookie to the client, and the client can access the server as long as it sends a request with that cookie.
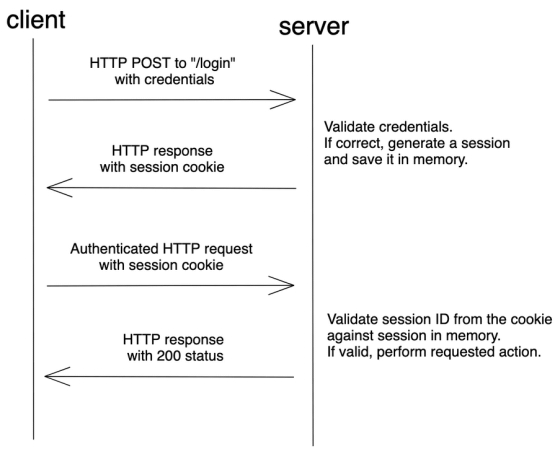
The advantage of session-based authentication is that the processing after login is fast because it is not necessary to send the authentication information for each request. Another advantage is that it is easy to implement due to the existence of abundant frameworks. Disadvantages are that the authentication information is retained on the server side, it is necessary to send a cookie for each request even if authentication is not required, and there is a weakness in
◆ Token-based authentication
Token-based authentication uses tokens instead of the cookies used in session-based authentication earlier. The token is signed with the server's private key, and the client sends a request with the token received from the server, which is an authentication flow. The server only needs to check if the signature is correct, so there is no need to keep the authentication information on the server side.
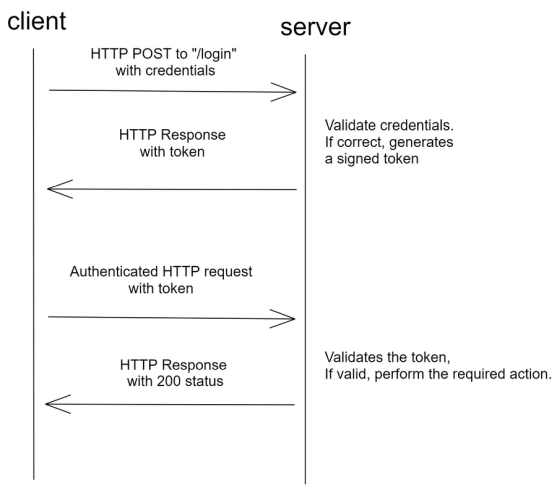
Shaji explained that token-based authentication is a stateless authentication method that does not hold authentication information on the server side, so high-speed communication can be realized. It goes well with microservices .
The disadvantages of token-based authentication are that depending on the client's information retention method, it may be damaged by cross-site scripting or cross-site request forgery, and tokens cannot be deleted until the expiration date, so if the token is used, Shaji says there are points that an attacker can exploit if leaked.
◆ One-time password
A one-time password issues a password that can be used only once when logging in. One-time passwords are characterized by the fact that one layer of security can be added by using a reliable system such as an email address and phone number that can be used only by the account owner. It has the advantage of high security so that it can be used for online banking, but it also has the disadvantage of not being able to authenticate if a reliable system becomes unavailable due to a malfunction or dead battery.

◆ OAuth / OpenID
Authentication protocol standards such as OAuth and OpenID have an authentication function such as 'who is the client' and an authority management function such as 'what to allow the client'. In addition, it is also possible to implement a login function using SNS accounts such as Google, Twitter, Facebook, etc., and it is possible to realize high security without holding a password.
As the advantages of authentication by OAuth and OpenID, Mr. Shaji listed that it is harmless even if it is attacked by a third party because it has high security, there is no need to create a new account, and it does not have a password. Disadvantages include the fact that some parts rely on other systems, the confirmation of authority is easily overlooked by users, and the fact that it cannot be used by people who do not have an SNS account.
Shaji also said that the following criteria should be followed when deciding which authentication method to use.
-Applications that use server-side templates: Session-based authentication. You can also add OAuth or OpenID
-REST API : Token-based authentication
・ When handling highly confidential information: Add a one-time password
Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log