Password management tool "1Password" may steal personal information from plaintext metadata

Popular as a password management tool1 PasswordIt is pointed out that there is a vulnerability in the Agile Keychain for management of metadata adopted by the user that privacy information of users may be peeked at by a third party depending on conditions.
1 Password Leaks Your Data
http://myers.io/2015/10/22/1password-leaks-your-data/
Dale Myers, a Microsoft software engineer, found a vulnerability that could cause personal data to leak out while using the password management tool "1 Password".
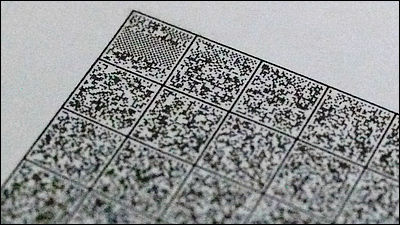
According to Mr. Myers, there is a file named "1Password.html" in ".agilekeychain" file of "Agile Keychain" which 1Password incorporates as data storage format. When accessing this file via HTTP, a gray page is opened and when you enter a password on the password entry screen, you can browse the data you save.
Under this mechanism, anyone who knows the link URL of the user's keychain page can access the file "1Password.agilekeychain / data / default / contents.js" by modifying the link, within this file The site information managed by 1 Password is saved as meta data in plain text not encrypted. Therefore, if you access metadata in the file, it seems that the service of what service the user is storing will be naked.
ByBlake Patterson
さらに都合が悪いことに、1Passwordでは、ログイン場所がキーチェーンにエントリーされる仕組みが採られているとのこと。例えば、「https://example.com/login」にサインインした場合、このリンクがキーチェーンのエントリーに保存されるそうです。
Mr. Myers said that it was necessary to reset the password due to a security bug of the ISP used by himself, but the URL link for reset sent by e-mail for password reset is used once It is in a state that it is still activated even after you reset your password, and it seems that it was in a state where you can reset the password again by clicking the link URL again after resetting the password. According to Mr. Myers, although this is a setting error on the ISP side, such a mistake is not uncommon.
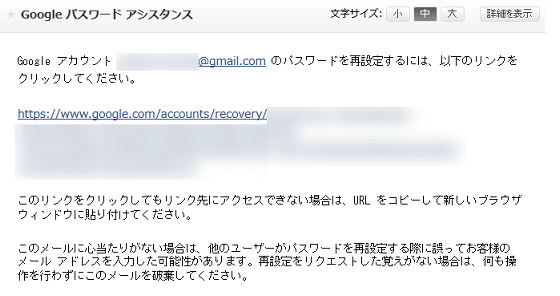
In the case where it is possible to step through the password link again as described above, since 1 Password stores not only the authentication information but also the password link page as the metadata, the third party can access the password change link which is the plaintext data That is why if you reset your password from the password link you will be deprived of access.
Mr. Myers reported to the AgileBits offering 1Password about the vulnerability described above and found that he got the answer "I recognize this vulnerability but it is a specification". Several years ago when 1Password's Agile Keychain was developed, encrypting up to metadata will decrypt all metadata when accessing the data and then retrieve the necessary data, which is heavy It seems that the specification that such metadata is not encrypted becomes adopted because it becomes.
Unless 1Password changes the current system, in order to prevent leakage of information such as services to be used, if you do not manage carefully that the link URL of the user's keychain page is not known to a third party I do not seem to get it.
Related Posts: