Okta announces that a flaw that allowed users to log in without a password if their username was 52 characters or longer had existed for three months

Okta AD/LDAP Delegated Authentication - Username Above 52 Characters Security Advisory
https://trust.okta.com/security-advisories/okta-ad-ldap-delegated-authentication-username/
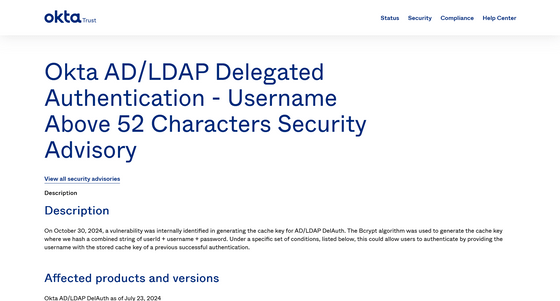
On November 1, 2024, Okta reported that its delegated authentication system, Okta AD/LDAP DelAuth, had a vulnerability that allowed users to log in to their accounts without entering the correct password.
According to Okta's security advisory, if a username is 52 characters or longer and the user has a history of successful authentication in the past, the stored cache key can be used to authenticate the user.

An algorithm called
This could have allowed users to authenticate using a stored cached key if the AD/LDAP agent was down or experiencing too much traffic.
The issue could be circumvented if multi-factor authentication (MFA) was used, but the flaw remained in the system from July 23 to October 30, 2024.
Okta discovered the vulnerability on October 30th and addressed the issue the same day by switching its encryption algorithm from Bcrypt to PBKDF2 .
Okta said customers should 'examine their system logs for unexpected authentications with usernames longer than 52 characters between July 23 and October 30, 2024,' and recommended setting up multi-factor authentication and using phishing-resistant authentication systems.
Related Posts:
in Security, Posted by log1l_ks







