What is the current state of "click jacking" and how to deal with placing transparent buttons to cheat users?

ByDave Dugdale
One of the attack methods on the Web is to trick users visually and click on malicious icons or link destinations by placing transparent buttons or invisible layers on the pageClick Jacking"there is. On the web page, with regard to the current status of attacks to be embedded using the general 'iframe' tag and the way of dealing with it,@ filtereded scriptorMr. is summarizing the information.
Google YOLO
https://blog.innerht.ml/google-yolo/
A typical example of Click Jacking is the structure of a page like the following. This page reproduces the page of online banking transaction using "iframe" tag, under the button written as purple "Harmless Button", "Transfer everything to my Nigerian account! (Transfer the whole amount to Nigerian account!) "Hidden button is set up.
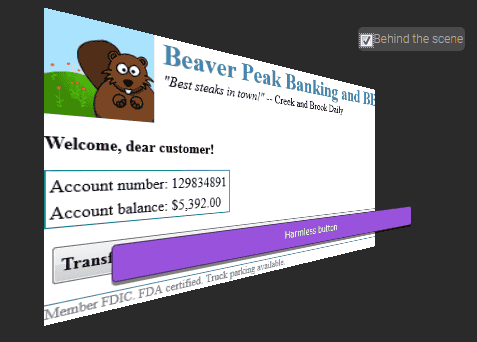
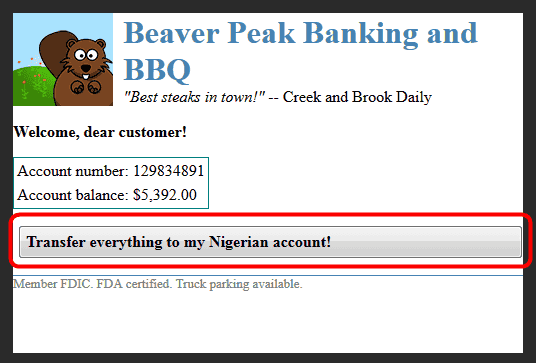
When filling in such click jacking, you can display an element (= button) on the front of the page using the "position" property of the CSS, and specify the "pointer-events" property, A mechanism is used to let the arranged elements pass through and click on malicious buttons arranged so as not to be seen on the back. In the case of this dummy page, the user who clicked on thinking that it is "harmless button" will lead to the situation that money will be remitted to the fraudulent account of Nigeria unnoticed.
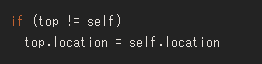
To avoid this problem, it is most effective to completely ban an iframe, but this method is not very realistic. Therefore, "frame busting" script using JavaScript may be used. This is a way to prevent the attacker from loading the website into the embedded iframe, and attempts to detect whether the page will be read using the script as shown below. When it is detected, reading of the page is blocked, so it is possible to avoid click jacking problems.
However, there is a countermeasure called "busting / frame busting" which invalidates "frame busting". This is to invalidate JavaScript for frame busting by exploiting the XSS Filter function installed in the browser. There are many cases where "onBeforeUnload" and "sandbox" are exploited in this case, and there are certain limits also in coping with JavaScript.
To avoid this problem, it is provided by Google's widget "One tap sign-up" and "automatic sign-in" mechanism "YOLO (You Only Login Once)". By embedding iframe tags generated by Google inside the website, users can log in with a single click using their Google account.
One-tap sign-up and auto sign-in on websites | Google Developers
https://developers.google.com/identity/one-tap/web/
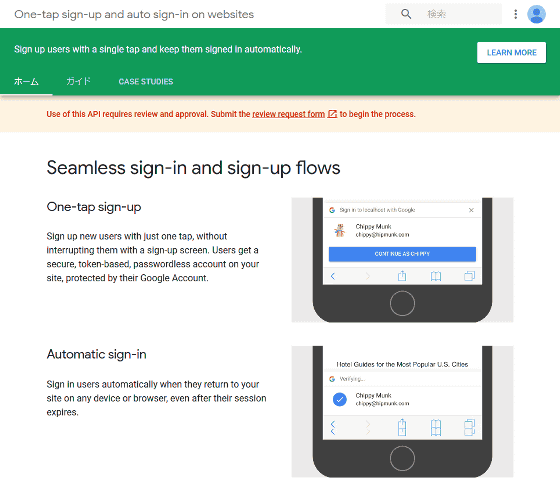
However, when using YOLO to try logging in with a Google account, information such as e-mail address, visitor's name, profile image, etc. will be sent as follows. As for this matter, Google decides that it is "as specified" as "necessary for providing widgets".

In this way, there are both advantages and disadvantages to coping with click jacking, and there is no way to say that there is no sure way. As a way to lower the risk, the following are mentioned.
· Include "X - Frame - Options" or "Content - Security - Policy" in the header part of the page
· Web widget providers should ensure that sufficient user interaction is required
· Consider disabling third party cookies on the user side
· Use browser profile
Related Posts: