Polymorphic attacks allow malicious extensions to pose as password managers and steal sensitive information
Cybersecurity firm
Polymorphic Extensions: The Sneaky Extension That Can Impersonate Any Browser Extension | by SquareX | Mar, 2025 | SquareX Labs
https://labs.sqrx.com/polymorphic-extensions-dd2310006e04
Malicious Chrome extensions can spoof password managers in new attack
https://www.bleepingcomputer.com/news/security/malicious-chrome-extensions-can-spoof-password-managers-in-new-attack/
SquareX has released a video demonstrating what a 'polymorphic attack' looks like.
Polymorphic Extensions: The Sneaky Extension That Can Impersonate Any Browser Extension - YouTube
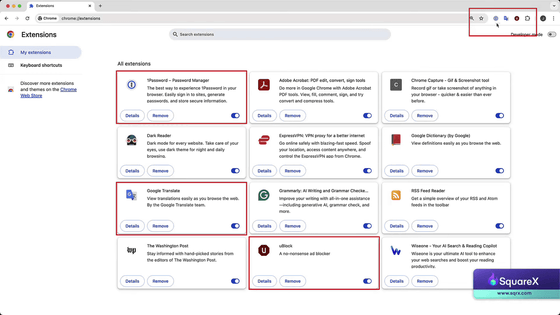
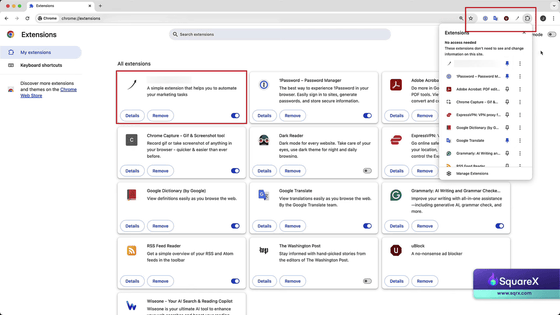
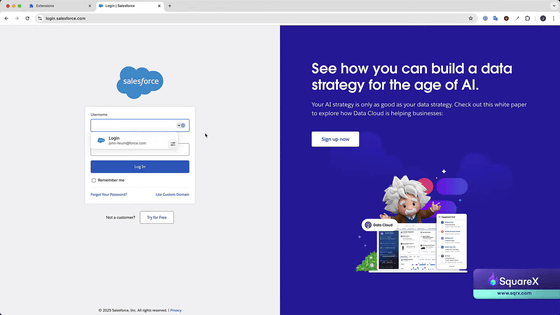
Chrome at the start of the experiment. The three extensions pinned to the toolbar were '1Password,' 'Google Translate,' and 'uBlock.'
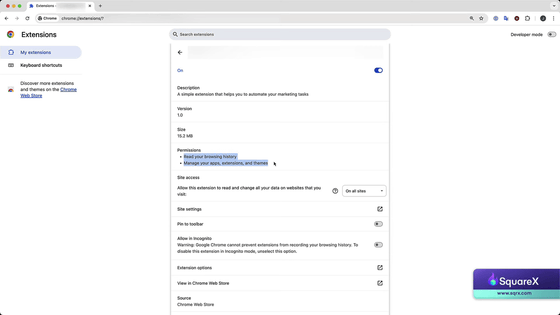
We are adding a new AI marketing tool extension.
The permissions for this extension are 'Read browser history' and 'Manage apps, extensions, and themes.'
Add this extension to your toolbar as well.
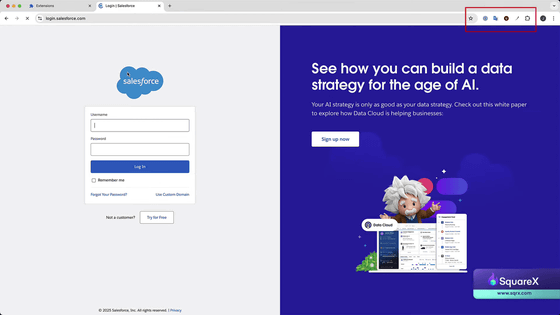
I have come to a site that requires me to log in.
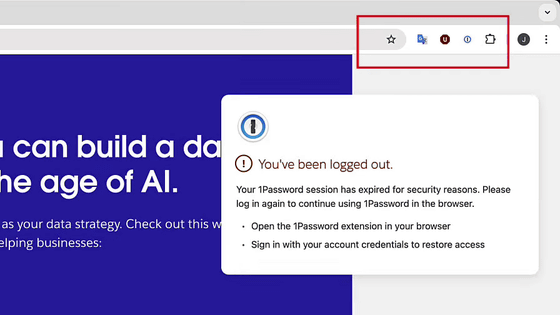
Then, a pop-up message appears saying that '1Password' has been logged out.
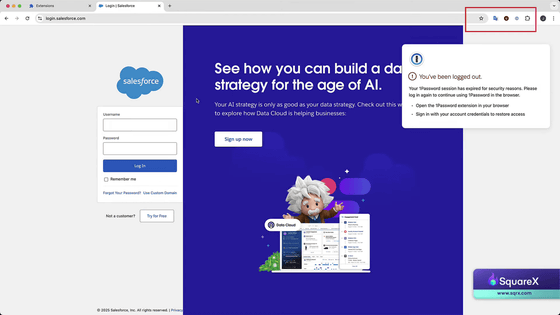
If you check closely what the toolbar looks like at this time, it will be normal as shown here when you access it.
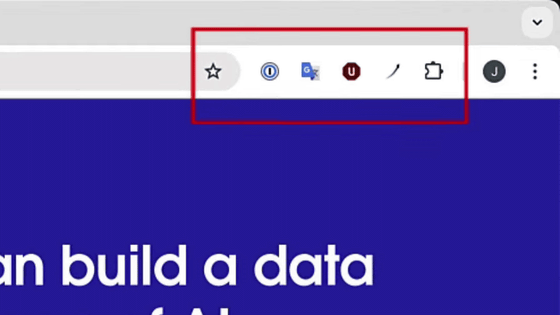
However, the '1Password' on the far left disappears.
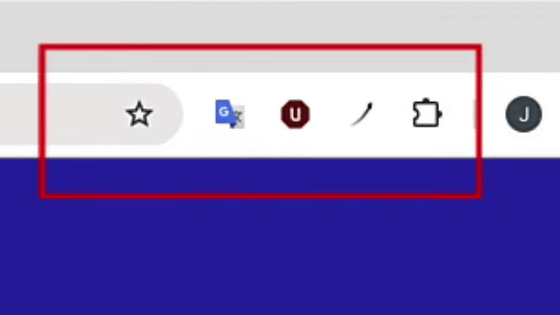
The icon of the AI marketing tool changed to that of 1Password, and a pop-up appeared. This pop-up was not from 1Password, but a fake one.
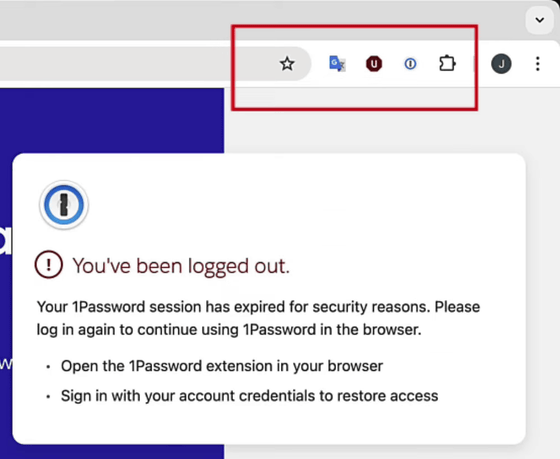
Next, a form appears asking me to log in to 1Password, which is also fake, of course.
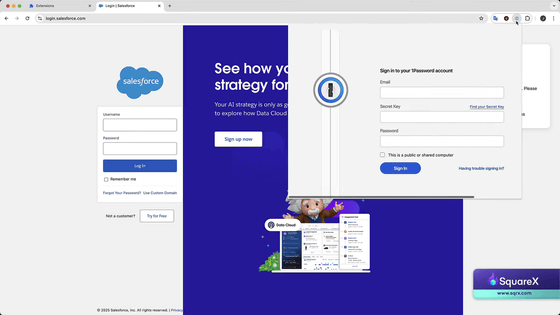
Enter the required information and sign in.
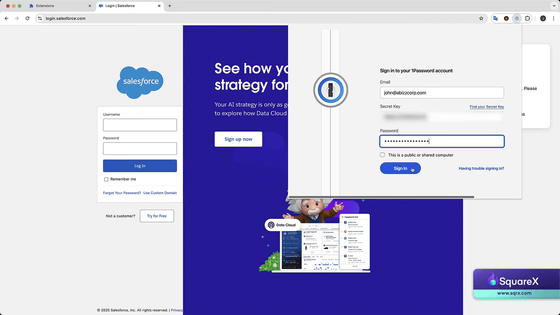
The login information is then suggested, as if you had logged out of 1Password and logged back in, but in reality the malicious extension had just temporarily disabled the legitimate extension, meaning any information you entered into the fake form would be stolen.
As SquareX describes the attack as ' polymorphic ,' this demonstration video is just one pattern. Malicious extensions find extensions to impersonate by abusing the ' chrome.management API ' used for extension management, or by using a technique called 'web resource hitting' to detect resources specific to the targeted extension. Therefore, the target is not limited to '1Password.'
In addition, the impact is quite widespread, covering not only Chrome but also all Chromium-based browsers, including Microsoft Edge.
SquareX has contacted the Chrome team about the attack as a form of 'responsible disclosure,' but says that the attack cannot be addressed with a patch and can only be addressed with a browser-native solution that understands the runtime behavior of each extension.
Related Posts: