Google · Facebook · Yahoo! A method to break through 2-step verification such as
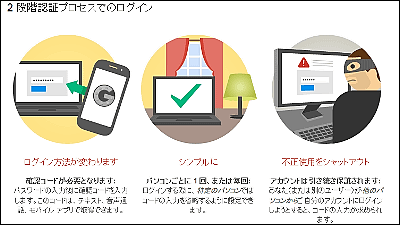
To reduce the risk of unauthorized access to your account, Google, Facobook, Yahoo! Services have introduced a system called 2-step authentication. 2-step verification is a function that can be set to input the authentication code sent to the registered device in addition to the account name and password when logging into the account, boasting robust security .... However, A man living in Australia broke through this 2-step certification in an unexpected way and released its details.
How I bypassed 2 - Factor - Authentication on Google, Facebook, Yahoo, LinkedIn, and many others.
http://www.shubh.am/how-i-bypassed-2-factor-authentication-on-google-yahoo-linkedin-and-many-others/
"There are a variety of breakthrough methods for 2-step verification, such as do brute force attacks or steal two-step authentication tokens somehow, but most of them have already been addressed," said security research Shubham Shah of the person. Shah mentioned voicemail which may be used for authentication as a weak point that it surely break through 2-step verification.
In 2-step verification, when you log in, you enter the account name and password, the authentication code is sent to the registered device, and the user must input it to login the authentication code. I normally receive an authentication code with a short message or voicemail, but the method discovered by Shah is to steal the authentication code sent by voicemail.
ByTony Webster
In order to carry out 2 step verification breakthrough method found by Shah, "target account name and password" "mobile phone number registered for 2-step authentication" "caller phone number camouflage service" "for carrier voicemail The telephone number of "four" is required. Caller phone number Impersonation serviceSpoofCardAlthough it is a net service such as a net service, it is charged, but if you register, you can display a fake number on the other party's device when you make a phone call.
After preparing the above 4, breakthrough start of 2 step certification. First, log in to the target 2-step authentication set account. After entering the account name and password, options such as sending shortcut authentication code for 2-step verification or sending by phone are displayed. In the meantime, call the target mobile phone registered for two-step authentication, confirm that the target mobile phone is receiving a call, select "Send authentication code by phone" and execute it. Then, since the target mobile phone is in a call, the authentication code is stored in the target voice mail.

ByJonas Seaman
After the authentication code is stored in the voicemail, we only use the caller phone number impersonation service to hear the authentication code. Call from the service such as SpoofCard to call "+610411000321" to display "target phone number" OK. With this, you can access voicemail where the target authentication code was recorded and you can get it safely. Here, "+610411000321" is the case of the carrier Shah tried, this is a number that can not be connected from a fixed phone, but it is prepared so that users can check voicemail from overseas There is a dedicated number.
However, the method described above is applicable when the target mobile phone line is on the left side of the image below "Live Connected"DodoWhen it was such as "Telstra"VodafoneIt is difficult if you contract with. Shah has only tried it in Australia, but the method of extracting the authentication code from voicemail is based on the British "3"EEIt seems possible even with a mobile phone contracted with. Meanwhile, in the United States, it is difficult to listen to voicemail because you may be asked to enter a PIN number.

Shah tried a method of stealing the authentication code using the caller telephone number impersonation service, but Google, Facebook, Yahoo! · Success with LinkedIn. After that, when informing that the security team of each service is vulnerable to 2-step verification, Facebook and LinkedIn immediately canceled "transmission of authentication code by telephone", but Google and Yahoo! It is said that it is left unattended.
Security researcher Shah gathered not only the career in Australia but also the information on "overseas carriers are set up so that users need to enter a personal identification number when listening to voicemail" , We are disclosing a list of "some phone numbers for accessing voicemail from counterfeit phone number calling service" of some of the carriers outside of Australia. NTT DoCoMo in Japan was included in the public list.
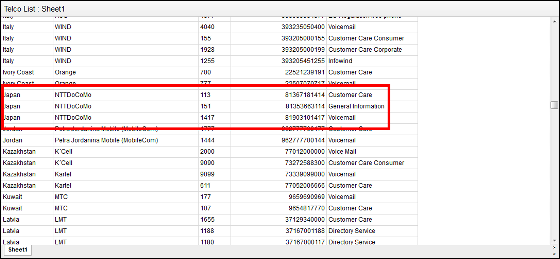
Shah says "This vulnerability has problems with carriers that make it possible to listen to voicemail without a PIN number than a service that sets 2-step verification." Also in JapanLINE phone, It turned out that the caller's phone number can be disguised, and LINESecurity updateWe are doing on April 28, 2014, but "I can call using a canceled phone numberThe phenomenon has just been confirmed. The method discovered by Shah is also a key to forgery of the caller's phone number, and a fundamental countermeasure against net service and career against such vulnerability is required.
Related Posts:
in Web Service, Posted by darkhorse_log