``Companies that use SMS for account login and password reset should be held responsible for SIM swap attacks''

Companies like Apple, Google, and Dropbox use
Companies embracing SMS for account logins should be blamed for SIM-swap attacks – Key Discussions
https://keydiscussions.com/2024/02/05/sim-swap-attacks-can-be-blamed-on-companies-embracing-sms-based-password-resets/

A SIM swap attack is a fraudulent method that uses the victim's personal information obtained through
In the United States, the number portability (LNP) system makes it easy to transfer SIM cards, so there is no end to SIM swap attacks. In fact, Dailey reports that the number of articles about SIM swap attacks reported on Techmeme is enormous.
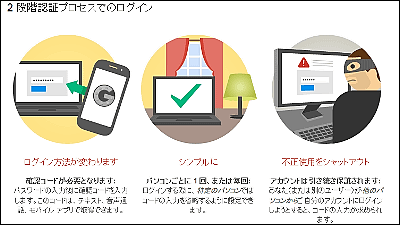
The methods to prevent SIM swap attacks are very simple, and include ``prohibiting login via SMS'' and ``prohibiting password reset via SMS.'' Also, if you need to use two-factor authentication using SMS, Dailey says it's important to implement a secure two-factor authentication option like
Regarding two-factor authentication using SMS, Dailey said, ``Sending an SMS to a customer is like sending a postcard. They are unencrypted, so-called 'plain text,' and anyone can intercept them. 'This protocol was not designed to be highly secure in the first place.' ``SMS-based login is unlikely to be a good thing in the future,'' he says harshly.
When a SIM swap attack occurs, most of the anger from victims is directed at the carrier. In fact, carriers may be subject to legal liability for failing to properly protect their customers' phone numbers. However, Dailey points out that ``companies such as Apple and Google that use these vulnerable carrier systems to provide SMS-based password reset and login options are also responsible.'' .

The option of incorporating SMS into the authentication flow, which was started by a few companies due to its ease of use, gradually spread to competitors. According to Dailey, two-factor authentication can be further strengthened by introducing protocols like
Dailey gives examples of companies implementing two-factor authentication via SMS.
・Apple
In 2018, Apple introduced a feature that allows you to automatically enter one-time codes from SMS received on your iPhone. It also provides an option to reset your Apple account using SMS.
Similar to Apple, Google introduced the ability to autofill one-time codes to Android in 2019.
・Cloud providers such as Amazon, Microsoft, and Google
By issuing one-time codes and sending them via SMS, providers such as AWS, Azure, and Google Cloud receive incentives. Therefore, these companies sell their one-time code sending technology via SMS as a 'secure solution'.
・Fund management service
Fund management services such as PayPal also provide account login and password reset functions using SMS.
・Other companies
A wide variety of companies, from food ordering services to social media to data storage companies like Dropbox, are implementing SMS logins and password resets. Of course, with these services, it is not possible to turn off the SMS system.
``Technology companies are constantly exposing their customers to SIM swap attacks, even though it is the technology company's job, not the customer's, to determine whether their systems are secure,'' Dailey said. Furthermore, he urges companies to ``address this situation to society and abolish support for SMS authentication services.'' “Hopefully, with more lawsuits and new laws, this will change,” Dailey said.

Related Posts:
in Web Service, Security, Posted by log1r_ut