The U.S. Securities and Exchange Commission posted a fake Bitcoin approval on SNS due to hacking by 'SIM swap attack'

The U.S. Securities and Exchange Commission (SEC) announced on January 22, 2024 that the commission's X (formerly Twitter) account was hijacked by someone due to
SEC.gov | SECGov X Account
https://www.sec.gov/secgov-x-account
SEC confirms X account was hacked in SIM swapping attack
https://www.bleepingcomputer.com/news/security/sec-confirms-x-account-was-hacked-in-sim-swapping-attack/
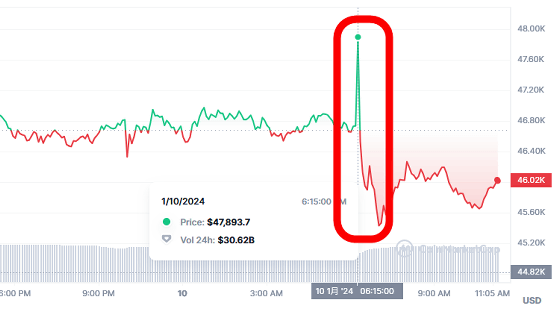
On January 10, 2024, an issue occurred where the SEC's X account falsely announced that it had approved a Bitcoin spot ETF, causing the price of Bitcoin to skyrocket. Ironically, shortly after that, the SEC officially approved Bitcoin ETFs.
A situation occurred where the U.S. Securities and Exchange Commission hijacked the X account and posted that ``Bitcoin ETFs are allowed to be listed'' & the price of Bitcoin soared immediately after posting - GIGAZINE

On January 22nd, the SEC, which had been investigating the cause in cooperation with related agencies such as the FBI, stated, ``Two days after the incident, after consulting with telecommunications carriers, we found that it was a ``SIM swap attack'' that was clearly caused by an unauthorized person.'' 'The SEC has determined that the SEC has obtained control of the SEC's mobile phone number associated with this account.'
A SIM swap attack is a technique that uses the victim's personal information obtained through phishing to trick telecommunications carriers into swapping the victim's SIM card with the attacker's SIM card. Once the attacker obtains the victim's SIM card, the attacker can bypass two-step authentication through calls and text messages using the phone number, and take over the victim's SNS accounts and online banking accounts.
According to the SEC, this SIM swap attack was not carried out through the SEC's system, but by deceiving carriers. As a result, no evidence of unauthorized access to SEC's internal systems, data, or other SNS accounts has been found to date.

The SEC said it continues to work with law enforcement to investigate how attackers used carriers to conduct SIM swap attacks. The SEC also found that the X account in question did not have multi-factor authentication enabled, as it had asked X's support center to disable multi-factor authentication when it encountered problems logging into the account. I revealed it. In addition, at the time of writing the article, multi-factor authentication is enabled on all SNS accounts held by the SEC.
However, once a SIM swap attack is successful, the hacker now has access to the one-time passcode sent to the phone number, allowing them to compromise the X account even if multi-factor authentication is enabled. IT news site BleepingComputer points out that it was possible.
As a measure to prevent similar damage, BleepingComputer says, ``If you set up an authentication app to use an authentication app, the attacker will not be able to log into your account even after you change your password.'' Therefore, it is always recommended to use only authenticator apps or hardware security keys for multi-factor authentication, rather than SMS.'
Related Posts:
in Security, Posted by log1l_ks