It's possible to hack a car using JavaScript

Engineer and author Charlie Gerard reports that he successfully hacked a car using JavaScript and
Hacking cars in JavaScript (Running replay attacks in the browser with the HackRF) | Charlie Gerard | Senior frontend developer & Creative Technologist Charlie Gerard | Senior frontend developer & Creative Technologist
https://charliegerard.dev/blog/replay-attacks-javascript-hackrf/
Using a HackRF and JavaScript Browser App to Perform Rolljam Replay Attacks on a Car
https://www.rtl-sdr.com/using-a-hackrf-and-javascript-browser-app-to-perform-rolljam-replay-attacks-on-a-car/
A few years ago, Gerald tried to capture raw data of passing aircraft using a PC-based radio receiver (RTL-SDR).
Wanting to use SDR more, Gerald got a HackRF One that can send and receive data. He downloaded Universal Radio Hacker and touched it, thinking, 'I wonder if a similar tool can be realized with a web browser and JavaScript,' and finally challenged himself to 'hack a car with JavaScript.'
The experiment is briefly summarized in the one-minute video below.
Hacking my friend's car using JavaScript - YouTube
A friend's car was provided for this experiment. The doors were locked.

The necessary equipment, including a laptop and HackRF One, was prepared on the hood of the car.

First, we need to make it possible to receive the frequency used by car keys. Gerald wrote code using

Then, he put the device into receive mode and operated the car key. The recording function of

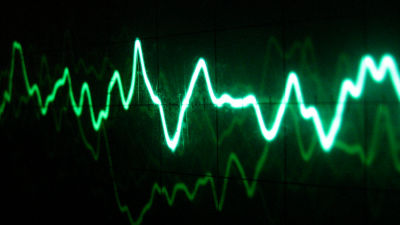
The signal itself was being transmitted, so I was able to successfully receive it on my device. I used the Canvas API to visualize the signal.
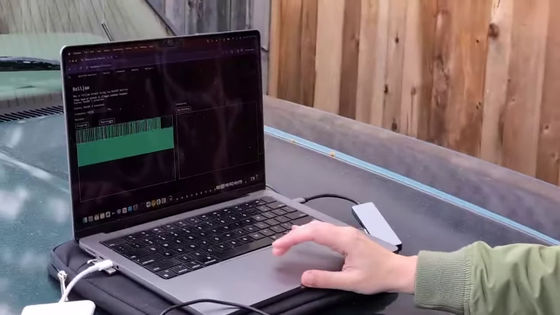
Again using the WebUSB API, we load the signals we saved to a local file and transmit them on the HackRF One. To make sure it's working properly, we use the Canvas API to import the data and visualize what the signals look like.
You will hear a beep and the car will be unlocked. This entire process is accomplished using only a web browser, plain JavaScript, and the browser API.

In the past, the signal sent from KeyFab was always the same code, but since 1995, it has been a 'rolling code' method that alternates between codes from a list. In the middle of the experiment, Gerard interfered with the car's reception of the KeyFab signal in order to perform a roll jam attack from the browser, which 'interferes with the car's receiver from receiving the signal, allowing the attacker to obtain and use the signal instead.'
'Overall it was a fun project and really exciting to demonstrate that it's possible to hack a car using JavaScript,' Gerard said.
Related Posts: