Developed hacking machine that steals secret key by measuring electromagnetic waves generated from PC with only inexpensive parts on the market

RSACryptography is widely used in the Internet, e-mail, etc. as a means to safely protect data from strong security. However, it became clear that a hacking method called "steal RSA secret key by measuring electromagnetic waves generated from PC" has been devised, making it possible to create a hacking device that can easily intercept secret keys by combining commercially available parts It is.
Stealing Keys from PCs using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation (extended version) - radioexp.pdf
(PDF file)http://www.cs.tau.ac.il/%7Etromer/papers/radioexp.pdf
Stealing Keys from PCs using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation
http://www.tau.ac.il/~tromer/radioexp/
In order to decrypt the encrypted data, an attack method for indirectly stealing the key for decryption by physically examining the operation state of the encrypting device is "Side channel attack"Israeli researchers pointed out the dangers of measuring the potential state of the PC and extracting the secret key of the RSA cipher already.
New hacking method to decrypt encrypted data from potential change of PC appeared - GIGAZINE

The research team of Professor Daniel Jenkin of Tel-Aviv University who devised this potential analysis side-channel attack further refined the method and made it possible to easily and inexpensively obtain the parts that can be obtained without using exclusively designed and expensive equipment By combining,Medium waveHas announced that it succeeded in the development of a device which eavesdrops on the secret key by using it.
This is the state of the experiment of eavesdropping using medium wave. In order to eavesdrop on the secret key of the RSA cipher from the left PC, attaching the SDR receiver to the notebook PC (right) from a distance of about 50 cm away Receiving radio waves by holding the loop antenna of 15 cm in diameter.

Cryptographic softwareGnuPGThe research team succeeded in stealing the secret key by recording and analyzing the fluctuation of the electromagnetic wave generated from the notebook PC when decoding it.
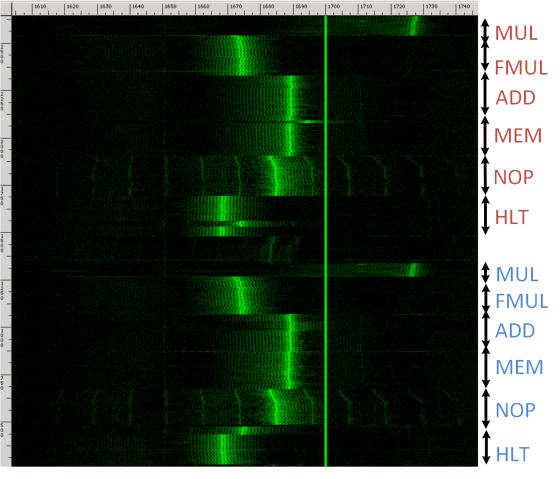
According to Professor Jenkin and others, most PCs emit different electromagnetic waves when computing with the CPU, it is possible to extract the secret key by analyzing the spectrogram by receiving the electromagnetic wave being decrypted. The vulnerability that was eavesdropped in version 1.4.19 of GnuPG used in the verification experiment seems to have been corrected promptly after the research was announced.
Furthermore, the research team of Professor Jenkin et al.Rikomagic MK802 IVThe Android terminal and SDR receiver were combined to develop a hacking device "Portable Instrument for Trace Acquisition (PITA)" which can extract secret key without PC. This is the PITA used in the experiment, each of which is made up of inexpensive parts marketed.
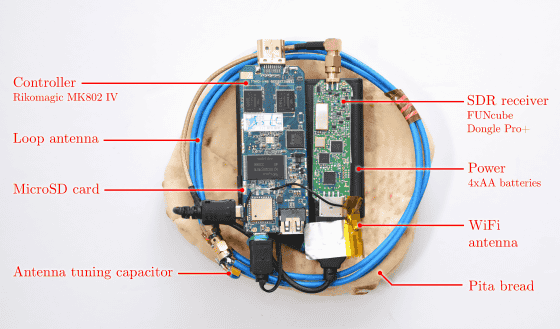
By getting close to the PC you want to wiretap antennas like this, we have successfully intercepted the radio waves and extract the encryption key.

PITA which can be manufactured cheaply but the research team who was dissatisfied with the necessity of the SDR receiver focused on the fact that the radio wave to be intercepted by eavesdropping is a frequency band close to 1.7 MHz which is relatively close to AM radio, portable radio Also developed a device using the receiver. smartphoneHTC EVOIt has also succeeded in stealing a secret key by connecting with.

Since the hacking attack by PITA only runs at a distance close to the target PC, the danger of being abused in real life seems unlikely. Moreover, it can be said that it is possible to combat hacking behavior by mixing dummy electromagnetic waves at the time of decryption of RSA encryption.

Related Posts:






