New hacking method for decrypting encrypted data from potential change of PC appears

ByCharis Tsevis
In order to decrypt the encrypted data, an attack method for indirectly stealing the key for decryption by physically examining the operation state of the encrypting device is "Side channel attackIt is called. Various methods are developed for side-channel attacks "By measuring the potential state of the PCRSA encryptionI steal the secret key of "The attack method was devised.
Get Your Hands Off My Laptop
http://www.cs.tau.ac.il/~tromer/handsoff/
Touching a Laptop Can Break Its Encryption | MIT Technology Review
http://www.technologyreview.com/news/530251/how-to-break-cryptography-with-your-bare-hands/
Side channel attacks came to be known in 1996 when Paul C. Cochel proposed a method to analyze secret keys using the fact that the processing time of public key cryptography depends on the bit pattern of secret key In the hacking method, for example, since the power consumption of the IC card has relevance to the processing content, "power analysis attack" in which power consumption is measured and the information is extracted, and processing contents And "acoustic analysis attack" that guesses the effect of "sound analysis attack" has been devised so far.
Meanwhile, researchers at the University of Tel Aviv in Israel have announced a new side-channel attack that steals the secret key of the RSA cipher by measuring the potential change of the PC enclosure.
This new side channel attack is based on the phenomenon that ground potential (ground voltage) fluctuates when the computer carries out calculation. Since this potential change also occurs when the encryption software decrypts the encrypted data, we try to steal keys by measuring the ground potential during decryption processing.
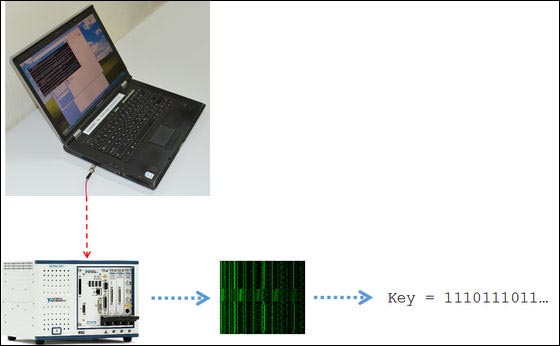
The ground potential of the PC body can be measured by an attacker in a state connected to the electrometer with a metal wire touching the target PC. Moreover, even if the attacker does not touch the PC directly, it can also measure by connecting to the potentiometer via the metal wire to the cable for the LAN cable and the display, so you can steal the key without noticing the other party is.
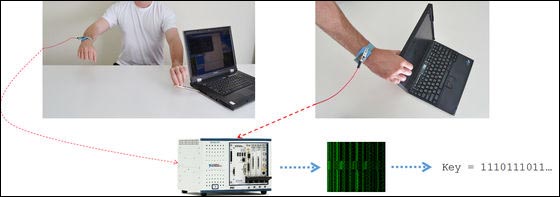
In the experiment, by measuring the ground potential with a smartphone (Galaxy S2) via a metal wire from the LAN cable of the notebook PC and analyzing the measurement data using a special algorithm, it is possible to use a well-known open source encryption softwareGnuPGThe private key was extracted from the PC that is decrypting the RSA encrypted data with.

While acknowledging that physical measures such as constructing an insulated structure so that the ground potential can not be measured from the PC case to effectively prevent the side channel attack using the ground potential is effective, it is a reality It is thought that it is better to realize it by taking countermeasures such as mixing random data in the calculation process on the encryption software side. The results of this experiment have already been reported to the developers of GnuPG, and the latest version of GnuPG introduces countermeasure patches.
Related Posts:
in Note, Posted by darkhorse_log