It is reported that the Bitcoin wallet can be hacked using the oscilloscope
In order to trade the virtual currency, you need to have a "wallet" that keeps the virtual currency that you own. This wallet has software and hardware types that are used for PCs, smartphones, tablets, etc., as well.BitcoinHardware wallet for "TREZORIn the old firmware of "oscilloscopeBy using Bitcoin's transactions necessaryPrivate keyThere is a vulnerability to take out the risk, there is a risk that the virtual currency is stolen.
Extracting the Private Key from a TREZOR
https://jochen-hoenicke.de/trezor-power-analysis/
Jochen Hoonnickke, a Ph.D. research engineer at Software Engineering at the University of Freiburg, pointed out that it is possible to retrieve the secret key used for Bitcoin transactions by analyzing the voltage flowing inside TREZOR with firmware version 1.3.2 or lower doing.
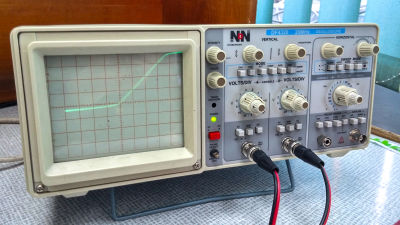
The way Funikke actually took out the secret key is to connect the TREZOR and the PC with a USB cable and to read the secret key from the waveform of the voltage flowing on the cable with an oscilloscope. Oscilloscopes used to extract secret keys are commercially available and cheap ones and there is no problem, Mr. Hunnick is relatively inexpensiveHantek 6002 BESucceeded to retrieve the secret key using. Voltage measurement can not be done directly from the USB cable, so Mr. Funicke attached a 10 ohm resistor (0.05 euro: about 7 yen) to the USB cable and measures the voltage across the resistor with an oscilloscope.

When the PC recognizes the TREZOR connected with the USB cable, since the software on the PC connects to "mytrezor.com", the TREZOR main unitPublic keyRequest. The requested TREZOR generates a secret key from a value called a seed value using a hash function, and generates a pair of public keys.
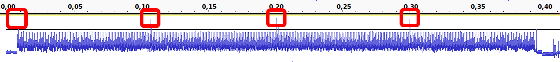
In the following image, the voltage when the TREZOR was actually started is the image below, the horizontal axis shows time (second), and the vertical axis shows voltage. According to Mr. Phnickke, TREZOR is that the secret key and public key are generated at the timing when the PBKDF 2 algorithm of the red frame part is executed.
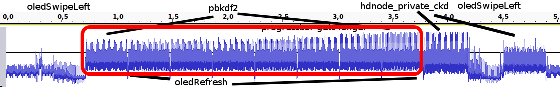
However, the waveform of the voltage acquired by the oscilloscope fluctuates due to the influence of the display change on the display. In order to do the actual analysis, it is necessary to peel off the display of TREZOR or display it blank so as to prevent disturbance in display voltage. Mr. Funikke shows the waveform of TREZOR when the display indication is blank, and it points out that there are four places of the red frame to which strong voltage is applied. According to Mr. Phnickke, he says he can retrieve the numbers necessary to calculate the public key by counting the number of small waves between big waves.
He also makes a test program for analysis, and it says that it is possible to derive a secret key by using the function in it. However, Mr. Hoonnick does not publish the actual program itself, and it keeps it out of simple logic only because of security consideration.
Mr. Hunnick says that even if the firmware of TREZOR is 1.3.2 or lower version, if you keep the passphrase protection function enabled, you do not have to worry that the secret key will be read using the oscilloscope and you can not upgrade for some reason Even though we are taking measures to take measures.
In addition, when upgrading the firmware to 1.3.3 or later, since the processing has been changed so that PIN authentication is required before calculating the public key, even if TREZOR is stolen it is difficult to analyze the secret key It is becoming. In addition to this, since the processing is changed so that the process of generating the public key from the secret key performs "no branch calculation", it is practically impossible to read the key from the voltage, Mr. Funicke I will explain.
Related Posts: