Be aware of the risk of information leakage from noise emitted by the device
There are various kinds of hacking methods for extracting computer information, but most of them are methods of intercepting communication illegally. Although it was able to prevent the damage by shutting off the communication and working offline, by analyzing the unique noise emitted by the device, information leaked from the device which should not originally originally emit information The problem that it is pointed out again.
GT | News Center :: Researchers work to counter a new class of coffee shop hackers
http://www.news.gatech.edu/2015/01/08/researchers-work-counter-new-class-coffee-shop-hackers
This research is conducted by Robert Callan, a graduate student at the Georgia Institute of Technology in the USA, and research teams by associate professors Alenka Zajic and Milos Prvulovic. When operating equipment such as a PC or smartphone or running software, noise such as various electromagnetic waves and sounds are emitted from the hardware installed in the device during processing, but if that noise is generated The problem of being able to steal information by measuring and analyzing has been pointed out before.
You can see how the device actually analyzes information by measuring the noise of the device in the following movie.
CyberSecurity - YouTube
About this problem, Associate Professor Prvulovic of the research team says "This is completely different from the way the usual hacker extracts information", and information can be extracted in a form not expected much Points are pointed out.

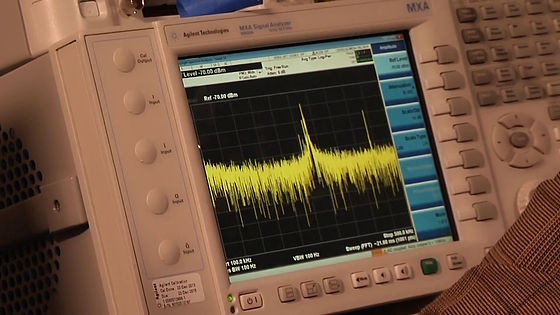
Waveform displayed on display of analyzing PC. This is an analysis of radio waves emitted from the PC board.

The text is continuously displayed next to the waveform, but ......

If you look closely you will see the letters "your password is (your password ......)". This is the result of analyzing the waveform of the noise emitted from the target computer, and it is clearly understood that the operation of the keyboard is in the way of a cylinder.

Associate Professor Zajic who measures the noise by placing the measuring device on the PC board. "Everyone is focusing on the security of the Internet and wireless communication, but what we are paying attention to is information that can be obtained from the computer itself, which should not have given any information," I point out the pitfalls of computer security.

The research team noticed a path of unusual information leakage called "side channel". This is what the computer is originally emitting information in a form not supposed to be able to extract the contents by analyzing the waveform of the noise like the picture below.
In order to solve such a problem, the research team used "Signal Available to Attacker (SAVAT: A signal that can be obtained by an attacker) "is proposed. This is an indicator showing the strength of the radio waves emitted by hardware, and is intended to help prevent the risk of information leakage in advance by incorporating this numerical measurement at the time of development.
The research team is paying particular attention that it is a problem of information being emitted from smartphones. Unlike PCs, smartphones tend to be easy to extract information because of large changes during operation and idling. Currently only Android devices are verified.

If this method is exploited, research teams pointed out that embedding antennas in tables such as cafes, libraries and station break spaces could lead to easy extraction of information. In addition, since the attacker can simply extract the information by simply receiving the signal, the victim side does not notice the damage at all.
Although it is said that the evidence that this method was actually misused has not been found so far, since it can be executed with a relatively simple apparatus, the risk of actual damage is considered to be high It is. Because of vulnerability derived from hardware, the actual countermeasure measures will be limited, but use PCs and smartphones in public places etc, and when dealing with particularly important information, they are unfamiliar to the surroundings The research team points out that it is better to check for suspicious devices and so on.

The report created by the research team can also be downloaded from the following link. Especially it seems to be useful for those who design the device.
(PDF file)http://users.ece.gatech.edu/~az30/Downloads/Micro14.pdf
Related Posts: