Researchers warn that there is a danger that a duplicate key will be made from 'sound when inserting a key into a keyhole'

As a method for unlocking a locked key by a third party who does not have a legitimate key, there is
Listen to Your Key :Towards Acoustics-based Physical Key Inference
https://dl.acm.org/doi/abs/10.1145/3376897.3377853
Researchers Can Duplicate Keys from the Sounds They Make in Locks
https://kottke.org/20/08/researchers-can-duplicate-keys-from-the-sounds-they-make-in-locks
Picking Locks with Audio Technology | News | Communications of the ACM
https://cacm.acm.org/news/246744-picking-locks-with-audio-technology/fulltext
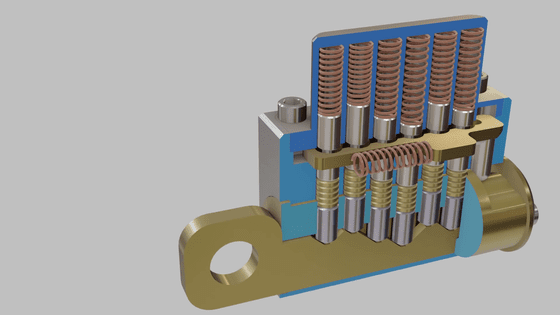
Widely used around the world, the pin tumbler lock consists of 6 metal pins connected to a spring and a double tube. When you insert the key, each pin is pushed up by the raised part of the key, and when all the pins are at the correct height, you can turn the key and unlock it.
It is said that there are about 330,000 lock patterns for pin tumbler locks, and even if you try to make a duplicate key randomly, it is extremely unlikely that you can break through the key you are aiming for. For this reason, criminals usually perform picking when opening the pin tumbler lock, but specialized equipment and the criminal's own skill are required for picking. In addition, even if you open the key once, you have to try picking again, so it can be said that there is a higher risk compared to duplicating the duplicate key that you can enter and leave once you make it.
Therefore, the research team of
HotMobile 2020-Listen to Your Key: Towards Acoustics-based Physical Key Inference-YouTube
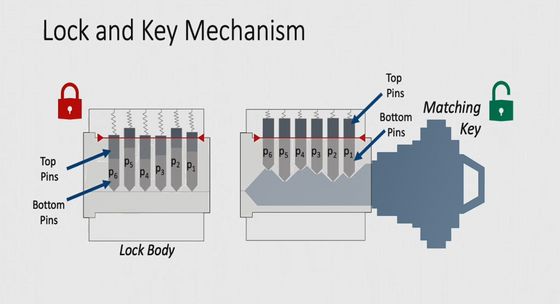
What is important in duplicating the duplicate key is the uneven and raised portion on the surface of the key. If you can identify the shape of this part, you can make a duplicate key that pushes the pin of the pin tumbler lock to an appropriate height.
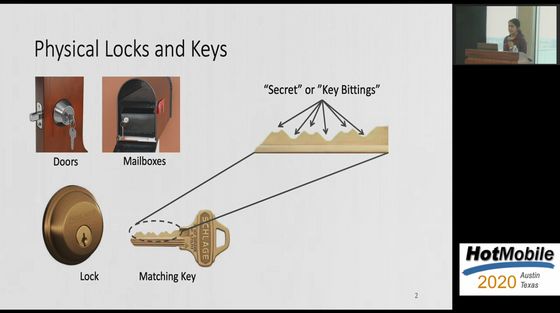
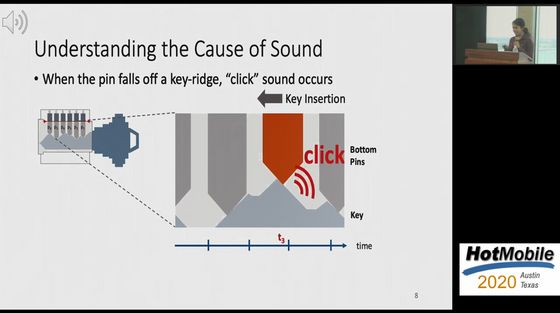
When you insert the key into the lock, the ridge of the key always hits the pin inside the lock and a metallic noise is generated. Ramesh's research team wondered if this 'sound' could be used as a clue to infer the correct key shape.

There is regularity in the raised part and the flat part of the key used for the pin tumbler lock, and it is said that the flat part to be combined with the pin is arranged at regular intervals.
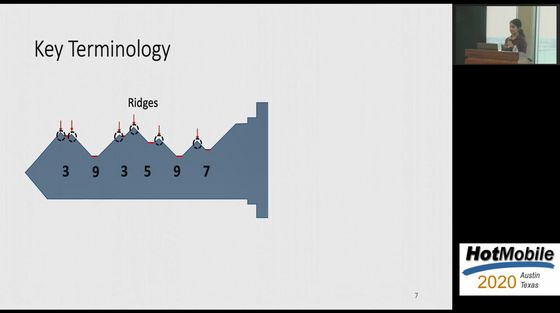
The sound of inserting the key is generated when the internal pin hits or rubs against the raised or flat part of the key. The sound when the pin crosses over the ridge is generated at regular intervals, which is an important clue to guess the shape of the key.
The research team developed software that analyzes this sound, and succeeded in guessing the shape of the raised part and the flat part of the key with high accuracy, using the sound when the key was inserted in the lock as a clue. If the speed of inserting the key is not constant, the accuracy of the guess will be adversely affected, but some fluctuation can be corrected by software.

If you can guess the correct key shape, you can create a duplicate key using a 3D printer. The software developed by the research team seems to have been able to narrow down the number of correct key candidates to 3 types from the approximately 330,000 types of pin tumbler lock keys. If there are only three candidates, it will take less time to create them with a 3D printer and try unlocking them.

In order to mount this attack, the criminal must obtain the 'sound when the desired key is inserted into the lock.' Possible methods are: 'Sneak up behind the door while the key is open and record it with the microphone of the smartphone' 'Install malware on the victim's smartphone and obtain the audio file when the key is opened' 'Hack a doorbell near a keyhole to obtain an audio file,' 'Use a
So far, it seems that the method using the attacker's own smartphone, which has the lowest execution hurdle, was not able to obtain sufficient volume for analysis unless it was located about 5-10 cm away from the key. The research team is studying various methods to solve this problem.
As a next step, Ramesh is also researching ways to prevent voice-based duplicate key duplication attacks. There is a risk of duplicating the duplicate key by using the sound as a clue, such as suppressing the sound produced by inserting the key slowly and quietly, and making the raised part of the key smooth to reduce the sound when inserted. Can be reduced, Ramesh said.

Related Posts: