How was the 'Toyota RAV4' with sophisticated security functions stolen?

Ken Tindel, chief technology officer at Canis Automotive Labs, which handles security technology for automobiles, explained
CAN Injection: keyless car theft | Dr. Ken Tindell
https://kentindell.github.io/2023/04/03/can-injection/
The beginning was that the headlight of Mr. Tinder's friend Ian Tabor's car was broken and the cable was pulled out.
No fcuking point having a nice car these days, came out early to find the front bumper and arch trim pulled off and even worse the headlight wiring plug had been yanked out, if definitely wasn't an accident, kerb side and massive screwdriver mark. Breaks in the clips etc. C&#ts
pic.twitter.com/7JaF6blWq9 — Ian Tabor (@mintynet) April 24, 2022
After another three months, Mr. Tabor notices that the car's headlights have been removed again. At first, Mr. Tabor did not understand the reason for this action. If someone tries to steal Mr. Tabor's car, it will be worth less by damaging the car.
Why do I bother having a nice car? I know it's a first world problem but can who ever it is just leave my fcuking car alone. No lights on the way to work this morning and even more gashes in the paint work and the molding has no clips any more. Not happy .
— Ian Tabor (@mintynet) July 19, 2022
However, a few days later Mr. Tabor's car was stolen. This reveals that the two acts of vandalism were a stepping stone to stealing the car.
I know what they were doing, the car is gone! My @ToyotaUK app shows it's in motion. I only filled the tank last night. FCUK! https://t.co/SWl8PcmfZJ
— Ian Tabor (@mintynet) July 21, 2022
In addition, Mr. Tabor's neighbor Land Cruiser also disappeared shortly after this. Therefore, Mr. Tabor, who is a cyber security researcher in the automotive field and has a history of receiving rewards for discovering vulnerabilities in automobile security, wondered how the criminal broke through the car security system. I decided to find out if he stole the car.
Mr. Taber first focused on the diagnostic trouble code (DTC) recorded when the electronic control unit (ECU) detected a failure. Tabor confirmed that Toyota's ' My Toyota ' system allows owners to view the DTCs that their vehicles send to Toyota's servers.
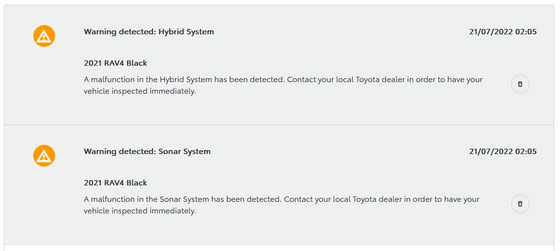
This revealed that Tabor's RAV4 recorded a number of DTCs before and after the theft. It is said that the recording of DTC is called 'dropping a DTC' among the industry. Specifically, it was recorded that communication with the ECU for light control was lost. This is natural given that the lights were broken.
However, it was also found that various systems other than the lights, such as the front camera and hybrid engine control, recorded the failure. Moreover, this failure was not due to the failure of the ECU itself, but due to the failure of communication with the ECU, which was determined to be a failure by diagnosis. At first glance, it looks like unconnected parts have failed, but they are connected by a certain mechanism. It is the Controller
Believing that the car had been stolen by CAN hacking, Tabor researched sites and message boards frequented by car thieves and thoroughly watched YouTube videos discussing car theft. went. As a result, we found a site selling over 100 tools to compromise automobile security, such as fake car keys and 'emergency boot devices.' This kind of criminal site was selling products to steal cars under the guise of owners who lost their keys and trusted repairers.
Among the theft tools sold on the site was an 'emergency boot device' for Toyota vehicles. The tool was stored inside a portable speaker, allowing the police to excuse it as just an audio product.
After learning that the tool 'supports' the Land Cruiser and RAV4, Tabor bought one to reverse engineer. Then I took it to CAN expert Ken Tinder and took it apart together.
This is the theft tool purchased by Mr. Tabor. Disguised as a JBL Bluetooth speaker.

Analysis of this tool revealed that the thief used a technique called 'CAN injection' to steal the car. Many modern cars are locked and unlocked with smart keys. The encrypted communication between the smart key and the car can only be broken by investing resources on a national scale, and in order to avoid this, methods such as
Countermeasures against relay attacks are taken, such as storing the smart key in a metal can that blocks radio waves, and setting the smart key to a power saving mode that does not respond to radio waves. Therefore, CAN injection is a newly developed method of theft to break through this.
Below is a simple CAN path diagram created by Mr. Tindel to explain CAN injection. 'Control CAN bus (red line)' connecting headlights, doors, smart keys, etc., and 'power train CAN bus (green line)' connecting engines, hybrid batteries, motors, etc. are shown.
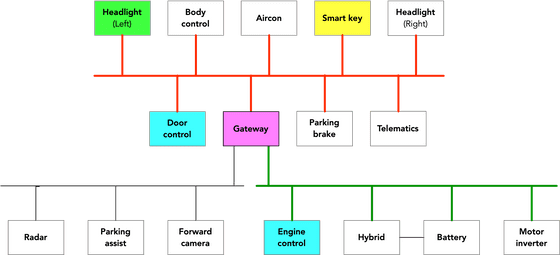
CAN injection intrudes into the CAN bus, which is the vehicle's internal communication, and injects a signal disguised as if it were a message from a smart key receiver saying, 'The key is valid. Please deactivate the immobilizer .'
In the case of the RAV4, the thief first hacked into the red control CAN bus and sent a 'key verified' message. The gateway ECU, colored purple, then relays its bogus message to the green powertrain CAN bus. The engine control system (light blue below) receives the message and stops the immobilizer. Finally, the thief sends a fake CAN message to the door's ECU (light blue above): 'The key is valid, please open the door.' This allows thieves to run the car without a smart key, which is how CAN injection works.
Below is the content of the aforementioned theft tool. Instead of a speaker, the theft tool contained a 'CAN injector' covered in a large black resin mass that enabled CAN injection.

When you power up the theft tool, the CAN injector does nothing and first waits for CAN messages that the car responds to. And when it receives the signal, it will send a fake CAN message with the signal 'Smart key is active'. After that, pressing the play button on the speaker changes the CAN message, now telling it to unlock the door. Mr. Tinder speculates that Mr. Tabor's RAV4 may have been stolen in this way. According to Mr. Tinder, this vulnerability to CAN injection is not a problem of specific manufacturers and models such as Toyota and RAV4.
After discovering the CAN injection method, Mr. Tabor contacted Toyota and offered support, but it did not go smoothly. One problem is that security issues are difficult for any large company to deal with. Adding to the difficulty is that it is not a normal vulnerability and does not fit into Toyota's process for responding to security issues.
The normal process is for ethical hackers to find exploitable vulnerabilities and report them to vendors, who then fix them. Vulnerabilities like this are called ' zero-day vulnerabilities ' because they risk having zero days left to fix, but CAN injection is already widely used in car thefts, so Tindel He describes this as 'minus 365 days.' Keyless vehicle theft is on the rise, but CAN injection is not considered a zero-day vulnerability as law enforcement considers it a broader relay attack.
Investigating any further would be risky and would require expensive specialized devices, so Tindell said, 'An industry group specializing in car security took over our project and asked what the thieves were doing with CAN injection.' It would ideally be a focal point among automakers looking for practical solutions to find out how they are using it.'
Related Posts:







