A security engineer reports on how he found a vulnerability that could freely rewrite millions of modems

Security engineer Sam Curry, who discovered a vulnerability in the system of the provider that operates his modem after his own modem was hacked, posted a blog post about 'how he discovered it.'
Hacking Millions of Modems (and Investigating Who Hacked My Modem)

It all started two years ago, when Curry was accessing an AWS instance from his home PC and encountered a strange phenomenon in which the same request was replayed from a mysterious IP address. In the log file below, '98.161.24.100' is the IP address of Curry's PC, but the same request was coming from a mysterious IP address, '159.65.76.209.'

Just to be sure, Curry tried accessing the site from a smartphone instead of a PC, and also tried setting up an instance on GCP instead of AWS, but the same problem occurred.

When Curry investigated 159.65.76.209, he discovered that the IP address was hosting a mail server as well as a phishing site targeting the Paraguayan security firm

Additionally, URL scan results showed that the IP address was being used for phishing by BeEF .

Malicious activity from this IP address has been recorded for over three years, and in addition to ISG Latam, various attacks have been launched from the same IP, including attacks against Adidas and the hack of Curry's modem. Although the attacker's intentions are unclear, Curry turned off his modem and requested a replacement from his provider, who owns the modem.

Curry wanted to keep the old modem and study the attacker's activities, but the provider's rules required that the old modem be returned when the new modem was handed over, and the old modem was taken away. When he set up the new modem, the traffic replay stopped, so Curry decided that the problem was fixed and stopped studying the attack.
In early 2024, Curry had a chance to talk to a security engineer friend, and when he told him about the modem incident, his security engineer friends were very interested. The friend, who had researched many more malware than Curry, focused on a domain that Curry thought was a mail server.
The friends speculated that the format of the domain that appears to be a mail server is the same as that used by other malware, and that this is a way for attackers to rotate the address of the C&C server that gives instructions to the malware. As shown in the figure below, the malware resolves the domain to obtain the IP address of the C&C server and receives instructions from the attacker.

Curry decided to look into how attackers had broken into the old modems. A Google search revealed no vulnerabilities in the modems, and if there were vulnerabilities, the attackers had managed to keep them hidden for years.
Later, when Curry was helping another friend move, he helped him migrate his modem, which was from the same provider as Curry. After connecting the modem to fiber optics, he contacted the provider's support and discovered that the provider could remotely control the device settings, including changing the Wi-Fi password and viewing connected devices.
The provider's remote support was made possible by a protocol called TR-069, implemented in 2004, which allows providers to manage modems in their own networks using port 7547. While the protocol itself has been the subject of security research, Currie was interested in the tools the provider's support was using to manage the modems.

Curry first investigated the Cox Business portal, which has features for remotely managing devices, setting firewall rules, and monitoring network traffic. Curry did not have an account and was unable to log in, but he found the API endpoint by analyzing the JavaScript on the page.

From the API response, Curry determined that the framework used internally was '

However, when the page was accessed, static resources such as JavaScript were not loaded and did not function. Curry discovered that there was a proxy rule that prevented external requests for static resources, and by adding the URL-encoded symbol '%2f' to the end of the static resource, he was able to circumvent the rule and load it, and display a list of API endpoints.

The APIs were roughly half authentication and half non-authentic, and it seemed as if important APIs were protected, but Curry discovered that by making the same request multiple times, it was possible to pass requests through APIs that required authentication without authentication. When searching for 'FBI' in customer profiles that actually have contracts with the provider, FBI data was found.

Curry continued his research and demonstrated that he could 'search for accounts by name and retrieve personal information,' 'obtain the MAC address of the hardware connected to the account,' and 'execute commands against the MAC address via the API.' However, for commands that change hardware, such as updating a password, a separate parameter called 'encryptedValue' had to be set.

Curry decoded the JavaScript code and found that the 'encryptedValue' was generated by the following two functions: Since both of these functions receive variables that only exist at runtime, Curry searched for places where they were actually used:
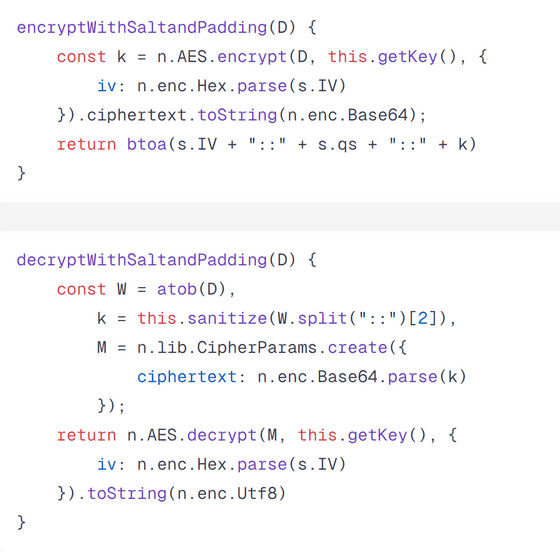
Curry then discovered that the four-digit PIN code on the account creation screen was encrypted using the two functions mentioned above.
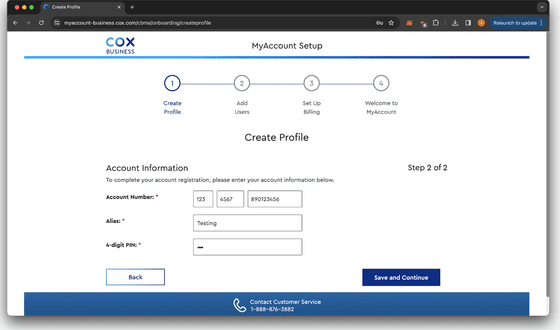
By setting a breakpoint where the function was being called, Curry could then correct the variable state and run the function from the console to encrypt and decrypt any data.

Curry actually targeted the modem he was using and sent an API request to change the Wi-Fi SSID name to 'Curry', and confirmed that his modem settings had actually been changed. It became clear that the same procedure could be used to freely edit millions of modems from the same provider.

Curry reported the vulnerability to the provider on March 4, 2024, and the vulnerability was fixed the next day, on March 5, 2024, making the method no longer work. The API-related service in which Curry discovered the vulnerability was released in 2023, after Curry's modem was hacked, so there are concerns that the modem may have other vulnerabilities.
Related Posts:
in Security, Posted by log1d_ts