A man-in-the-middle attack was discovered against Russia's largest XMPP message service, compromising at least 90 days of communications.

A man-in-the-middle attack was launched against Russia's largest
Encrypted traffic interception on Hetzner and Linode targeting the largest Russian XMPP (Jabber) messaging service —
https://notes.valdikss.org.ru/jabber.ru-mitm/
On October 16, 2023, oxpa, the administrator of jabber.ru, received a message saying 'The certificate has expired' and investigated and found that all the certificates installed on the server were valid. Even though the expiration date had been updated, an expired certificate was being returned for connections to port '5222', which listens for connections using XMPP's STARTTLS .
As a result of an investigation by multiple people including oxpa, the following facts were discovered.
・The server is sending a valid, valid certificate to the network.
・There are no expired certificates on the server.
・The expired certificate is based on someone else's private key and was not issued by the server's certificate issuance script.
Additionally, the TCP connection to port 5222 had been modified, and the source port number and SEQ/ACK number were different. Furthermore, the TTL value of the packet received on the server side is 64, indicating that the data is being sent without going through the router at all.
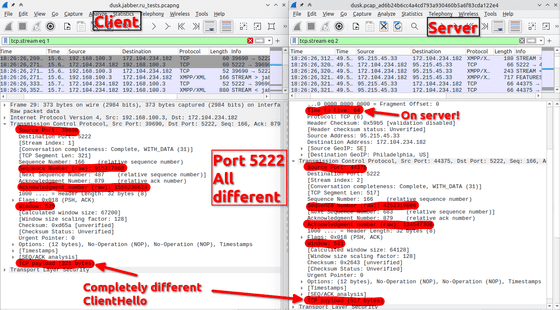
No such modification of packets was observed on ports other than 5222.

In this way, it became clear that a man-in-the-middle attack was being launched against connections to port 5222, so they further investigated the following details.
・All kinds of logs
・Modification date of executable files and libraries
・Running processes, memory maps, and files associated with each
・Whether LD_PRELOAD exists in userland, which hijacks libraries using statically compiled
・Dump kernel memory with LiME and analyze it by volatility to see if there is a kernel-level hijacking module
During these investigations, we were unable to find anything that could clearly be said to be the cause, but the research team found the following unusual record in the kernel log of the machine installed at Hetzner. This log shows that the physical network link was lost for 19 seconds on July 18, 2023.

As an alternative route to hosting jabber.ru, we also have servers on Linode. The server on Linode is only used as a tunnel to the Hetzner server, and only minimal basic services such as SSH and NTP are running, but when we analyzed the packets, we found that the ServerHello packet was sent from the Hetzner server to the Linode. It turned out that the file was authentic when it arrived at the server, but was altered when it was sent from the Linode server to the client. Therefore, Hetzner's server and Linode's server are subject to the same type of man-in-the-middle attack.
When you check the connection destination from a general Linode server, the MAC address of the Cisco router will be returned.
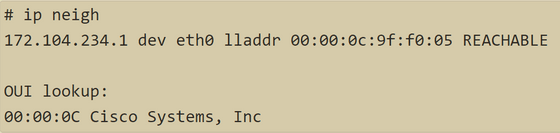
The Linode server being attacked this time was connected to an unknown device.

Furthermore, external network tests show that while a normal Linode server can be reached in 13 hops , the number of hops to the attacked Linode server is 14, with one non-stop in addition to the normal route. A public route has been added. In addition, the number of hops remained at 13 for port 5222, suggesting the existence of a device that performs additional processing only for connections to port 5222, but passes through communication to other ports.
Additionally, when we checked the certificate transparency database crt.sh , we discovered six certificates that were not issued by legitimate servers after April 18, 2023. This time, the existence of the attack was revealed when the certificate that was fraudulently issued on July 18, 2023 and actually used in the man-in-the-middle attack expired on October 16, 2023. That's why.
As a result of their investigation, the research team concluded as follows:
・The attacker successfully used Let's Encrypt to issue multiple SSL/TLS certificates for the jabber.ru and xmpp.ru domains starting from April 18, 2023.
・Man-in-the-middle attacks on XMPP traffic to port 5222 on jabber.ru and xmpp.ru were carried out from at least July 21, 2023 to October 19, 2023.
・The attack probably began on April 18, 2023.
・The attacker failed to reissue the TLS certificate, and the man-in-the-middle proxy provided an expired certificate on port 5222 of the jabber.ru domain.
- Man-in-the-middle attack began investigation on October 18, 2023 and stopped after submitting a ticket to Hetzner and Linode support teams
・However, passive eavesdropping still occurs on Linode servers.
・There is no evidence that either Hetzner or Linode servers were hacked.
・Both Hetzner and Linode networks have been reconfigured specifically for man-in-the-middle attacks on XMPP services.
The research team states that all communications between April 18, 2023 and October 19, 2023 should be considered compromised. Due to the nature of eavesdropping, an attacker can view an account's contacts, download unencrypted server-side messages, send new messages, or modify messages without knowing the account password. It was possible to do so.
The research team believes that this attack was a legal one at the request of German police. The research team recommends the following measures to detect such man-in-the-middle attacks:
・All SSL/TLS certificates are subject to certificate transparency , so you can use something like Cert Spotter to notify you by email of new certificates issued for your domain name. Monitor
- Restrict verification methods and account IDs that can issue new certificates
・Use external services to monitor SSL/TLS certificate changes for all services
・Monitor changes to the default gateway MAC address
・Use XMPP channel binding
Related Posts:
in Security, Posted by log1d_ts