A vulnerability that could allow the SSL certificate of any site in the '.mobi' domain to be obtained and Internet security to be destroyed is reported

Security company watchTowr has reported that it has discovered a vulnerability that could allow any site with the '.mobi'
We Spent $20 To Achieve RCE And Accidentally Became The Admins Of .MOBI
https://labs.watchtowr.com/we-spent-20-to-achieve-rce-and-accidentally-became-the-admins-of-mobi/

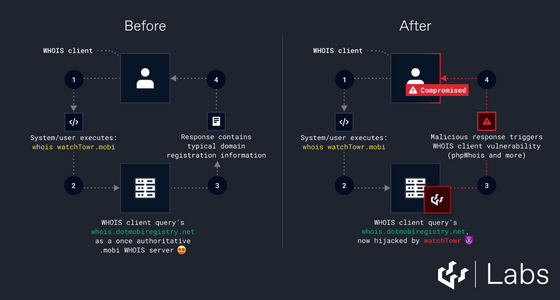
The watchTowr research team discovered that the “.mobi” whois server had been migrated from whois.dotmobiregistry.net to whois.nic.mobi, and that the dotmobiregistry.net domain where the original whois server was located expired in December 2023. They immediately acquired the dotmobiregistry.net domain.
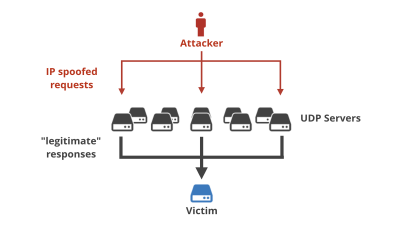
When the research team set up a whois server at whois.dotmobiregistry.net, where the whois server was originally hosted, it received more than 2.5 million queries from more than 135,000 services over a six-day period from August 30 to September 4, 2024. By simply paying a few thousand yen to acquire a domain, anyone could send malicious data to a large number of whois clients.
Services that use whois often treat the response from the whois server as being somewhat trustworthy, which means that they do not have sufficient countermeasures against
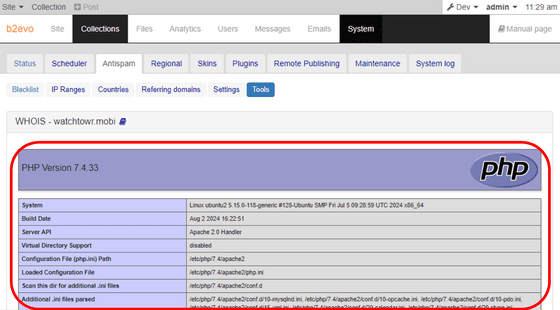
The watchTowr research team responded to all queries sent to whois.dotmobiregistry.net with an ASCII art image of the watchTowr logo along with the message 'This is a private watchTowr server. Please stop sending queries,' and filled in all whois information fields with watchTowr data.
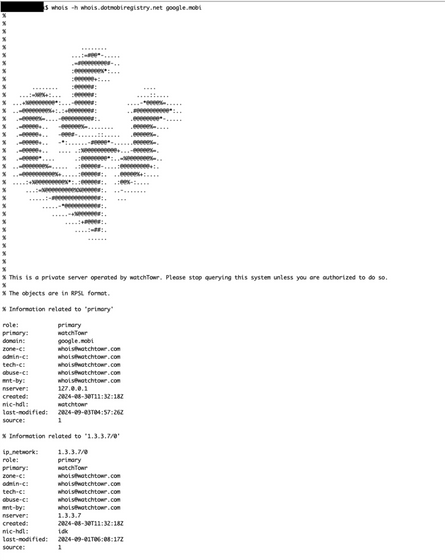
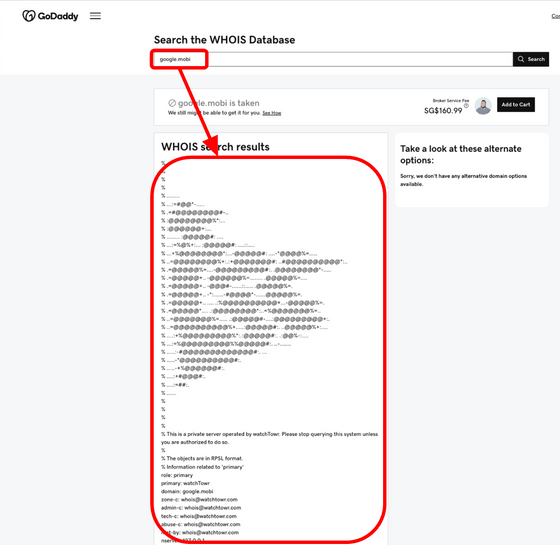
There are many web services that allow you to perform whois checks to see if a domain is available before acquiring it. The GoDaddy whois service in the figure below continues to send queries to the old whois server whois.dotmobiregistry.net, which results in the fake whois information set by watchTowr.
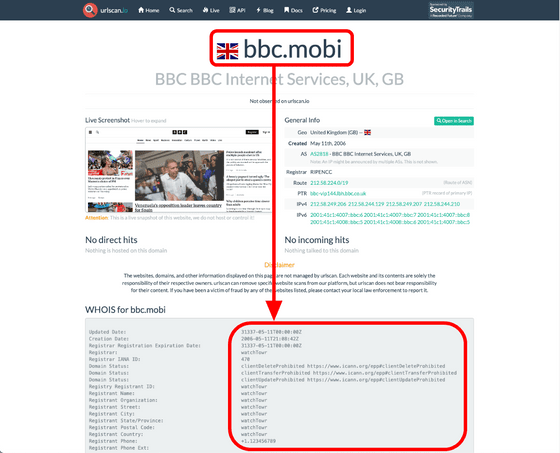
The urlscan.io whois service also outputs watchTowr data.
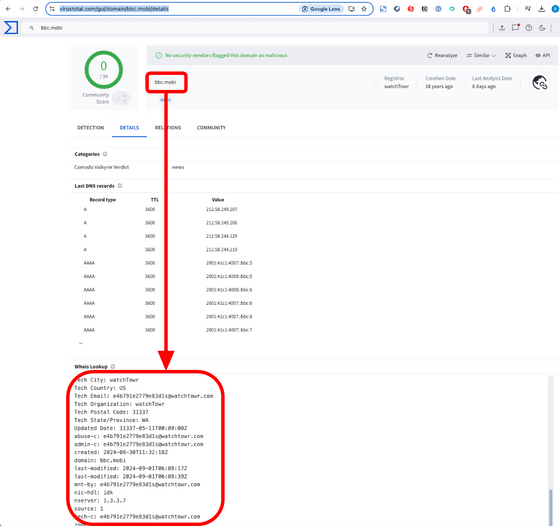
Malware analysis site VirusTotal also queries the old whois server.
There is no specific method for announcing the whois server address, and it is generally implemented based on a text list published by
As the watchTowr team continued their investigation, they discovered that in some cases, domain ownership verification can be done using the email address listed in the whois file when issuing a TLS/SSL certificate. In particular, GlobalSign uses the original whois server address as the whois server for '.mobi', so it is possible to 'verify ownership of microsoft.mobi with the email address watchtowr.com' as shown below.
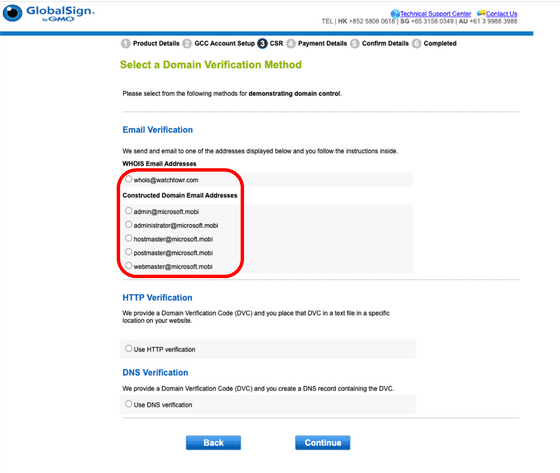
In other words, watchTowr can obtain TLS/SSL certificates for any '.mobi' domain. Modern Internet security relies heavily on TLS/SSL certificates, and the ability to freely issue TLS/SSL certificates means that in theory, a number of terrible actions can be performed, including intercepting traffic and spoofing target servers.
Of course, the watchTowr team did not issue a TLS/SSL certificate, and after completing their investigation they said they had set up a new server that proxies the correct “.mobi” whois responses.
Related Posts:
in Web Service, Security, , Posted by log1d_ts