The root cause of attack such as DDoS is that "IP spoofing" that spoofs IP can be done
DDoSAttack is an attack that loads and downs by sending requests from a large number of machines all at once to a target machine via the network. I got up in 2000MafiaBoyDDoS is an attack that plagues the Internet service industry for many years, such as GitHub being attacked in February 2018, beginning the incident. The reason why it is difficult to deal with DDoS attacks so far is to "disguise the IP address"IP spoofingWhat is done is done.
The real cause of large DDoS - IP Spoofing
https://blog.cloudflare.com/the-root-cause-of-large-ddos-ip-spoofing/
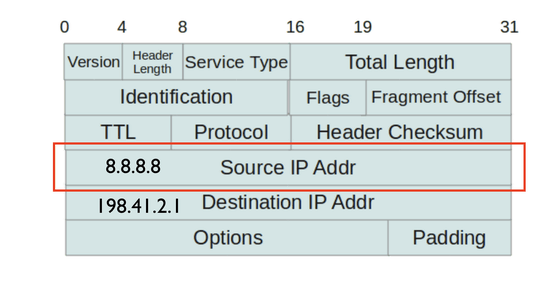
When exchanging data via the Internet, by notifying the sender's IP address in the header, you can let the other party know the reply destination. However, since the sender can freely describe the IP address of this sender, it can easily impersonate others. This is the "IP spoofing" problem, it is a mechanism that can send a large amount of data hiding the data source.
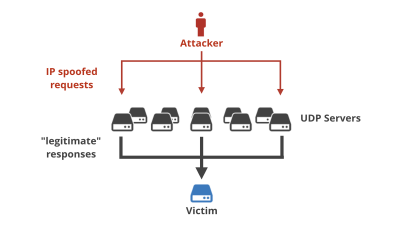
In addition, instead of directly sending data, you can amplify traffic by intervening through other servers. When accessing various servers by describing the attack target IP address in the IP address of the sender, the accessed server sends a reply to the IP address listed in "Sender" to puncture the target. From the attacked side, I know only the IP address of the vulnerable server on the platform.
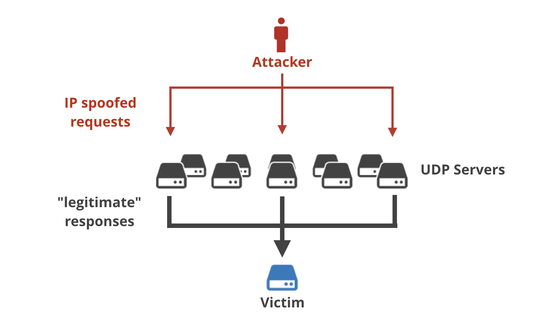
In addition, it is difficult to find IP address forgery on the Internet. In the Internet, the route connecting the machine and the machine is not limited to one, but it changes with time, there is also a possibility that the transmission route and the reception route may be different, so the route through which the packet is passed is legitimate I can not judge whether there is.
The attacker is unbeatable as it is not currently possible to track the attacker who is doing IP spoofing. It is more difficult to defend than an attack, and blogging concludes that it is necessary to actively address the IP spoofing problem in order to change this asymmetric structure.
Related Posts:
in Security, Posted by log1d_ts