Tor found out the dangers of botnet damage and breakthrough of encryption key by NSA, calling for updates to users

ByAndYaDontStop
It is an anonymous communication systemTorThere was a phenomenon that the number of connected users to the Internet rapidly increased from August 19, 2013. On the other hand, on the net "Net users are related to American NSAnewsBecause I was concerned about "and other speculation fluttered,TorBlogAnd the security vendor of the NetherlandsFox-ITAccording to the causeBotnetThat was.
Meanwhile, a security research companyErrata SecurityHas conducted its own investigation and announced on Toronto blog that Tor may be using an encryption key that is easily broken by NSA. The safety of Tor is questioned.
[Tor-talk] Many more Tor users in the past week?
https://lists.torproject.org/pipermail/tor-talk/2013-August/029582.html
Large botnet cause of recent Tor network overload | Fox-IT International blog
http://blog.fox-it.com/2013/09/05/large-botnet-cause-of-recent-tor-network-overload/
How to handle millions of new Tor clients | The Tor Blog
https://blog.torproject.org/blog/how-to-handle-millions-new-tor-clients
Errata Security: Tor is still DHE 1024 (NSA crackable)
http://blog.erratasec.com/2013/09/tor-is-still-dhe-1024-nsa-crackable.html
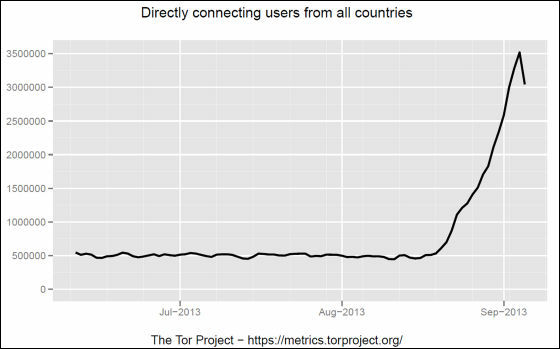
The graph below shows the number of users connected to Tor from all over the world on the vertical axis and the time on the horizontal axis. The graph shows that the number of connected users to Tor rose to climb from mid August 2013, and the number of users who had been about 500,000 in the beginning of September reached 3.5 million A situation occurred.
The cause of the increase in the number of users is "Net users fear connected PRISM operated by NSA" or "Tor is a browser that can avoid government restrictions on access to the websitePirate BrowserWe introduced various reasons such as "Introduced on August 10", but according to Fox-IT,Mevade.ACalled a botnet called itselfC & amp; C server(Command & amp; control) It turned out that Tor module was downloaded as a backup for communication.

ByDaniela Hartmann
Tor said that this attackTor 0.2.3.xIt is clear that we are using,handshakeWe are calling on users to upgrade to the new Tor 0.2.4 using a communication method called.
Also, Rob Graham, CEO of Errata Security,1024 bit RSA / DH encryption keyUsing Tor 0.2.3.x using a large amount of fundsCustom chipIt is easy to break through by the NSA that can produce the view.

ByWerner Kunz
According to a unique survey conducted by Mr. Graham,Diffie-Hellman key sharingThan Tor 2.3.x using the cryptographic protocol named "Elliptic curve cryptographyTook inElliptic curve Diffie-HellmanIt is said that Tor 0.2.4 which is using is more difficult to be cracked by NSA, but it seems that only 10% of the total users upgraded to Tor 0.2.4. Mr. Graham says, "Although it is still a mere measure, the 1024-bit RSA / DH encryption key that was most popular in the past 10 years is NSA's most likely to crack."

ByNick Carter
Tor is passionate for Tor such as "Attacks by Botnet" and "Older versions are easily broken by NSA", so Tor users seem to prefer to upgrade to the new version, Tor 0.2.4 as soon as possible.
Related Posts: