'Mēris Botnet', the largest DDoS attack in history, appears

A joint research between Russian security company
Blog — Mēris botnet, climbing to the record
https://blog.qrator.net/en/meris-botnet-climbing-to-the-record_142/
According to QratorLabs, in the last five years,
A new type of botnet 'Mēris' has been observed since around June 2021, and tens of thousands of host devices have been confirmed. Since the device is used in rotation and has never attacked at once with 'full power', the whole picture is unknown, but it is estimated that more than 200,000 units are installed.
Some describe the botnet as the 'return of the Mirai botnet,' which launched an unprecedented DDoS attack in 2016, but Qrator Labs has a slightly negative view. One of the reasons is that the botnet is made up of only products from Latvian network equipment manufacturer Mikrotik. For this reason, the botnet was given the name 'Mēris', which means 'plague' in Latvian.
What has been confirmed on the Mēris botnet is that it uses HTTP pipeline technology for DDoS attacks, that DDoS attacks themselves are based on RPS (number of requests per second), and that port 5678 of the damaged terminal is opened. matter.
According to the news site The Record, traditional DDoS attacks have been 'bandwidth attacks' measured in bps (bits per second) , sending as much junk traffic as possible to the target. However, the RPS attack is a 'volume attack', and it is said that it aims to occupy resources by sending a large number of requests to the target server and processing it, and finally crash the server. Prior to the DDoS attack that occurred in the summer of 2021, RPS-based attacks were rare, and no one of this scale was seen.
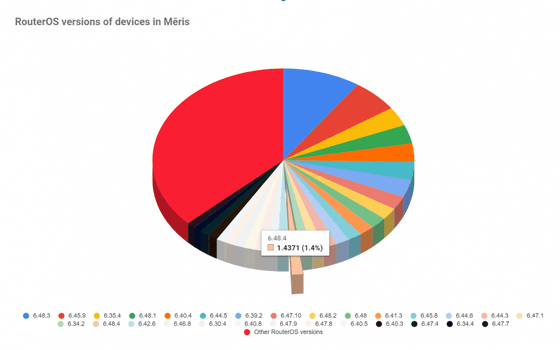
It is not known what kind of vulnerabilities are causing the large-scale damage to Mikrotik products, but the forum says that the router OS is version 6.40.1 released in 2017. It has been shown that there is a lot of hacking damage. On the other hand, the data collected by Yandex shows that even relatively new versions are suffering.
Router OS version distribution of damaged terminals shown by QratorLabs. While the latest stable version is '6.48.4', the most common version is '6.48.3', which is the previous version, so 'It is damaged because the firmware is old and no vulnerability countermeasures have been taken. You can see that this is not the case.
QratorLabs believes the Mēris botnet is responsible for the large-scale DDoS attacks that occurred in multiple countries in early summer 2021, including the 17.2 million requests per second DDoS attack detected by Cloudflare. .. The Mēris botnet is said to have the potential to overwhelm even robust infrastructure with its enormous RPS power.

The '17.2 million requests per second' detected by Cloudflare is also unprecedented, but according to Yandex, the attack received on September 5, 2021 was even larger, '21.8 million requests per second (21.8 million RPS)'. That thing.
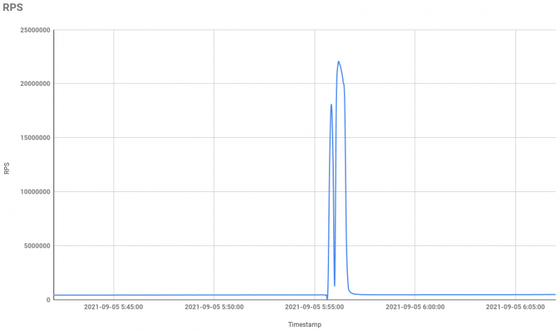
Analysis of the attacks on Yandex revealed that both ports 2000 and 5678 were open to the attackers. Of these, port 5678 is used by Mikrotik in UDP because it is a Neighbor Discovery Protocol, but it was used by TCP in the damaged terminal.
Based on the information, Qrator Labs investigated 'Port 5678 open by TCP' and found that there were 328,723 active hosts on the Internet. Although not all are victims, Qrator Labs writes, 'We have to assume that this could be the entire Mēris botnet.'
Distribution map of the terminal shown by QratorLabs. The darker the color, the more applicable terminals there are. The largest number is 139,930 (42.6%) in the United States, followed by 61994 (18.9%) in China, 9244 (2.8%) in Brazil, and 4928 (1.5%) hosts in Japan.
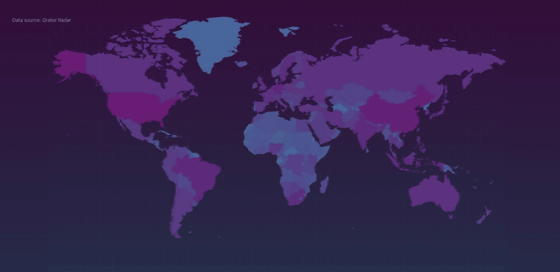
QratorLabs has reported this result to Mikrotik and is calling for 'always update network devices to the latest firmware'.
Related Posts:
in Security, Posted by logc_nt