A Linux malware 'perfctl' that uses 100% of the CPU to mine virtual currency has been discovered, and since it stops its activity when you log in, it is difficult to detect and millions of servers may have been targeted

It has become clear that a Linux malware called ' perfctl ' has been active for more than three years. perfctl is a malware that uses 100% of the CPU to mine the virtual currency 'Monero', and it is estimated that millions of servers have been targeted and thousands of servers have actually been affected.
perfctl: A Stealthy Malware Targeting Millions of Linux Servers
Linux malware “perfctl” behind years-long cryptomining campaign
https://www.bleepingcomputer.com/news/security/linux-malware-perfctl-behind-years-long-cryptomining-campaign/
Although the details of perfctl were reported by security company Aqua , the existence of perfctl itself has been reported on the Internet for three to four years. For example, on March 2, 2022, a report was posted on an online forum that 'a process called perfctl uses 100% of the CPU.'
linux - 100% CPU load caused by service 'perfctl' - Server Fault
https://serverfault.com/questions/1095192/100-cpu-load-caused-by-service-perfctl
Aqua's detailed analysis of perfctl revealed that upon startup, perfctl established an internal communication route using UNIX domain sockets and an external communication route using Tor to execute the Monero mining tool ' XMRig .'
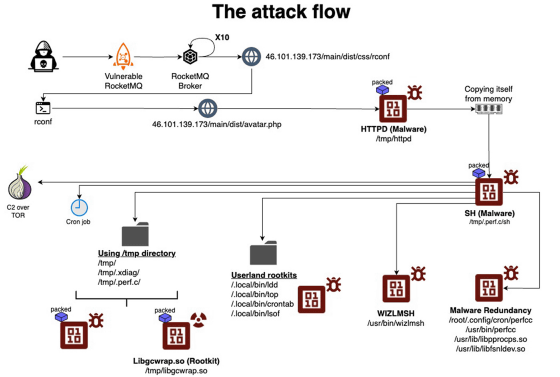
Below is a list of files that perfctl creates on the target machine. perfctl evades surveillance by running mining when the user is logged out and stopping mining when the user logs in. In addition, a function to 'delete competing malware' was also implemented to extend the uptime of the target machine.
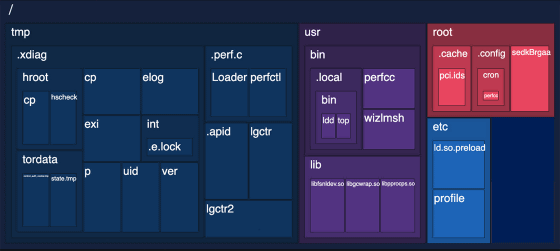
Aqua lists the following methods for detecting perfctl:
- Check whether there are any suspicious files in '/tmp', '/usr' or '/root'.
- Monitor CPU usage spikes
- Check to see if processes such as 'httpd' or 'sh' are running in unexpected locations.
Check the system log for changes to '~/.profile' and '/etc/ld.so.preload'
・Monitor Tor communications to external IP addresses such as '80.67.172.162' and '176.10.107.180'
Monitor connections to cryptocurrency mining pools and proxy jacking services
・Monitor communications to known malicious IP addresses such as '46.101.139.173', '104.183.100.189', and '198.211.126.180'.
- Check whether 'ldd', 'top', 'lsof', 'crontab', etc. have been replaced with malicious versions that contain a Trojan horse.
・Analyze logs to monitor for 'misuse of system binaries,' 'suspicious cron jobs,' and 'falsified error messages.'
Related Posts: