Anonymous communication system 'Tor' What is 'KAX17' that runs a large number of malicious servers on a network?

Is “KAX17” performing de-anonymization Attacks against Tor Users? | By nusenu | Nov, 2021 | Medium
https://nusenu.medium.com/is-kax17-performing-de-anonymization-attacks-against-tor-users-42e566defce8
A mysterious threat actor is running hundreds of malicious Tor relays --The Record by Recorded Future
https://therecord.media/a-mysterious-threat-actor-is-running-hundreds-of-malicious-tor-relays/
Someone Is Running Hundreds of Malicious Servers on Tor Network
https://gizmodo.com/someone-is-running-hundreds-of-malicious-servers-on-the-1848156630
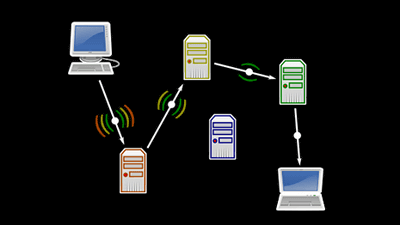
In a normal communication system, when you access a website or send an e-mail, the user's IP address remains on the server, and it is possible to identify the user based on this. However, with Tor, communication is possible with the IP address anonymized by using multiple servers (relays) on the route from the source computer to the destination and encrypting everything except the exit of the access route. I am doing it.
You can find out more about how Tor works by reading the following articles.
An easy-to-understand explanation of how anonymous communication 'Tor' works --GIGAZINE
by la inventoría
The servers that play an important role in the anonymization of the Tor network are provided by volunteers who support Tor. Volunteers adding servers to the Tor network should include contact information, such as email addresses, during setup so that Tor administrators and law enforcement agencies can contact you in connection with reporting misconfigurations and abuses. However, servers that do not follow this rule and do not declare contact information are often added to the Tor network to guarantee a sufficient number of servers for anonymization.
Security researcher nusenu discovered that 'a large number of servers without contacts' are being run by the same actor in the Tor network. It is pointed out that this actor named ' KAX17 ' has about 900 servers running and is located in data centers all over the world, and has quite a lot of resources.
The relays in the Tor network are divided into three parts: the 'guard relay' which is the entrance part of the network, the 'intermediate relay' which is the relay part, and the 'exit relay' which is the end part. Since the number of servers executed by KAX17 is very large, when a user uses Tor, the probability of using the KAX17 server as a guard relay is 16%, the probability of using it as an intermediate relay is 35%, and the probability of using it as an exit relay is 5. It will reach%.
In general, most threat actors running malicious servers in Tor networks focus on egress relays that can affect your traffic. For example, the threat actor 'BTCMITM20 ' is running a large number of exit relays to replace the address of the Bitcoin wallet in the traffic. However, KAX17 is unique in that it focuses primarily on guard relays and intermediate relays, and nusenu points out that the purpose of KAX17 may be to 'gather information about Tor users.' ..
Regarding the purpose of KAX17, nusenu said, 'There is no evidence that they are actually conducting a de-anonymization attack, but they are in a position to do so, and no one can do a normal relay. The fact that we are running a percentage of (intentionally ambiguous) large networks is enough to sound all sorts of alarms. '

nusenu reports to the Tor Project every time he discovers a KAX17 server from 2020, saying that the Tor Project removed the KAX17 server from the Tor network in October 2020, October 2021, and December 2021. That. According to nusenu, KAX17 has set an email address on some of the servers it ran in the past, and later subscribed to Tor's relay mailing list with the same email address, opposed the suggestion to 'remove malicious relays.' He also knows that he was doing it.
Related Posts:
in Web Service, Security, Posted by log1h_ik