Cloudflare explains the state-of-the-art cyber attack 'SAD DNS', what is its clever technique?

The
SAD DNS Explained
https://blog.cloudflare.com/sad-dns-explained/
IP addresses are used for communication on the Internet, but IP addresses, which are just a series of numbers, are difficult for humans to handle. DNS makes such IP addresses correspond to domain names such as 'gigazine.net' so that you can use the Internet comfortably. DNS consists of a 'DNS query' that requests an IP address from a domain name and a 'DNS reply' that returns an IP address.
There are three factors involved in converting a domain name to an IP address by DNS: 'client', ' resolver ', and ' authoritative server '. The client first sends a DNS query to the resolver, and if the resolver caches the correspondence between the inquired domain name and IP address, it sends a DNS reply to the client as it is. If the domain name is not in the cache, in order to authoritative server of each domain that sends a DNS query structure has become.
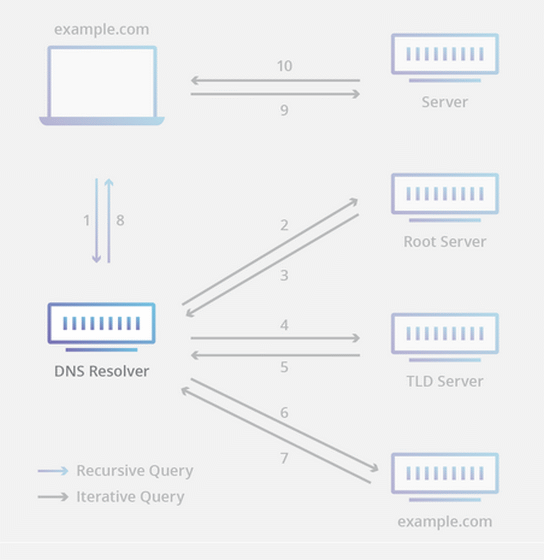
DNS generally communicates using
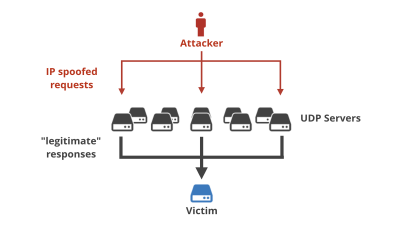
DNS has additional features to complement UDP, which lacks encryption and authentication capabilities, and to make it difficult for attackers to spoof responses. Specifically, when sending a DNS query, a random ID is also sent, and if the DNS reply has the same ID, it will be processed as a legitimate response. Since DNS replies need to be sent to the source port number of a DNS query, the 'DNS ID' and 'source port number' contribute to increasing entropy in DNS and make spoofing difficult. I am.
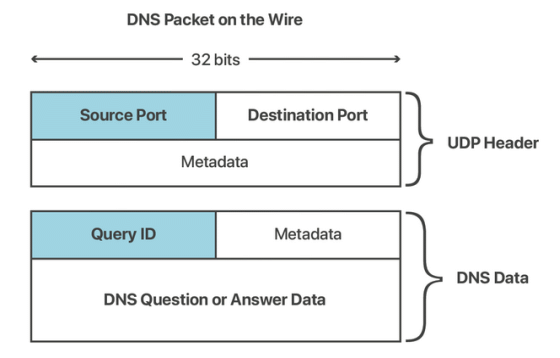
However, it is said that such a mechanism is not fully functioning. Since the resolver port number is generally 53, the only factor that increases entropy is the ID. In addition, only 65,536 IDs could be set, which was too simple to make spoofing difficult. This weakness is used in the
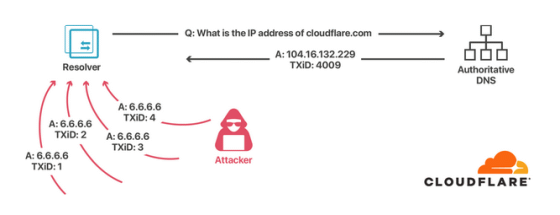
In order to deal with the Kaminsky type attack method, a function to randomize the port to be used has been implemented in the resolver, but there is still a method to attack DNS. One of them is a method that utilizes the fact that all the randomness that increases the entropy of DNS is included in the 'DNS message'. UDP combines the DNS ID and source port into one split destination when packet splitting, and stores the DNS data part in another split destination, so if the DNS data part can be replaced, the ID and source You can disable port randomization.
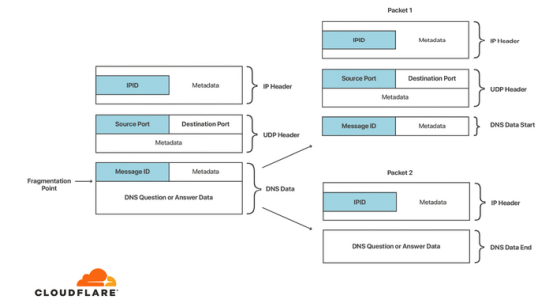
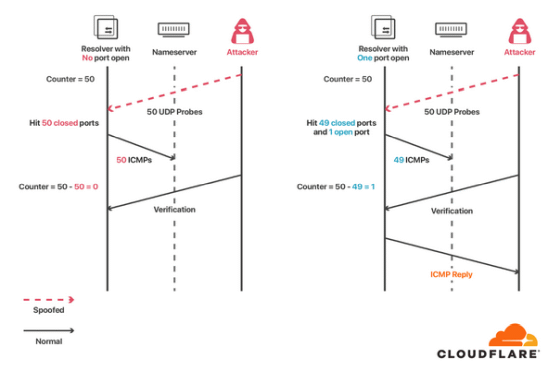
This time, the DNS attack method 'SAD DNS' newly discovered by research teams such as the University of California and Berkeley adopts an approach of identifying the port used by the resolver. To determine the port has various techniques, but in SAD DNS ICMP limiting the error transmission interval that the 'ICMP Rate Limit' is used.
ICMP Rate Limit is a function that limits the number of times ICMP error messages are sent at regular intervals. You can increment the counter by one each time you send an ICMP error message, and stop sending error messages when the number of counters reaches the limit. This feature can prevent the server from puncturing with a large number of ICMP packets, but Cloudflare says that if you turn it over, it will give the attacker information about 'whether there are open ports'. Explains.
If the ICMP Rate Limit is 50, the attacker first sends packets to a total of 50 ports in the resolver, 1000-1049, and then sends additional packets to some ports. If any one of the ports 1000-1049 is open, the ICMP Rate Limit is not working and you should get an ICMP error message response to additional packet transmissions. By this operation, the attacker can obtain the information that 'one of the 1000 to 1049 ports of the resolver is open', and by repeating the operation, it is possible to identify the open port. ..
Cloudflare has already taken measures to make it difficult to guess the DNS ID in its DNS service ' 1.1.1.1 ', but it has not reached a fundamental solution to SAD DNS. The problem is that DNS relies on ' security by hiding ' to ensure security by hiding IP addresses and port numbers, and the spread of DNSSEC that can confirm the validity of DNS replies using digital signatures Cloudflare commented that it would focus.
Related Posts: