Cyber attacks involving virtual currency mining occur on supercomputers

Multiple high performance computing (HPC) systems installed in various European countries are being forced to stop using one after another due to 'security problems'. A research report revealed that this problem was caused by a cyber attack and that the attacker's purpose was to mine crypto assets (virtual currency) using supercomputers.
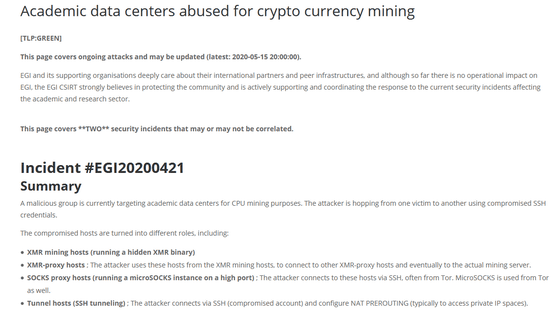
Academic data centers abused for crypto currency mining | EGI CSIRT
European supercomputers hacked in mysterious cyberattacks
https://www.bleepingcomputer.com/news/security/european-supercomputers-hacked-in-mysterious-cyberattacks/
Supercomputer in Europa gehackt: Mindestens neun in Deutschland betroffen --DER SPIEGEL
https://www.spiegel.de/netzwelt/web/supercomputer-in-europa-gehackt-mindestens-neun-in-deutschland-betroffen-a-7d9403b9-c7ea-4f84-a9d7-17bbdff3a954
The cyber-attack in question was recognized as 'dangerous' from around January 2020, but it wasn't until May 2020 that it had a clear effect. Multiple HPC systems are no longer available in the UK, Germany, Switzerland, etc. due to security issues.
Although there was a notification to the user that the supercomputer could not be used due to a security problem, details of what kind of problem was occurring were not disclosed, but on May 15, 2020, the European grid • The Computer Security Incident Response Team (CSIRT) , an organization called Infrastructure (EGI), has released a summary of the information.
According to the EGI CSIRT, there are two major events, '# EGI20200421' and '# EGI2020512', and it is unclear whether they are related to each other or not.
However, it is common that all attacker groups have launched attacks with the purpose of 'using research computing resources for mining the virtual currency' Monero ''.
Researchers typically do not connect their computers directly to the HPC system, but rely on secure online access using user accounts and SSH key authentication. It's not clear how the attacker stole the SSH credentials, but some victims have found dangerous SSH binaries.
In addition, attackers are using various techniques to conceal malicious activities, and in some cases they are set to operate only at night to avoid detection.
There are already more than a dozen supercomputers affected by this attack in Europe, and according to EGI CSIRT, victims have been confirmed not only in Europe but also in North America and China.
Related Posts:
in Security, Posted by logc_nt







