How does 'RAM Scraper' stealing over 100 million credit card information steal large amounts of card information?

ByJm3 on Flickr
It is a major supermarket chain in the United States on September 29, 2014SUPERVALUWhenAlbertsonsBut,cash registerYaPOS systemBy hacking toUnauthorized access from outside to customer's credit card informationIt was done. In recent years, hacking incidents aiming at cash registers and POS are increasing in the United States, and the number of major American retailersTargetYaHome DepotThere are things that have been targeted, but the malware used for these hacking "RAM scraperAbout WIRED reveals its method in detail.
How RAM Scrapers Work: The Sneaky Tools Behind the Latest Credit Card Hacks | WIRED
http://www.wired.com/2014/09/ram-scrapers-how-they-work/

◆ RAM scraper
"RAM scraper" is the computer'sRAMIt collectively refers to malware that collects and steals data from within.
A hacker aiming at SUPERVALU or Albertsons makes illegal dumping of RAM scraper into the POS system of these companies and temporarily saves it in the RAM of the register at the time of purchase processing by a credit card or a debit card carried out at the cash register We succeeded in stealing the "customer's credit card information in an unencrypted state" to be stolen. It seems that credit card information can easily be stolen in this way, and more than 100 million credit cards have been damaged so far.

ByMoneyBlogNewz
There are more than 12 kinds of RAM scrapers currently being traded on the black market. Basically, these RAM scrapers collect data from RAM in the same way, but they also have different characteristics, for example, RAM scraper called "Dexter" steals customer's password in addition to card information It is malicious malware. Also, "ChewBacca" is a RAM scraper that uses Tor from an intrusive network environment and is designed to send secretly stolen data to a hacker.
RAM scraper is not the only tool to steal credit card information. Such as ATMSkimming deviceIt is possible to steal credit card information by using. In order to steal card information using a skimming device, it is necessary to actually install the device in the ATM, but the RAM scraper can be invaded into the retailer's network by remote operation, and dozens of retail stores, franchise checkouts It is also possible to get into the POS system.
In addition, if you hack with RAM scraper, you can clean up the evidence of the crime by remote operation, so if you steal your credit card information, which method is more secure is obvious.

ByElton Lin
◆ How is card transaction done
When purchasing something using credit or debit cards, small retail stores and others use third-party card processors to process card transactions. These card processors obtain card information in a state of being unencrypted at the time of purchase processing and transmit this data to the bank, if the authentication is obtained, the purchase transaction is completed, money is transferred from the bank, the customer You can purchase items.
In the case of a major supermarket chain or the like, since a large number of card transactions occur in each chain, card transactions of each store are sent to the central processing unit via the corporate network, where card information is sent to appropriate banks respectively, You get the purchase transaction is complete.

ByMike Mozart
When you introduce a card system to a store so that customers can make payments using credit cards or debit cards,PCI data security standardIt is necessary to satisfy. This was jointly formulated by companies such as VISA, MasterCard, Discover, American Express, JCB, which are the top players of the credit card industry. According to this, when storing card information on a business network or the Internet, always data It is said that it is necessary to encrypt it.
However, this PCI data security standard does not mandate "encryption when card information is moved within the company network or when card information is transmitted to an external data processing organization via a private network". However, it seems that smart companies have dealt with hackers by encrypting the data everywhere to make it safer system.
In this way, companies have been working on encrypting card information to protect customers' card information, but within the processing process of card transactions, the moment the encryption of the card information will definitely be unlocked and become unprotected there is. When you scan the card to make payment with the card, we will move to the authentication work with the bank to confirm that the card information is correct. At this time, the account number and various customer information accompanying it are stored in a state where the encryption is decrypted on the memory of the POS system, and the RAM scraper enters here to steal the customer's credit card information.

ByDon Hankins
◆ Solution
When the RAM scraper gets into the system, it examines what the system is running from among the processors and detects the memory storing the card information. After stealing a lot of card information from the cash register RAM, the RAM scraper is stored in a place where the hacker can collect it remotely together with the stolen data in the encrypted state.
A lot of companies have become prey to RAM scrapers so far, but this can not be prevented never. The ramification of the current RAM scraper is to make the PCI data security standard "encrypt card information all the while from the moment of inputting a personal identification number with the keypad until the card information reaches the bank for authentication" If you fix it, you can prevent it. However, since most card processors do not currently have the function for encrypting card information, there may be a need to set new functions for encryption and new protocols for data communication .

ByDaniel Foster
OtherEMVBy using the card, the damage by the RAM scraper is stopped. A microchip is embedded in the EMV card, and it is used by holding it over a dedicated device, but it is necessary to input PIN code in addition to holding it over. Also, the information in the cardDigital signatureAlso, even if information on this EMV card is stolen, it can not generate code necessary for card transactions. In the United States, this EMV card is slow spreading, and since many credit cards and debit cards of magnetic cards are still circulating, it is thought that there are more damage by RAM scraper than in other countries.

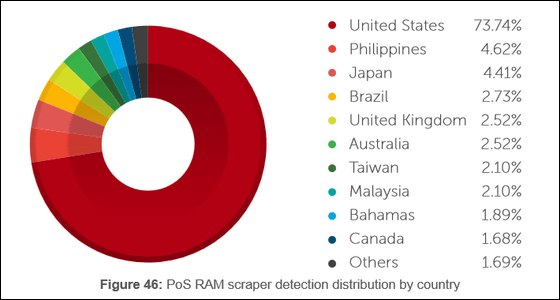
When Internet Security Trend Micro examined the number of RAM scrapers that are traded on the black market, it is said that Japan is the country that purchased RAM scraper the third most in Japan.
Related Posts:
in Note, Posted by logu_ii