Astonishment cyber attack "aIR-Jumper" to hack the infrared monitoring camera and leak confidential information to the camera

A cyber attack that sends instructions to the surveillance camera and leaks confidential information with infrared rays using infrared rays invisible to human beingsaIR-JumperIsraeli researchers have developed. aIR - Jumper has the cleverness that even if the surveillance camera system does not have a network with the outside, it can be operated remotely and the appearance of the attack can not be seen from the outside.
[1709.05742] aIR-Jumper: Covert Air-Gap Exfiltration / Infiltration via Security Cameras & Infrared (IR)
https://arxiv.org/abs/1709.05742
Security cameras are vulnerable to attacks using infrared light: study
https://phys.org/news/2017-09-cameras-vulnerable-infrared.html
High performance surveillance cameras use infrared rays for shooting in the dark. However, because the infrared itself is invisible, humans can not visually check the motion of the surveillance camera in the dark. A hacking method "aIR-Jumper" using this invisible point of infrared ray was developed by a team of researchers such as Moldechai Gri of Negev-Ben-Glion University in Israel. aIR-Jumper is "to operate a surveillance camera system through surveillance cameras by sending and receiving signals using infrared rays".
In aIR-Jumper, we first put in malware to send and receive infrared signals in the surveillance camera system. Systems infected with malware can read infrared signals with surveillance cameras or, on the contrary, infrared signals can be sent to the surveillance camera via infrared signals.
Cyber Attack Using Infrared Camera The mechanism of aIR-Jumper can be understood from the following two movies.
hidden communication via security cameras - YouTube
Picture of the surveillance camera shooting the park. Since it is a surveillance camera compatible with infrared rays, it is possible to clearly display images even in the dark.

One car appeared on the screen. This car that stopped slowly in the parking lot is an attacker that launches the aIR-Jumper attack.

A blinking light that can be confirmed from the window of a car is one using infrared rays. Other people in the parking lot do not see the flashing lights. This infrared light blinking has information like Morse code and it is possible to send a command to the infrared camera under shooting. The malware stuck in the surveillance camera system stands by the surveillance camera so that it receives infrared signals from the outside and waits for a cyber attack signal.

The surveillance camera that receives the instruction by the infrared signal can return the information with the infrared signal.
leaking data via security cameras - YouTube
A surveillance camera controlled by a surveillance camera system infected with malware. The generated infrared signal can not be confirmed with the naked eye.

So I will try using a terminal with a camera that can detect infrared rays such as smartphones.
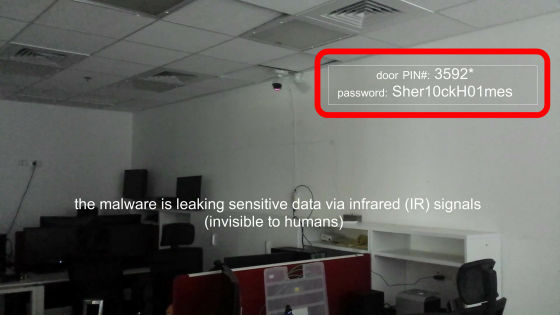
A surveillance camera that started flashing by infrared rays.

Flickering like Morse code sent to me, confidential information such as door security PIN code and password. With aIR - Jumper it is possible to send an instruction to send information in the system to malware waiting on the system and send that information to the camera in the form of infrared blinking.
When sending anything, the camera starts flashing.

"The adventure of Tom Soya" and the surveillance camera returned to the command "Send famous book name".

Risk of surveillance cameras being hacked from the outside is drawing attention, and it is considered that blocking the network with the outside is one effective means. However, even if you block the network with the outside, if you allow malware to enter the internal network, it is impossible to prevent aIR-Jumper attacks that can be remotely controlled via infrared. Since it is extremely difficult to distinguish from the outside that it is under attack by aIR - Jumper, it seems there is a risk of delaying the discovery of the fact of receiving a cyber attack.
Related Posts: