There is a security hole where an image of a camera can be seen in an Android terminal

ByIamos
It is installed in notebook PC etc.Risk of hacking webcam and being abused for voyeurismAlthough infringement of privacy by cameras connected to the network is pointed out, such as being pointed out, the Android terminal does not notice the user by remotely manipulating the thing that is reflected on the camera, sees the image and other data It was revealed that there was a security hole that could send.
Snacks for your mind: Exploring limits of covert data collection on Android: apps can take with photos with your phone without you knowing.
http://snacksforyourmind.blogspot.co.uk/2014/05/exploring-limits-of-covert-data.html
Szymon Sidor, a college student, found this security hole. When I was studying the security of computers and networks in the campus project, I discovered that there was a problem with Android's camera function by chance, and decided to publish it on my own blog.

A state that Sidor actually reproduced the problem is published on YouTube.
Covert video capture on Android. - YouTube
Mr. Sidor has Nexus 5 in hand. The terminal is in sleep state, so the screen is pitch black and nothing is displayed ......

The camera data sent from the application installed on the terminal is displayed on the PC screen.
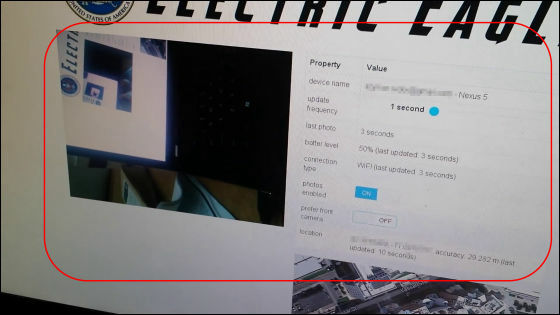
On the monitor, not only the photo but also the details of the terminal such as the Google account name, the remaining battery level, the network being communicated, etc. are displayed, and the current position information is also displayed, and this action is a duplicate I will.
I tried to cancel sleep. Since the camera is running, normally the screen of the camera should be displayed, but just the home screen is displayed, you can not know that the camera is running under just one glance.

Even if you display the running application, "No recent apps" is displayed and there is no chance to notice the startup of the camera from here as well.

In the meantime, the image captured by the camera was continuously sent on the screen of the PC.

Although the content of the specific camera image sampling application is of course not disclosed, Sidor is calling out on the blog that the following countermeasures are effective in order not to suffer similar application damage.
1. Pay attention to "app authority" displayed when installing the application
Attention is required when requesting authority to the camera function despite an application that may not be related to the camera, such as a memo application.

2. Keep your Google Account secure
To increase security and prevent hijacking by others,2 step verification processIt is important to use measures such as updating passwords regularly. Also,Commonly used passwordsTo avoid using it is also one countermeasure
Commonly used passwords leaked from Adobe Top 100 will be released - GIGAZINE

3. Delete unnecessary apps

Four. It is also important to doubt malicious behavior if there is an application with unexpectedly high battery usage or data usage.

Five. Check the applications that are running in the background and check if suspicious apps are running
If you find something you are not familiar with, you may find out the identity by searching the application name on Google.

6. Make suspicious applications completely stop
Tap "Forced Stop" after entering "Settings" → "Application" → "Application Information", it is possible to stop the motion completely.

It is a smartphone that can be said as a "universal tool" anymore, but it is a situation that it is said that privacy is always threatened in exchange for its convenience. You do not have to be frightened at all times, but you always need to keep security in one corner of your head. At the end of the blog Sidor suggests to Google that "I want you to focus more on protecting user privacy."
Related Posts:
in Video, Software, Web Service, Smartphone, Posted by darkhorse_log