A terrifying technology called 'PIXHELL attack' that steals data from LCD monitors using 'sound' has appeared
It has been
New PIXHELL acoustic attack leaks secrets from LCD screen noise
https://www.bleepingcomputer.com/news/security/new-pixhell-acoustic-attack-leaks-secrets-from-lcd-screen-noise/
You can see how the PIXHELL attack works by playing the following movie.
PIXHELL Attack: Leaking Sensitive Information from Air-Gap Computers via 'Singing Pixels' - YouTube
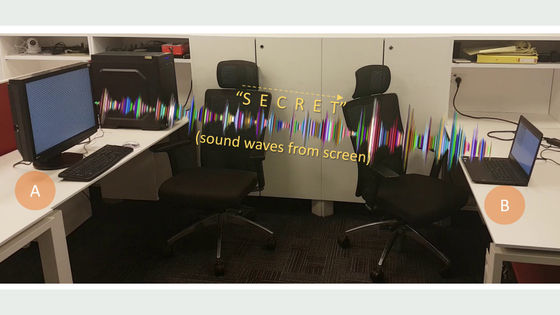
The left PC is air-gapped, meaning it has no internet, Wi-Fi, or Bluetooth connectivity and no speakers. The right PC has a cover over its webcam, so at first glance it doesn't seem like there's any way for the two PCs to exchange information.

Confidential information was transmitted from the PC on the left via 'pixel noise' on the LCD monitor.

To the human eye it just looks like static, so when you look at the display it doesn't look like data is being transmitted.

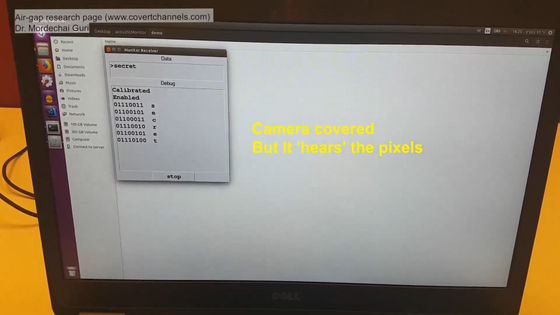
Because the cameraman was standing in front of the receiving PC, it is clear that the image was not captured, but the screen shows that the data 'secret' was captured. This is a PIXHELL attack.
The PIXHELL attack exploits coil whine , a high-pitched sound made by electrical appliances while they are in operation, capacitor noise, or unintended sounds made by monitors due to vibration.
Specifically, the malware first modulates the pixel pattern of the monitor to produce noise with a frequency between 0 and 22 kHz, then transmits a signal encoded within the sound waves, which are then received by a smartphone or other device to exfiltrate data.
The sounds used in PIXHELL attacks are barely audible to humans and the pixel patterns displayed on monitors only need to be low-intensity, making the attack stealthy.
There are three modulation methods: On-Off Keying (OOK), which generates data by switching sound on and off; Frequency Shift Keying (FSK), which switches the frequency; and Amplitude Shift Keying (ASK), which changes the volume.
Below, sounds of 5000Hz, 10000Hz, 15000Hz, and 20000Hz are modulated by a signal generation algorithm and generated as a pattern on the screen.

The PIXHELL attack technology was developed by Mordecai Guri of Ben-Gurion University of the Negev in Israel, who is well-known for his research into techniques for extracting data from air-gapped environments.
In his tests, Guri confirmed that he could exfiltrate data at a speed of 20bps from a distance of up to two meters. This transmission speed is not enough to steal large files, but it is enough to steal text files containing sensitive data such as real-time keystrokes and passwords.
On the other hand, since the PIXHELL attack requires a device equipped with a microphone to pick up sound, it can be thwarted by banning such devices or disrupting them with noise. Guri also proposed detecting attacks by monitoring for abnormal pixel patterns that do not match the normal operation of the system.
Related Posts:
in Free Member, Video, Security, Posted by log1l_ks