Stolen data of a complete offline PC and transfer it to a complete offline mobile phone

ByJohn Watson
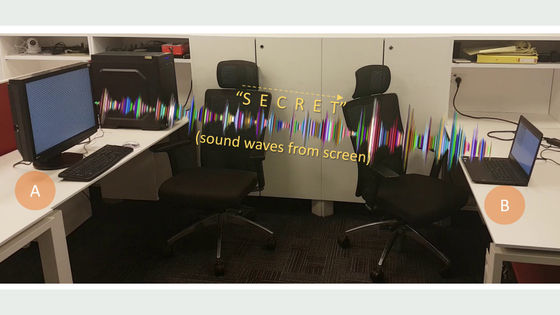
In places dealing with important confidential information, in addition to smartphone carry-on restrictions, measures such as installation of a completely off-line "air gap PC" that does not connect to the net and can not use Wi-Fi / Bluetooth are taken. Although some methods of physically penetrating the environment that was disconnected from the net have been proved, while it is considered that it is still difficult to carry out data from the air gap network, the Israeli Negev-Ben-Glion college Researchers from simple low-end mobile phones with only calling and message functionsGSMIt proved that we can extract air gap PC data through the network.
GSMem: Data Exfiltration from Air-Gapped Computers over GSM Frequencies | USENIX
https://www.usenix.org/conference/usenixsecurity15/technical-sessions/presentation/guri
Where the password actually entered on the air gap PC is displayed on a mobile phone that does not have SIM, camera, Wi-Fi, Bluetooth function, it is contained in the following movie.
GSMem Breaking The Air-Gap - YouTube
On the right side is the main body of the Air Gap PC which can not connect to the network · Internet · Ethernet · Wi-Fi · Bluetooth.

It is attached to the middle wall is network, Internet · Wi-Fi · Bluetooth connection is impossible, SIM card, camera and no data are not included Super simple cell phone. We will demonstrate hacking using these. By the way, Negev-Ben-Glion University, which is studying this method,A method of stealing data by communicating with "heat" of a computerIt has also been demonstrated.

In this method, it is necessary to infect both air gap PC and mobile phone in advance with malware. On a display connected to a PC infected with malware, a window for entering the code is displayed, and when "A 528" is entered by operating the mouse ... ...

"A528" was also displayed on the screen of the next mobile phone. By issuing specific memory related commands at the PC, signals are transmitted at the frequency of the mobile phone,Multichannel archae textureTo amplify the transmission and output data to the next mobile phone through the GSM network.

The effective transmission distance of PC and mobile phone by this method is 1 meter to 5.5 meters, and it has also been demonstrated that if you use a dedicated receiver, you can extend the effective distance to 30 meters.According to WIREDAlthough it is possible to output to the mobile phone only with a small amount of data such as password, it is possible to extract the password and the encryption key in 1 minute to 2 minutes, and even if the attacker does not collect the mobile phone, The possibility of taking data from the neighboring building and nearby parking lot is also considered.
For example, Intel's workers are provided with mobile phones with only telephone and message functions without the camera · Wi-Fi function and can be brought to the work site, but if it is this method data leakage becomes possible It is that.
Related Posts:
in Video, Hardware, Smartphone, Posted by darkhorse_log