A method to steal data from a computer isolated from the net by ultrasonic wave turned out

byChattanooga Public Library
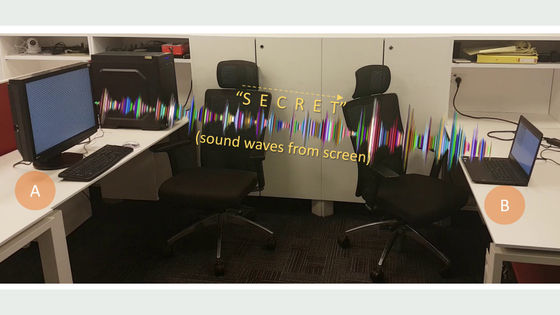
"Air gap computers" that are completely isolated from the network require physical access via USB drives and cables to transfer data, and are considered to be appropriate for storage of important data for security . However, security researchers in Israel announced "a method of stealing data with an ultrasonic wave from an air gap state computer".
MOSQUITO Attack Allows Air-Gapped Computers to Covertly Exchange Data
https://thehackernews.com/2018/03/air-gap-computer-hacking.html
The research team at Ben-Glion University in Israel developed a method to make it usable as an ultrasonic transmitter and receiver by infecting headphones and speakers not equipped with a microphone function with malware. Many microphones and speakers respond to sounds close to ultrasonic waves of 18 kHz to 24 kHz, so they can seem to be able to function as microphones with malware that reverses the hardware listening function and microphone function. The research team explained the method of stealing data via ultrasonic waves announced this time,MOSQUITO (Mosquito)"We name it.
This is a movie released by a research team at Ben Grillon University that actually exchanged data with Mosquito.
MOSQUITO: Jump air-gaps via speaker-to-speaker communication
Two computers in the air gap state are installed. Panda's dot picture is displayed on the display of "computer A" ... ...

Nothing is displayed on "Computer B" display.

A listening device connected to two computers is infected with malware, and it is said that communication is possible by Mosquito.

When the mosquito starts, the picture is gradually displayed on the display of the computer B where the dot picture of the panda is not displayed ......

Panda's dot picture is completed in tens of seconds.

It is the same as the dot picture of the panda displayed on Computer A.

As an attack scenario, it seems that three patterns of "communication between speaker and speaker", "communication between speaker and headphone" and "communication between headphones and headphones" are assumed. The research team says, "In communication between speakers and speakers, we were able to steal data secretly from a distance of up to 9 meters.When communication between headphones communicates, data can be stealed from 3 meters away," Thing.
Also, by using a loudspeaker that is more powerful than a normal speaker, it is possible to communicate at an effective bit rate of 10 to 166 bps from a distance of 8 to 15 meters, and data can be stolen by an air gap state computer There is no prohibition to believe that it is not.
The research team at Ben Grillon University has been studying how to steal data from computers in the air gap state and has previously announced a method of "stealing data using computer heat".
A method of stealing data by communicating with "heat" of a computer

Related Posts: