Malware that extracts data without hearing sound and user not noticing it

ByMarsmet tallahassee
A computer scientist has developed a prototype of malware that can communicate using the sound signal of inaudible sound. From the machine infected with malware, it is possible to securely send the input contents of the keyboard and confidential data, and it is possible to extract the data even if the machine is not connected to the network.
Scientist-developed malware covertly jumps air gaps using inaudible sound | Ars Technica
http://arstechnica.com/security/2013/12/scientist-developed-malware-covertly-jumps-air-gaps-using-inaudible-sound/
In GermanyFraunhofer Institute"Research institutes that invented MP3 compression algorithms" researchers said, "Using microphones and speakers built into a standard computer, send and receive data with small passwords and small capacities from 65 feet (about 20 meters) away I succeeded in doing it. "Journal of CommunicationsWas published inIn a dissertationI made it clear.
An air gap is one type of network security that forms a secure computer network by isolating it from a network that is not guaranteed to be secure, such as a public Internet or a non-guaranteed local area network. However, with this data transfer technology using the audio signal of the inaudible sound, it becomes possible to extract the data from the computer isolated from the network by the air gap.

ByIngo Bernhardt
Using a high-frequency transmission to jump the air gap When a computer is infected with mysterious malware,Security surveyor revealedA few weeks later this paper was published. "The idea of air gaps will be out of date due to the speaker and microphone built into a typical laptop, and the mesh network of sounds secretly made by them," the authors of the thesis Michael Hanspach who is one of. Furthermore, by constructing a mesh-like network made up of sounds with a plurality of terminals infected with malware as connection points, the information can be moved on this network and freely travels from the isolated computer system to the network It will be possible. "
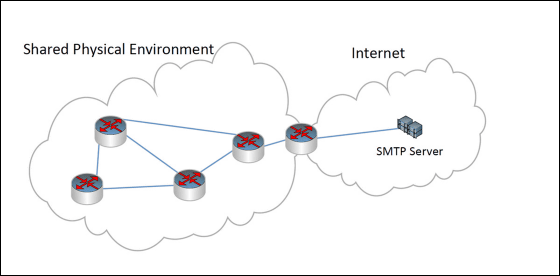
Researchers who have developed this technology have twoLenovo T400It seems that we developed data transfer technology using inaudible sound using only built-in microphone and speaker. The most effective one applied to this technology is a technology called adaptive communication system (ACS) developed for data transfer underwater. This was made in a facility that conducts research on underwater acoustic effects and geophysics in Germany, and the range where data can be sent and received was 19.7 meters. The biggest disadvantage of this is only 20BpsAt this rate, it was almost impossible to exchange movies and large size data at this speed, but by using a special program to transfer only some types of data, the transfer rate of ACS is slow Overcome. Hanspach, one of the developers seems to think that "even small bandwidth may be enough to extract information like a password."
Related Posts:
in Note, Posted by logu_ii







