Amazon Echo can be remodeled as a wiretap

According to MWR InfoSecurity, a security specialist, a design vulnerability has been reported to Amazon Echo version 2015 and 2016, and a malicious attacker gains root authority on the Linux OS and accesses the shell to download malware It is possible to install it. This allows you to convert Amazon Echo into an eavesdropping device without being noticed by users without affecting other Amazon Echo features at all.
Alexa, are you listening?
https://labs.mwrinfosecurity.com/blog/alexa-are-you-listening?
Hackers can turn Amazon Echo into a covert listening device - Help Net Security
https://www.helpnetsecurity.com/2017/08/01/amazon-echo-covert-listening/
How to turn Amazon Echo into an eavesdropping device is as follows. For Amazon Echo there is a debug pad on the bottom of the unit in the following way. First remove the rubber base on the bottom and expose 18 debug pads.
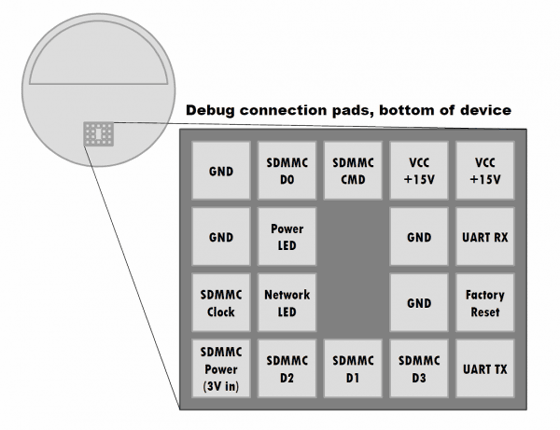
Directly access the firmware and transfer the malware via the SD card. With this method, hackers can gain root privileges without leaving physical evidence and have access to the shell, so you can remodel Amazon Echo as a wiretap device.
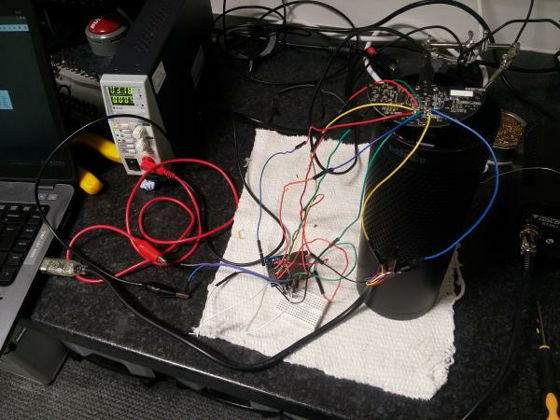
After that, researchers created a script that streams audio picked up by the device to an external server. Embedding this script will not affect Amazon Echo's other functions and it will be possible for the user to steal the contents of the conversation without knowing it. It is possible to choose whether to watch this audio data from the device in the remote environment, to send it through the speaker in the remote environment, or to save it as a WAV file. This vulnerability has been reported on Amazon Echo version 2015 and 2016, but the 2017 version of Echo and Amazon Dot has not been confirmed.

Mark Barnes, a security consultant at MWR InfoSecurity, says, "Routing Amazon Echo itself is trivial, but this is not to say to the manufacturers of devices that use the Internet and what are called" smart home devices " We will ask a lot of questions. " Although there is a major limitation that this vulnerability requires physical access to the terminal, placing the device in an environment where consumer safety or privacy is compromised should be taken for granted Mr. Barnes insists.
On the other hand, it is possible for an attacker to place a terminal under his / her control in the same way as this experiment, but in order to remodel the terminal into a wiretapping device, it is necessary to compile a special code. Also, thinking that it is necessary to do work within a few minutes when there are no people, it seems that it is not an easy task.
Of course Amazon has been trying to minimize the potential attack potential in Amazon Echo's development, but "the debugging pad is not protected" and "You can boot the device via the SD card Hardware setting "can be said to expose consumers to unnecessary risk.
Therefore, MWR InfoSecurity recommends the following three points.
◆ 1: Use the Mute button
For Amazon Echo there is a physical mute button to turn off the microphone, so when talking about delicate information press the mute button.
◆ 2: Observe daily activities
Whether or not the device is vulnerable is unknown from the outside, but you can monitor suspicious activity by monitoring network traffic.
◆ 3: Buy a terminal directly from Amazon or buy from a trusted retailer
Since it is necessary to access the device physically in order to use the vulnerability reported this time, it is better that there is no third party intervention before purchasing as much as possible. Let's remember that there are potential dangers in secondhand goods etc.
In response to MWR InfoSecurity's report, Amazon says, "Customer's trust is very important to us, in principle, Amazon devices should be purchased from Amazon or a trusted retailer to upgrade their defense measures, We recommend that it be up to date. "
Related Posts:
in Hardware, Posted by darkhorse_log