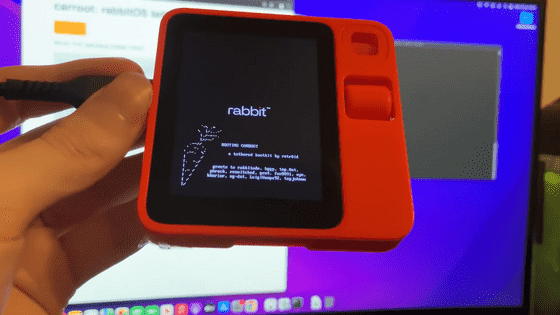
Rabbit, the developer of the AI device 'rabbit r1' that is shaken by security issues, reports that the API key problem was caused by an employee leaking information to a hacker group, and the hacker side points out that the point is being shifted

Rabbitude, a community that jailbreaks and reverse engineers the AI device 'rabbit r1' developed by technology startup Rabbit, has pointed out that 'rabbit r1 has an API key hardcoded in its code base.' In response to this, Rabbit reported that 'in June 2024, an employee leaked the API key to a self-proclaimed
rabbit - penetration test results and security measures to protect data security
https://www.rabbit.tech/newsroom/security-pentest
Rabbit Says Former Employee Handed Hacking Collective the Keys to the R1's Backend
Rabbit Says Breach 'Not Caused by a Breach,' Is Fault of Malicious Employee, 'Hacktivists,' Journalists
https://www.404media.co/rabbit-says-breach-not-caused-by-a-breach-is-fault-of-malicious-employee-hacktivists-journalists/
'Rabbit R1' is an AI device that is advertised as being able to 'order food from delivery services,' 'play your favorite music,' 'send emails,' and more, through its camera and voice input/output functions. However, it has been pointed out that in reality, its functions as an AI assistant are immature, and its internal functions are limited to running the operation automation app 'Playwright.'
Report that the AI device 'rabbit r1' was a fraudulent product that repeatedly said 'That function is in preparation' when purchased - GIGAZINE

Additionally, the reverse engineering community rabbitude pointed out that the API key was hard-coded in the codebase.

When Rabbit investigated these cases, it found that an employee had leaked the API keys to a self-proclaimed hacktivist group, Rabbitude, which had published an article claiming that it had access to the source code and some of the API keys. Rabbit immediately revoked the affected API keys, rotated the API keys, and moved the additional private keys to AWS Secrets Manager.
Following this action, a third-party audit was conducted and it was confirmed that all confidential information stored in the code had been removed.
The company also said that this incident was independent of other incidents and that there was no breach of Rabbit's security systems. Rabbit reports that the API key was obtained and shared illegally and that it is in contact with the authorities. The employee who leaked the information to the hacktivist group has been fired.
In addition, Obscuritylabs, a security company requested by Rabbit to investigate, conducted penetration testing of rabbit r1 from April 29, 2024 to May 10, 2024, and declared that Rabbit and rabbit r1 are completely safe.
Rabbit R1 Penetration Test
https://www.obscuritylabs.com/resources/blog/rabbit_pentest
However, news sites such as 404media and Gizmodo have expressed doubts about Rabbit's report. According to 404media, who contacted rabbitude, Emily, a member of rabbitude, said, 'Rabbit is focusing on where the information was leaked from, but they're missing the point and missing the important issue. These API keys should never have been hardcoded into the rabbit r1 codebase in the first place.'
Eva, also a member of Rabbitude, told Gizmodo that they should not have hard-coded it, even if it was an insider, because that would mean that all employees could access users’ production messages, even if there was no intrusion. She added that the Obscuritylabs study, which found no problems with r1, “isn’t even what you would call a penetration test.”
Related Posts: