When the AI device 'Rabbit R1' was jailbroken, it was discovered that it 'sent user location information without permission' and 'violated open source licenses'
The AI device '
Jailbreaking RabbitOS: Uncovering Secret Logs, and GPL Violations | Blog
https://www.da.vidbuchanan.co.uk/blog/r1-jailbreak.html

The AI device 'Rabbit R1' developed by technology startup Rabbit was expected to be an AI assistant device that could play music and order food just by talking to it, but in reality it only runs Android apps using off-the-shelf APIs, and many users have criticized it for its disappointing functionality and performance.

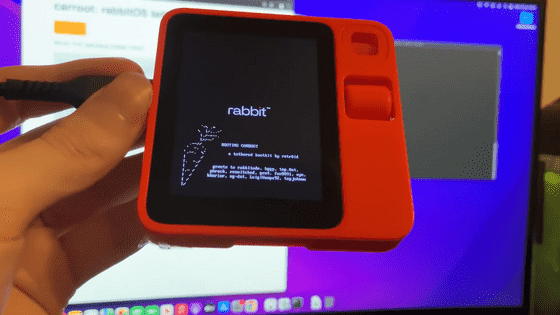
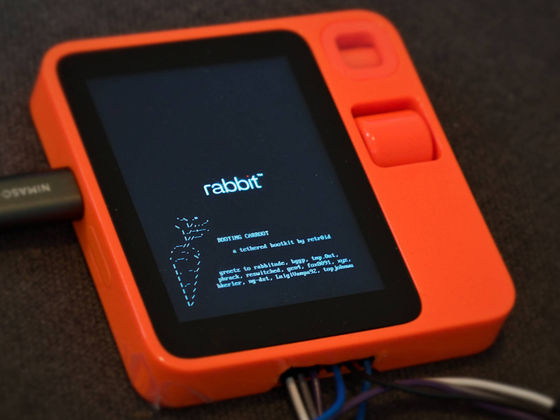
After getting his hands on the Rabbit R1, Buchanan performed a jailbreak that replaces the data on the Rabbit R1 with data he prepared the moment it boots up, and analyzed the operation of RabbitOS. Buchanan has named his jailbreak method ' Carroot ' and has also released a demo video of Carroot in action.
carroot: rabbitOS tethered jailbreak demo - YouTube
When Buchanan actually jailbroken and analyzed RabbitOS, he found that all data logs acquired by RabbitOS were stored in text files in the internal storage.
In addition, the data logs included 'the user's precise location,' 'the name of the Wi-Fi network used by the user,' 'the IDs of nearby cell towers,' 'the user's IP address,' 'a user identification token used by the device to authenticate with Rabbit's backend AIP,' and 'all voice input from the user to the Rabbit R1, along with a text transcript.' According to Buchanan, the location information and cell tower IDs were sent to Rabbit's servers even when no SIM card was inserted.
'There's no need to log this much data,' Buchanan said. 'It's scary to think what Rabbit, on the back end, is using this data for.' 'The Rabbit R1 doesn't have a way for users to reset the device to factory settings, so the logs are being collected in perpetuity. If a Rabbit R1 were to end up on the second-hand market, users' personal information could be exposed to the public.'

In addition, Rabbit has added
Furthermore, Buchanan points out that some of the open source RabbitOS uses closed source drivers. Specifically, closed source drivers for scroll wheel sensing and camera rotation stepper motor control are linked to a kernel image that is open source licensed under the GNU General Public License (GPL). 'Rabbit is violating the GPL license,' Buchanan says.
Buchanan asked Rabbit about the information it had gained from the jailbreak and whether it planned to comply with the GPL license, but as of July 17, 2024, he had not received a response from Rabbit.
It has been discovered that Rabbit R1 has a critical security issue in that the API key is written directly into the source code. It has been pointed out that by using this API key, it is possible to 'view all replies that R1 has ever made to users, including personal information,' 'brick all R1s,' 'change all R1 responses,' and 'change the voice of all R1s.'
AI device 'Rabbit R1' has security issues that could cause user data to leak - GIGAZINE

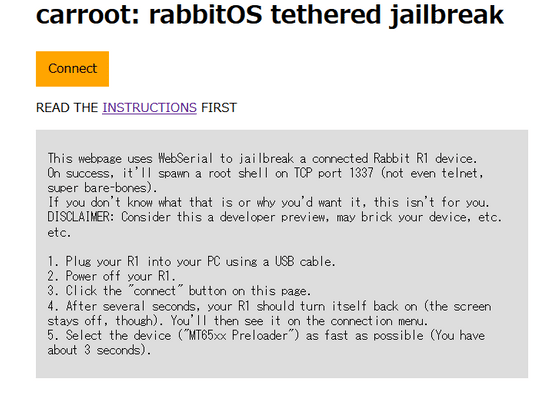
Buchanan has also published a website where you can run Carroot.
carroot: rabbitOS tethered jailbreak
https://retr0.id/stuff/r1_jailbreak/
Related Posts: