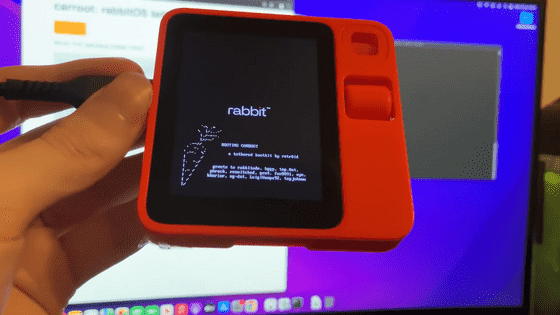
It was discovered that the AI device 'Rabbit R1' has a security problem that causes user data to leak

Researchers reverse-engineering the AI device 'Rabbit R1' have discovered a sensitive API key written directly into the device's code, which could allow unrestricted access to internal data, including users' personal information, the researchers say.
Updates on investigation on r1 SaaS API keys
rabbit failed to properly reset all keys: emails can be sent from rabbit.tech domains
https://rabbitu.de/articles/security-disclosure-2
Researchers Prove Rabbit AI Breach By Sending Email to Us as Admin
https://www.404media.co/researchers-prove-rabbit-ai-breach-by-sending-email-to-us-as-admin/
The Rabbit R1 is an AI device developed by technology startup Rabbit. It was released with much fanfare as a personal assistant device equipped with ChatGPT, but in reality it only runs Android apps using off-the-shelf APIs, and its features and performance have been met with disappointment from users and reviewers.
Report that the AI device 'rabbit r1' was a fraudulent product that repeatedly said 'That function is in preparation' when purchased - GIGAZINE

Additionally, rabbitude, a community working on jailbreaking and reverse engineering R1, announced that they had found critical API keys hard-coded in the R1 codebase.
API keys are highly confidential because they are used by service providers to identify products that use the API and track their usage, so they are generally not hard-coded in source code.
The API keys that rabbitude found belonged to ElevenLabs (for its text-to-speech service), Azure (for its old speech-to-text system), Yelp (for review search), and Google Maps (for location search).
In particular, ElevenLabs' API key gives rabbitude administrator privileges, which means that it is possible to 'view all responses that R1 has ever made to users, including personal information,' 'brick all R1s,' 'change all R1 responses,' and 'change the voices of all R1s.'
A member of rabbitude told foreign media outlet 404 Media, 'A common method of secret management is to insert keys in some form at runtime rather than hard-coding secret keys and values into the code itself. However, interestingly, Rabbit deploys all of its code in containers managed by a system called Kubernetes . Kubernetes natively supports the aforementioned secret management methods, so this should normally be the norm.'

In fact, Rabbitude discovered this issue in May 2024 and
Then, more than a month later, on June 26, Rabbit released a statement saying, 'Yesterday, we were notified that a third party may have accessed our API keys, and we rotated them, which caused a brief downtime for R1. Our team continues to investigate, but at this time we have not confirmed that any of our critical systems or customer data were compromised.'
According to rabbitude, the four API keys mentioned above were actually rotated as announced by Rabbit. However, rabbitude discovered a fifth hard-coded API key, an API key for the email service SendGrid , which could be used to view emails sent from Rabbit's internal email address and send emails from the internal email address.
404 Media has confirmed that rabbitude did indeed receive an email from Rabbit's email address that read, 'Sorry, we've been hacked but we're a bunch of cowards and continue to deny it. From the 1 person Rabbit security team.'
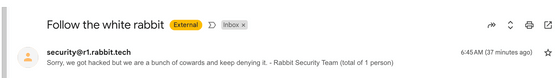
Regarding Rabbit's statement, rabbitude said, 'Frankly, I think the statement is a lie. Sure, we didn't steal any user data, so the statement that 'no customer data was leaked' is true by strict definition, but if we wanted to, we could have accessed things that we shouldn't have.'
Related Posts: