It turned out that there was a DDoS attack on Google Cloud with a maximum of 398 million requests per second with 'HTTP/2 rapid reset attack'
In February 2023, Cloudflare was hit
Google Cloud mitigated largest DDoS attack, peaking above 398 million rps | Google Cloud Blog
https://cloud.google.com/blog/products/identity-security/google-cloud-mitigated-largest-ddos-attack-peaking-above-398-million-rps/
How it works: The novel HTTP/2 'Rapid Reset' DDoS attack | Google Cloud Blog
HTTP/2 Zero-Day Vulnerability Results in Record-Breaking DDoS Attacks
https://blog.cloudflare.com/zero-day-rapid-reset-http2-record-breaking-ddos-attack/
How AWS protects customers from DDoS events | AWS Security Blog
The scale of DDoS attacks has increased rapidly in recent years, with the attack against Cloudflare in June 2022 reaching a maximum of 26 million requests per second , and the attack on Google Cloud in August 2022. The attacks carried out against it expanded to a maximum of 46 million requests per second .
In 2023, DDoS attacks with 71 million requests per second have been reported against Cloudflare.
Cloudflare reports that it has been attacked with 71 million requests per second, the largest scale in history - GIGAZINE

Then, in August 2023, a new attack was carried out, reaching 398 million requests per second at its peak, 7.5 times larger than before. According to Google, the attack lasted two minutes, and its scale was greater than the total number of views on Wikipedia in the month of September 2023.
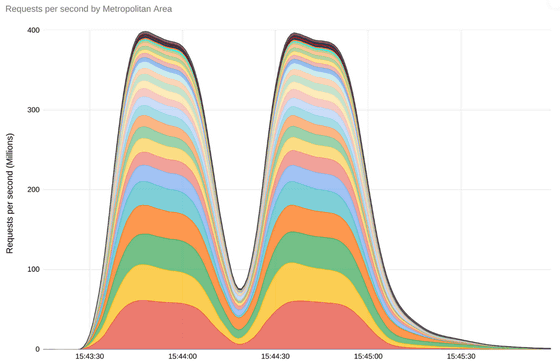
During the same period, Cloudflare observed attacks exceeding 210 million requests per second at its peak, and AWS also observed 155 million requests per second.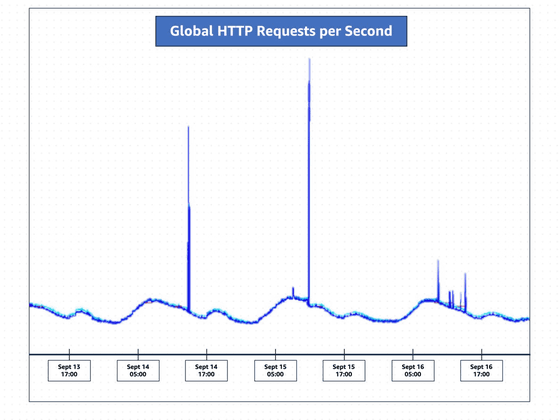
Although Google prevented this attack, since late August, attacks have continued to target infrastructure providers, including Google services, Google Cloud infrastructure, and Google customers.
Google, Cloudflare, and AWS have each confirmed that a large-scale attack has occurred, and that the attack is being carried out by exploiting some features of
NVD - CVE-2023-44487
https://nvd.nist.gov/vuln/detail/CVE-2023-44487
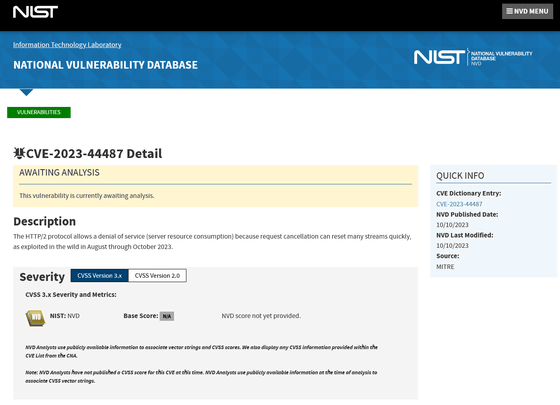
This attack is described as an ' HTTP/2 rapid reset attack .'
The HTTP/2 protocol allows a client to explicitly indicate to the server that the previous stream should be canceled by sending an 'RST_STREAM' frame. At this time, the server and client do not need to coordinate cancellation, and the client can cancel unilaterally. If the server receives an 'RST_STREAM' frame, the client expects the cancellation to take effect immediately, before any other data is processed.
Therefore, an 'HTTP/2 rapid reset attack' opens multiple streams from an endpoint, immediately cancels the stream without waiting for a response from the server or proxy, and then opens the stream again. Because the stream is canceled immediately, the attacker can continue sending requests without exceeding the number of concurrent open streams.
In addition, HAProxy, an open source software that operates as a load balancer and proxy server, has already addressed the vulnerability using code developed in version 1.9 released in 2018, and has revealed that it will not be affected.
HAProxy is not affected by the HTTP/2 Rapid Reset Attack (CVE-2023-44487)
https://www.haproxy.com/blog/haproxy-is-not-affected-by-the-http-2-rapid-reset-attack-cve-2023-44487
He also explained that the web server system NGINX has a default setting of 128 concurrent streams and 1000 HTTP keepalives for performance and resource consumption reasons, and that there will be no problems if you operate with these values. I am.
HTTP/2 Rapid Reset Attack Impacting NGINX Products - NGINX
https://www.nginx.com/blog/http-2-rapid-reset-attack-impacting-f5-nginx-products/
Related Posts:
in Security, Posted by logc_nt