Cloudflare successfully mitigates 26 million DDoS attacks per second

On June 14, 2022, Cloudflare, a cloud service provider, detected and mitigated 26 million
Cloudflare mitigates 26 million request per second DDoS attack
https://blog.cloudflare.com/26m-rps-ddos/
According to Cloudflare, the attack detected this time targeted the websites of customers using Cloudflare's free plan. Like the massive DDoS attacks that occurred in April 2022, many of these attacks came from cloud service providers rather than home Internet service providers, with hijacked virtual machines and powerful servers. It is said that it has been shown to have been used in the attack.
The 26 million attacks per second originated from a powerful botnet consisting of 5067 devices, and each node was making about 5200 attacks per second during peak hours.
Looking at the time axis, we can see that the number of attacks increased sharply in just a few seconds after 22:26:30 on the day of the attack.
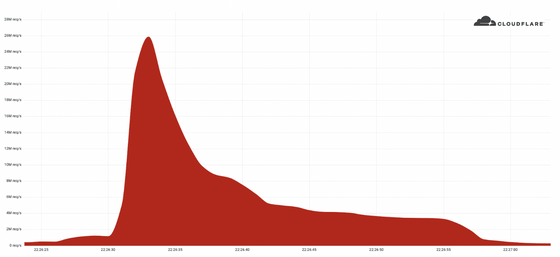
As a result of conducting experiments using a botnet composed of more than 730,000 devices by Cloudflare, the botnet used in the experiment could not generate more than 1 million requests per second, and the average number of requests per device Was only about 1.3 times per second. From this result, Cloudflare points out that the attacker who executed the DDoS attack detected this time built a botnet that was 4000 times stronger than the botnet used in the experiment.
It is also noteworthy that this attack was carried out via HTTPS. HTTPS DDoS attacks are expensive to establish a secure TLS encrypted connection, which means that it costs more for the attacker to launch the attack and for the victim to mitigate the attack. .. Cloudflare said, 'There have been very large-scale attacks using HTTP in the past, but since this attack uses HTTPS, it stands out in terms of the amount of resources required for the attack.' Said.
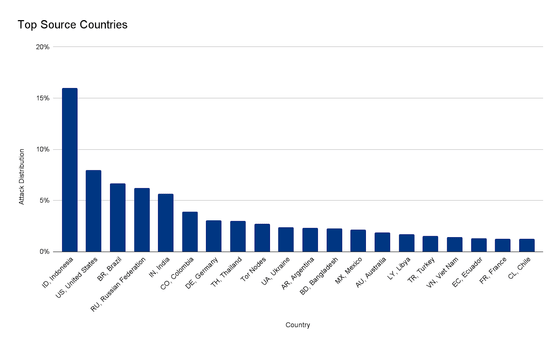
In addition, the botnet that caused the DDoS attack generated more than 212 million HTTPS requests from more than 1500 networks in 121 countries within 30 seconds. The top countries were Indonesia, the United States, Brazil and Russia. Also, about 3% of the attacks were done via the Tor node.
Looking back over the past year,
Cloudflare says, 'Most attacks are small, such as cyber vandalism, but even small ones can have a serious impact on the unprotected Internet. On the other hand, large attacks do. It's growing in size and frequency, but it's still short and fast. Attackers are trying to concentrate the power of the botnet to exert its one-shot deadly destructive power and evade detection. Attack detection It is recommended to protect Internet assets with an automated, always-on protection service that does not rely on humans for mitigation. '

Related Posts:
in Web Service, Security, Posted by log1p_kr







