It turned out that AWS was under 2.3 Tbps DDoS attack

by
Protecting Amazon's Cloud Services From DDoS Attacks A report released by AWS Shield found that AWS was under the largest DDoS attack ever.
AWS Shield Threat Landscape Report – Q1 2020
(PDF file) https://aws-shield-tlr.s3.amazonaws.com/2020-Q1_AWS_Shield_TLR.pdf
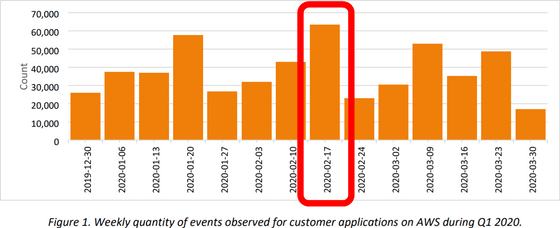
The following is a weekly graph of the number of events observed on AWS during the first quarter of 2020. Looking at the part surrounded by the red frame, you can see that the week of February 17, 2020 has a particularly large amount of events compared to other periods.
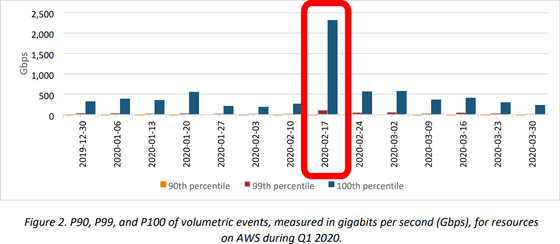
There are various types of such events, but according to AWS, most large-scale events are caused by DDoS attacks. These attacks are intensifying, and none of the attacks observed on AWS between December 2018 and April 2019 exceeded 1
The graph below shows this best. This graph shows the 90th percentile , 99th percentile, and 100th percentile (all events) of the maximum weekly event amount observed by AWS in the first quarter of 2020 with orange, brown, and dark blue bar charts, respectively. Looking at the red frame, you can see that an event exceeding 2000 Gbps (2 Tbps) has occurred on February 17, 2020. According to the report, the event that occurred at this time was 2.3Tbps, far exceeding the 1.3Tbps recorded in the February 2018 attack on GitHub , which was the largest DDoS attack to date.
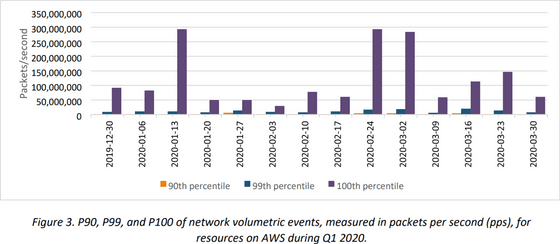
Most of these DDoS attacks were
SYN flood attacks use very small packets, which makes them difficult to absorb. The following is a graph showing the weekly event amount observed by AWS in the first quarter of 2020, in packets per second. Large-scale SYN flood attacks were carried out in the week of February 24, which is close to the time when large-scale DDoS attacks were performed, and in mid-January and early March.
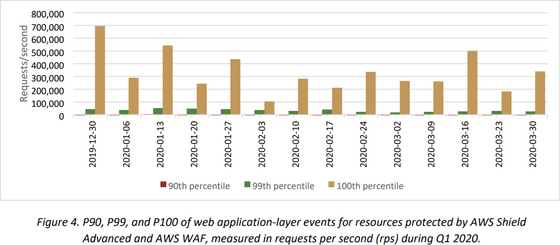
The behaviors that differ from these attack methods are application layer attacks such as HTTP reflection attacks and web request flood attacks. Below is a table showing the number of requests per second for application layer events protected by
In order to protect its services from these attacks, AWS said in a report, 'Reduce the attack surface by limiting access to applications unless necessary, such as providing services to authorized end users.' Up-to-date and follow vendor best practices' 'Do not allow remote access to hosts unnecessarily, manage remote access by using Bastion hosts , etc.' 'AWS Shield Advanced, AWS Firewall Manager , Amazon We recommend that you take measures such as utilizing services such as CloudFront and Amazon GuardDuty to protect your system from attacks.'
Related Posts:
in Web Service, Security, Posted by log1l_ks