A method will be developed to locate the AWS account ID of any S3 bucket, including private ones.
Sam Cox, CTO of the security company ``Tracebit,'' has disclosed a method to find out account IDs from bucket names in S3, an AWS storage service, regardless of whether they are public or private.
How to find the AWS Account ID of any S3 Bucket
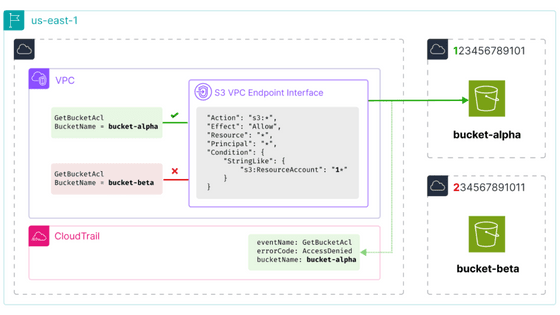
The key to Mr. Cox's method is to apply the VPC endpoint policy by using S3's VPC endpoint. By allowing the policy based on the account ID, such as 'Allow only if the account ID starts with 1', check whether or not denial occurs at the policy level.

The specific method is as follows.
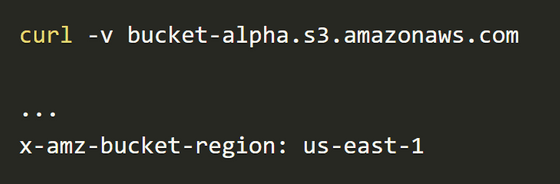
First, check the region of your target bucket. When accessing with curl etc., the region is listed in the 'x-amz-bucket-region' header.
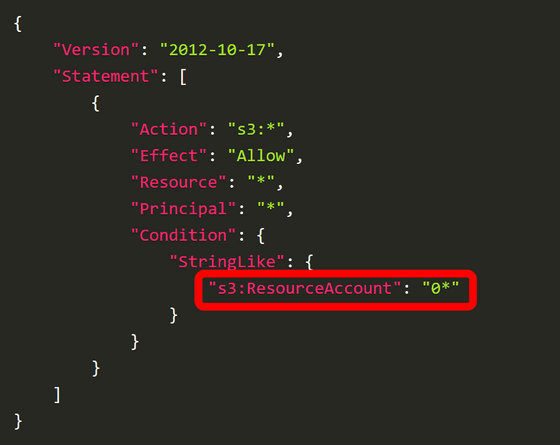
Next, create a VPC and VPC endpoint in the same region as the target, and set 's3:ResourceAccount' in the VPC endpoint policy as shown below. By setting it to '0*', communication is allowed only if the account ID starts with 0.
Create an EC2 instance and access the target bucket via the VPC endpoint. Of course, access will be denied, but if you are passing through the VPC endpoint at that time, a log like the one shown below will remain in CloudTrail.
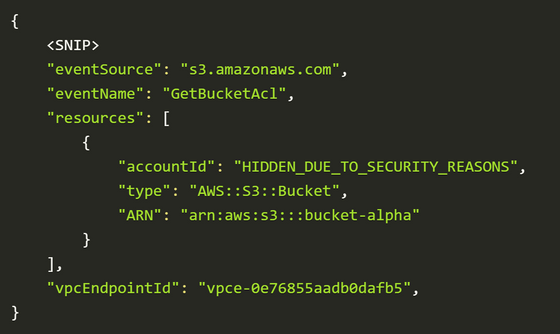
If you don't see any logs in CloudTrail after waiting about 10 minutes, you know that the first character of your account ID is not 0 because access is denied at the VPC endpoint level. In this case, it is OK to check whether the first character of the account ID is 1 or not, like '1*'.
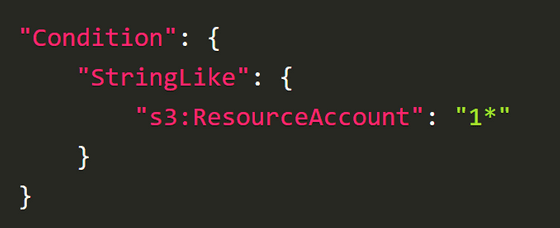
On the other hand, if the log is displayed in CloudTrail, move on to finding the second digit, such as '00*'.
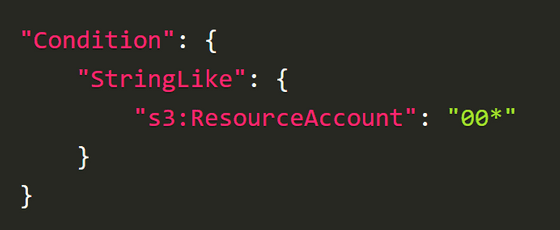
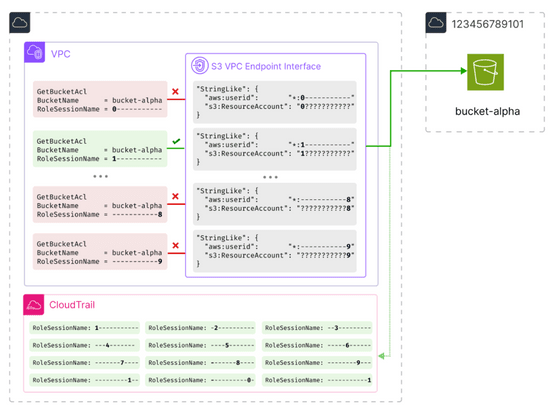
By repeating this process, all of the account IDs will be revealed. In addition, it is stated that it is possible to find the account ID within 10 minutes by setting multiple rules at once, as shown in the figure below, instead of searching for each character one by one.
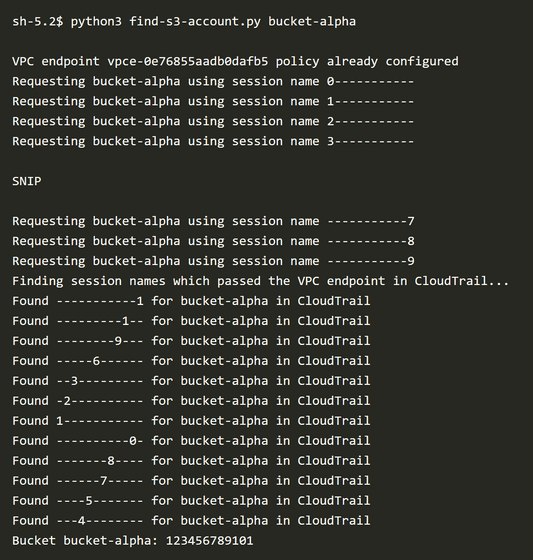
Although the code has not been made public, the actual operation is as shown in the figure below. When you enter the bucket name, you can see that the account ID is output.
There are various opinions on whether or not account IDs are confidential information, and AWS officials do not specifically state that they should be kept confidential, but there is no doubt that security will be higher if they are kept confidential. Cox also said that he consulted with the AWS security team before publishing this blog post.
Related Posts:
in Software, Web Service, Security, Posted by log1d_ts