Vulnerability that can delete arbitrary file on server when editing media file with WordPress, unconditioned in version 4.9.6

by Christine Rondeau
It is pointed out that there is a vulnerability in the popular CMS "WordPress" that an attacker can delete arbitrary files on the server. Although the damage is minor if the image file is deleted, it is also possible to delete the security related file and it may happen that WordPress is reinstalled without permission.
Although this vulnerability has been reported to the WordPress security team in November 2017, patch is not currently applied, and it is said that it is unrevised also in version 4.9.6 which is the latest version.
WARNING: WordPress File Delete to Code Execution
https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/

According to RIPSTECH familiar with PHP security, this vulnerability is based on the premise that an attacker has the authority to edit and delete WordPress media files, so it is necessary to take advantage of account hijacking and another vulnerability in advance It is said that it needs to be promoted.
An attacker who gains necessary privileges can access ".htaccess" that controls access to folders, "index.php" file to prevent file list display in folders, " wp-config.php "and so on can be deleted. In particular, since the last "wp-config.php" contains database authentication information, when it is deleted, the next time you visit the website, it behaves as though WordPress has not been installed yet, WordPress will be reinstalled. When an attacker finishes installing himself as an administrator account, it becomes possible to execute arbitrary code on the server.
On the RIPSTECH site, you can see a demonstration video that actually deletes "wp-config.php" from the edit / delete screen of the media file.
First of all, video starts from logging in to WordPress. The attacker's account can already edit / delete media files.
I will add a new media file
The "logo.png" file you choose is a file of no discrimination.
However, it is a problem from where you can prepare for adding files. Open development tools ......
Confirm the input information to the upload form
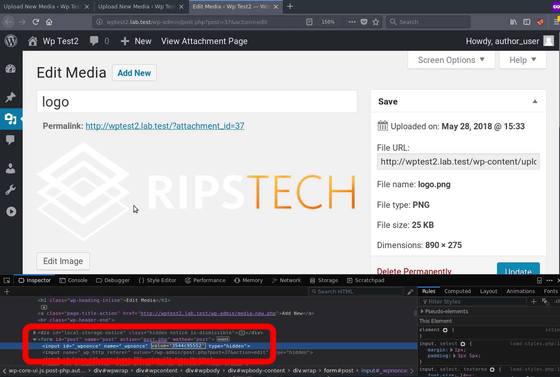
Rewrite the value manually ...
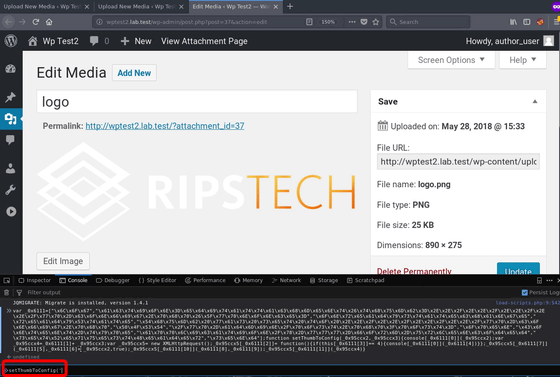
Set the thumbnail to "wp-config.php"
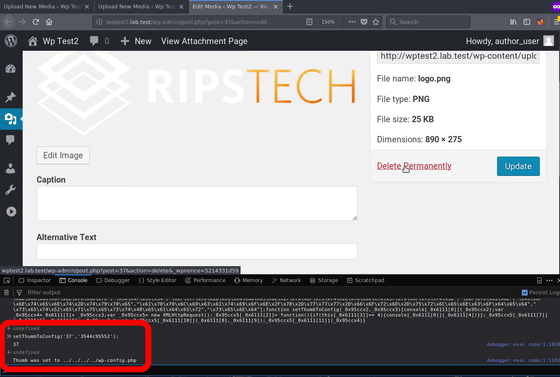
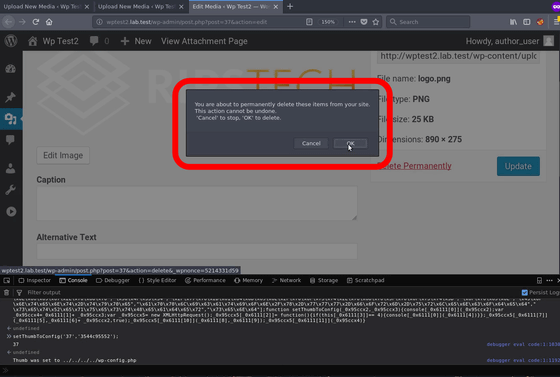
And we will try to delete this file. A common message when deleting WordPress files, "Delete can not be canceled" is displayed.
Ignoring deleting the file, the screen for selecting the language appears. This is the screen you see when installing WordPress ......
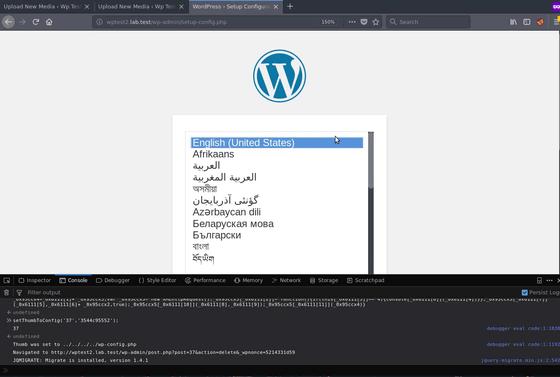
Selecting a language displays the initial screen called "Welcome to WordPress". After all, it returns to the "not installed" state.
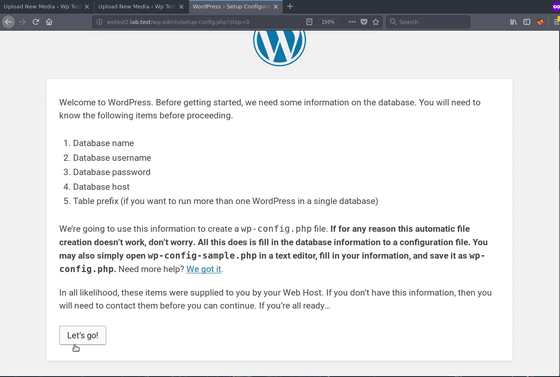
The attacker can do reinstallation with this.
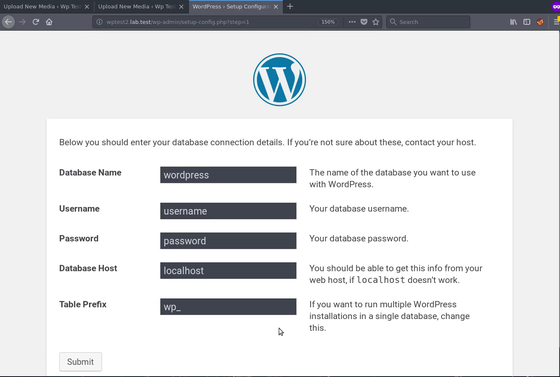
As of 20th November 2017, the vulnerability has been reported from Hackerone on the bug reporting platform to the WordPress security team, but the security team inquired about patch release from RIPSTECH without talking with Hackerone no reaction. In May 2018, though DM was sent on Twitter considering the possibility of overlooking the message at Hackerone, as it was still unresponsive, after seven months have elapsed from the report, it is said that the information has been released about.
In WordPress, in February 2017, site vulnerability was exploited by site tampering damage, and it was fixed in version 4.7.2.
About vulnerability countermeasure of WordPress: IPA Independent Administrative Institution Information Processing Promotion Agency
https://www.ipa.go.jp/security/ciadr/vul/20170206-wordpress.html
Related Posts:
in Security, Posted by logc_nt