``GPU.zip'' attack steals visual data from Apple, Intel, AMD, NVIDIA, Qualcomm, and Arm GPUs and reads personal information displayed on websites
Researchers at the University of Texas at Austin announced that they have discovered an attack called GPU.zip that targets GPUs from six major suppliers, including Apple, Intel, AMD, NVIDIA, Qualcomm, and Arm. This attack allows malicious websites to read visual data of personal information such as usernames and passwords displayed on other websites.
GPU.zip

GPU.zip: On the Side-Channel Implications of Hardware-Based Graphical Data Compression
(PDF file) https://www.hertzbleed.com/gpu.zip/GPU-zip.pdf

GPUs from all major suppliers are vulnerable to new pixel-stealing attack | Ars Technica
https://arstechnica.com/security/2023/09/gpus-from-all-major-suppliers-are-vulnerable-to-new-pixel-stealing-attack/
iframes are used as HTML elements that allow you to embed advertisements, images, and other content hosted on other websites. GPU.zip is an attack carried out by placing a link to the web page you want to read within this iframe, but browsers have introduced the ' same origin policy ' as part of security regarding resource handling, and originally this same Origin policies do not allow either site to inspect the other site's source code or content.
However, the research team found that a side-channel attack is possible that extracts and steals visual data from the data compression used by the internal GPU to improve performance. Security concerns with iframes have been known for over a decade, and most sites restrict requests for cross-origin resource sharing on pages that display usernames, passwords, or other sensitive content. However, Wikipedia is not restricted on some sites, such as displaying the user name of the logged in user.
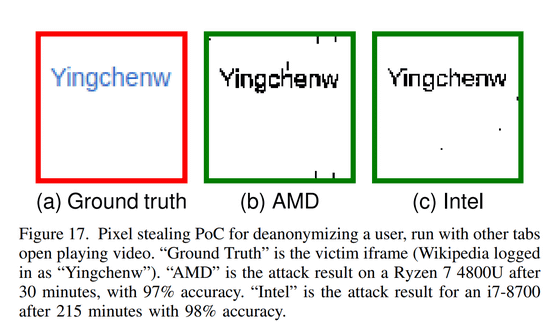
In the proof of concept conducted by the research team, an experiment was conducted to steal the usernames of Wikipedia users. In the image below, (a) is the name logged in to Wikipedia, (b) is the character reproduced with the built-in GPU of AMD Ryzen 7 4800U, and (c) is the character reproduced with the built-in GPU of Intel Core i7-8700. The research team reported that an AMD Ryzen 7 4800U had a 30-minute attack with 97% accuracy, and an Intel Core i7-8700 had a 215-minute attack with 98% accuracy. According to the research team, it was possible to reproduce GPU.zip with Apple, Intel, AMD, NVIDIA, Qualcomm, and Arm GPUs.
GPU.zip runs in three stages: ``Allow cross-origin resource sharing on the iframe and load cookies'' ``Allow SVG filters to be rendered on the iframe'' ``Delegating rendering tasks to the GPU'' . Therefore, GPU.zip runs in browsers with Chromium engine such as Chrome or Edge, but cannot run in browsers with other rendering engines such as Firefox or Safari.
'Data compression is done to save memory bandwidth and improve browser performance,' said Wang Yingchen, a researcher at the University of Texas at Austin. 'This can be exploited to perform side-channel attacks that steal visual information.'
The research team has published the proof of concept source code on GitHub. The research team has released the survey results and proof of concept source code to Apple, Intel, AMD, Nvidia, Arm, Qualcomm, and Google in March 2023, but as of September 2023, GPU vendors will not be able to apply the fix. Google has not decided whether or how to fix the problem.
GitHub - UT-Security/gpu-zip
https://github.com/UT-Security/gpu-zip

When IT news site ArsTechnica spoke to Google, Google said, ``We are communicating with and proactively working with the researchers reporting the reports. We are always working to further improve protection for Chrome users.'' 'We aim to do so,' he said, but declined to say whether it would change Chrome's behavior. Intel also stated, ``We have determined that the root cause lies in third-party software, not the GPU.'' This issue is browser-influenced and can be resolved with a browser update, so it is not included in our threat list. 'There are no plans to make any changes.'
Related Posts: