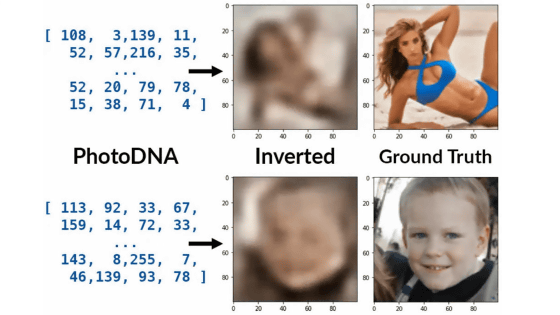
Technology ``Tree-Ring Watermarks'' that embeds digital watermarks in images output by image generation AI such as Stable Diffusion and enables tracking is proposed

When you hear the phrase “add watermarks to images,” many people may think that they are intended to prevent reprinting and misuse of content
[2305.20030] Tree-Ring Watermarks: Fingerprints for Diffusion Images that are Invisible and Robust
https://arxiv.org/abs/2305.20030
GitHub - YuxinWenRick/tree-ring-watermark
https://github.com/YuxinWenRick/tree-ring-watermark
In recent years, high-quality image generation AI such as Stable Diffusion and Midjourney have appeared one after another, making it possible for anyone to easily generate a wide variety of images from text. At the same time, the problem was that 'it has become easier for someone to maliciously generate fake images and deceive people.' Of course, it is possible to create sophisticated fake images with conventional image processing software, but the emergence of tools that can generate images simply by entering text has greatly lowered the hurdle.
In order to deal with this problem, a mechanism has been proposed to ``add a digital watermark to the image generated by AI to make it identifiable''. A digital watermark is a mark that can be detected by performing a special operation that is invisible to humans, and helps to identify that 'this image was generated by AI'. If a robust system for watermarking AI-generated images is built and spread, social media, news organizations, and AI platforms will be able to identify the source of the images, reduce the damage caused by fake images, and provide information to law enforcement agencies. It will be possible.

Conventional digital watermarking generally involves adding watermarks after the files have been output. In response, Wen et al.'s research team devised a method called `` Tree-Ring Watermarks '' that incorporates a digital watermark system into the process itself in which AI generates images.
Image generation AI such as Stable Diffusion, which uses
Detailed illustration of how the image generation AI 'Stable Diffusion' generates images from text - GIGAZINE

Tree-Ring Watermarks incorporates a 'key', which is a pattern constructed based on Fourier transform , into an array of random noise, which is the initial value, in this image generation process. This key remains as a potential minor layout change even after the standard generation process transforms the random noise into a clean image, but still distinguishes it from other random generated images even when checked by a human. He said he can't.
However, by reversing the image with embedded keys through a diffusion model to recover the original random noise, it is possible to see if the keys are present. The research team says that the key is a pattern engraved in Fourier space, so it is much more robust than existing methods for editing such as trimming, changing colors, flipping, rotating, and adding noise.
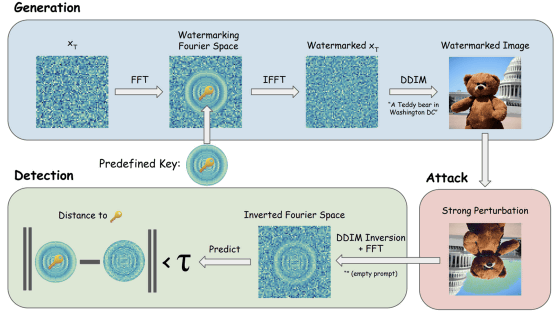
In fact, the research team conducted a validation test using Tree-Ring Watermarks and found that the effect on the image quality score was negligible, high robustness to conversion, low false positive rate in detection, etc. It was confirmed.
For digital watermarks to be added to digital content, it is necessary to ensure that the general user does not notice it, that it is not lost even if a malicious person processes the file, and that it can be detected with high accuracy even if the file has been processed. What you can do' etc. The Tree-Ring Watermarks meet these requirements, and the research team hopes to help track the origin of AI-generated images.
It is not necessary to create a new image generation AI to implement Tree-Ring Watermarks, and it can be incorporated into existing image generation AI through API. Since the parameters of the AI model are required to perform the inversion process of the diffusion model, it seems that only the owner of the AI model can be verified by design.
According to social news site Hacker News, ``If you can trace something from your service, it's useful. If you can stuff it with metadata like prompts and the identity of the user who generated it, it can help you switch from child sexual abuse content to political disinformation. It will be a powerful tool that can compete with anything up to ” .
Tree-Ring Watermark: Invisible Robust Fingerprints of Diffusion Images | Hacker News
https://news.ycombinator.com/item?id=36426136
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik