It was discovered that the Windows source code was for sale for 62 million yen

A large-scale cyber attack on the network monitoring software 'Orion Platform' that occurred in December 2020 caused enormous damage to many organizations such as US government agencies and large corporations. In addition, a site called SolarLeaks, which claims to sell data stolen in this cyberattack, has emerged, claiming to provide source code for Orion and Microsoft Windows.
solarleaks.net/
SolarLeaks site claims to sell data stolen in SolarWinds attacks
https://www.bleepingcomputer.com/news/security/solarleaks-site-claims-to-sell-data-stolen-in-solarwinds-attacks/
In December 2020, a cyber attack occurred in which a Trojan horse was mixed in the update file of the network monitoring software 'Orion Platform' of security company SolarWinds . The victim Microsoft was forced to work with other companies to seize domains related to cyber attacks. Microsoft President Brad Smith describes the attack as 'one of the most serious cyberattacks in the last decade.'
What is the attack on SolarWinds' Orion Platform, which Microsoft president says is 'one of the most serious cyberattacks in the last decade?' --GIGAZINE

News site Bleeping Computer reported on January 12, 2021 that 'SolarLeaks, a site that claims to sell data stolen in an attack on SolarWinds, was released today.'
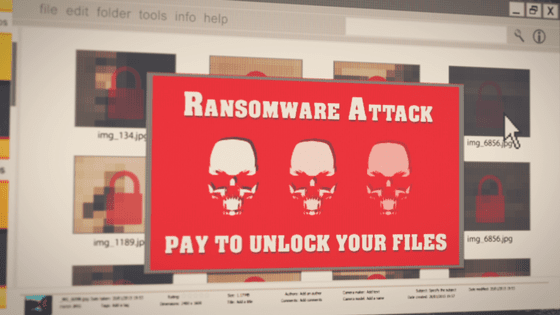
The result of actually accessing the Solar Leaks site is as follows. A simple text message that begins with the 'Happy new year!' Greeting states, 'We are selling the data we found in our recent adventures.' Also, some of the Windows source code and Microsoft repositories were priced at $ 600,000.
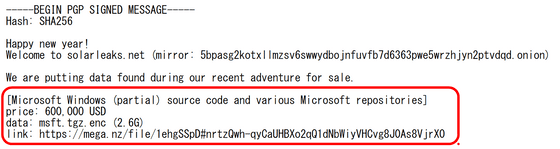
When I accessed the URL of the cloud storage site posted as a link to the Windows source code, the screen asking for the decryption key was displayed as shown below. It seems that SolarLeaks' aim is to get money in exchange for this decryption key.
Microsoft
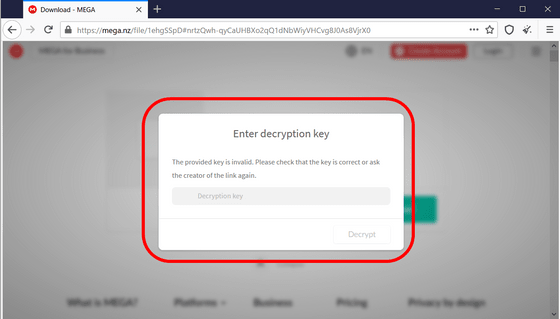
In SolarLeaks, other network equipment giant received a similar damage and Microsoft's Windows Cisco and is a development company of Orion that was used to attack SolarWinds, a prominent security company FireEye has source code and data are sold. At the end, you will also find the email address used to contact Solar Leaks.
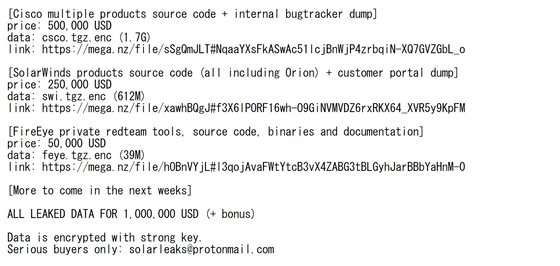
However, when Bleeping Computer actually tried to send an email to this email address, I got a message that the email address didn't exist.
According to Ricky Jubert, the founder and security researcher of
The domain is 1 day old and registered through NJALLA. Njalla is a preferred registrar from Fancy Bear and Cozy Bear. This alone already shows the people behind this website have at least a little knowledge about Russian MO.
— Rickey Gevers (@UID_) January 12, 2021
Investigations to date have shown that the attack on SolarWinds involved a group of hackers suspected of being backed by a Russian government agency, UCN2452.
Hacker group 'UCN2452' that intercepted confidential information of government agencies and companies around the world revealed the method --GIGAZINE

Also, when Bleeping Computer searched for Solar Leaks on WHOIS , a service that queries domain owners, it found a mocking name for someone who searched for 'You Can Get No Info.' The attached server is displayed.

About SolarLeaks, Bleeping Computer said, 'We haven't confirmed if this site is genuine or if the site owners actually have the data they sell.'
Jake Williams, founder of security firm Rendition Infosec , said on Twitter: 'SolarLeaks data is commercially attractive but not of intelligence value. The Ministry of Finance, the Ministry of Commerce, etc. The fact that government data is not provided suggests that this may be due to a genuine group, 'he said. He said that the possibility of counterfeiting is small because he is devoted to earning profits.
One more thought about #solarLeaks : the alleged sale is only for things are commercially interesting, not data of intelligence value. The fact that no intelligence data (Treasury, Commerce, etc.) was offered for suggests this could be the real group. 1 / 3
— Jake Williams (@MalwareJake) January 12, 2021
( https://t.co/vCaZOBsT9G )
Bleeping Computer has contacted Microsoft to check if it knows the existence of SolarLeaks and if the data is leaked as SolarLeaks claims, but at the time of writing the article, no response was obtained. That is.
Related Posts: