Pointed out that GitHub's cloud development environment 'Codespace' can be exploited as a malware distribution server

Security company
Abusing a GitHub Codespaces Feature For Malware Delivery
https://www.trendmicro.com/en_us/research/23/a/abusing-github-codespaces-for-malware-delivery.html
How attackers might use GitHub Codespaces to hide malware delivery | CSO Online
https://www.csoonline.com/article/3685419/how-attackers-might-use-github-codespaces-to-hide-malware-delivery.html
Hackers can use GitHub Codespaces to host and deliver malware
https://www.bleepingcomputer.com/news/security/hackers-can-use-github-codespaces-to-host-and-deliver-malware/
Codespaces is a tool that allows you to create and test applications in development containers running on the GitHub server. Since its general availability in November 2022, Codespaces has gained popularity among developers who prefer a preconfigured container-based environment with the tools and dependencies they need for development.
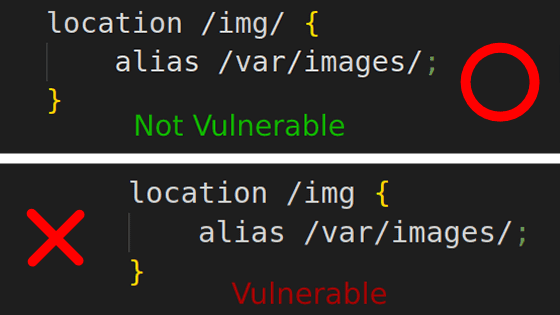
Codespaces allows external users to test and showcase code under development. To do that, you need to do port forwarding in Codespaces and generate a URL to access the code you are developing. This port forwarding setting can be configured as private or public. When set to private, authentication in the form of a token or cookie is required to access the URL, while when set to public, authentication is required. , the code is accessible to anyone who knows the URL.
The port forwarding settings in Codespaces are as follows and can be set to 'Private' and 'Public'.
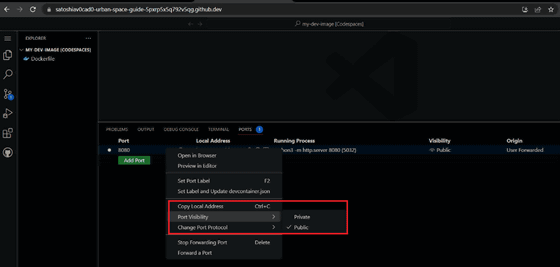
By using this feature, developers can flexibly demonstrate code, but Trend Micro can abuse this to turn Codespaces into a server for hosting malware. I point out that it is possible.
Users can use the
Below is an image showing how to host malware using Codespaces.
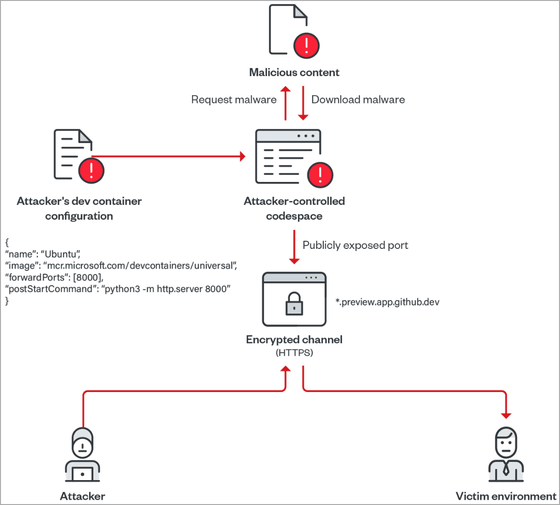
If this method is used, the victim of the attack will download malware from a domain owned by GitHub, a reliable service, so the possibility of malware being detected by the
Trend Micro points out that exploiting cloud service providers to host malware is not new. However, compared to other cloud service providers such as Amazon Web Services, Microsoft Azure, and Google Cloud Platform, the cost barrier to exploiting GitHub's Codespaces is 'low'.
Technology media BleepingComputer reports, 'I touched Codespaces for the first time, but I was able to create a'malicious web server'in less than 10 minutes.'
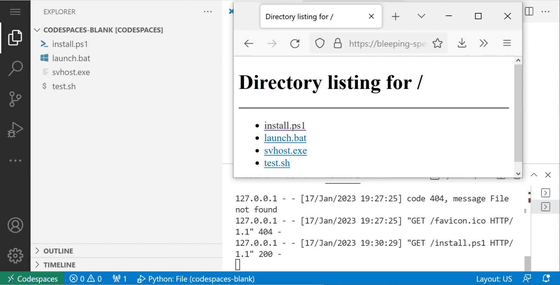
GitHub policy automatically deletes inactive Codespaces after 30 days, allowing attackers to use the same URL for a month. At the time of writing the article, no cases of Codespaces abuse have been confirmed, but Trend Micro emphasizes the possibility of malicious attacks using this technique.
Related Posts:
in Web Service, Security, Posted by logu_ii